to their office computer and files. It also allows IT professionals to provide remote support and troubleshooting for computers on a network. Additionally, RDP can be used for virtual meetings and collaboration, as multiple users can access the same computer remotely. Overall, RDP offers convenience and flexibility for remote access and management of devices and networks.
Is RDP and VPN same
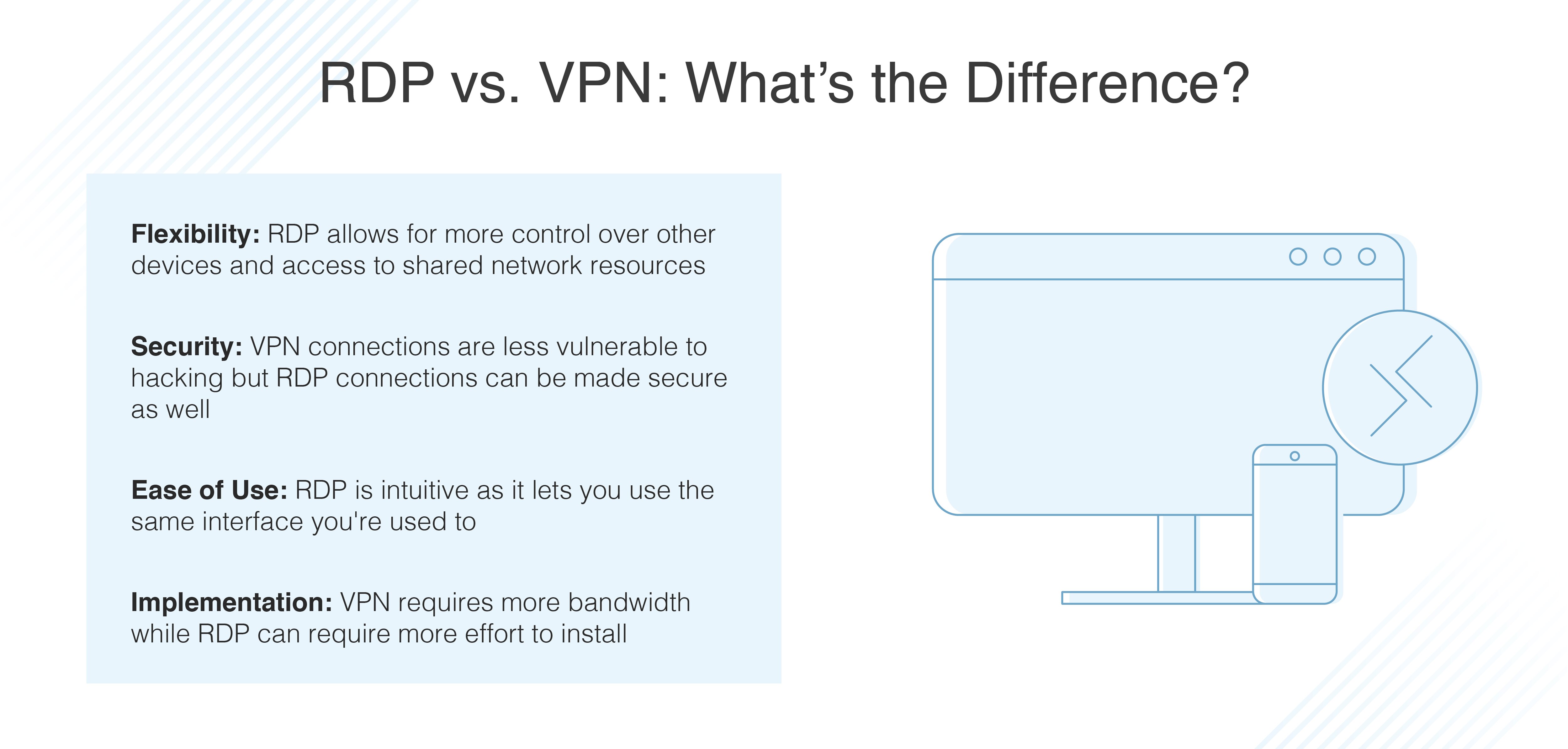
While VPN and RDP share similar features, there is a clear difference between them. RDP provides remote access to a computer or device, whereas a VPN allows access to secure networks. This comparison of VPN vs. RDP (Remote Desktop Protocol) will tell you which one is right for you.
Cached
What is the advantage of RDP over VPN
Unlike VPN, RDP typically enables users to access applications and files on any device, at any time, over any type of connection. The biggest advantage of RDP is that you have access to network resources, databases, and line-of-business software applications without the limitations and high bandwidth demands of VPN.
Cached
Do you need VPN with RDP
While you don't need a VPN to access or use remote desktops, it is highly recommended that you secure connections between any of your devices and the networks they connect to.
Can RDP and VPN be used together
Access can be first restricted by ensuring Remote Desktop is used behind a secure virtual private network (VPN). Then two-factor authentication (2FA) that is compatible with RDP and VPN should be implemented to augment traditional password authentication.
How safe is RDP over internet
Is RDP secure Remote Desktop Protocol is designed to enable authorized users to access data and remote systems. However, RDP security is not infallible. There are certain vulnerabilities inherent to using RDP that threat actors can potentially exploit to gain unauthorized access.
What does RDP stand for
Remote Desktop Protocol
This article describes the Remote Desktop Protocol (RDP) that's used for communication between the Terminal Server and the Terminal Server Client.
What is the disadvantage of RDP
No Administrative Access – In the event that simply having a Remote Desktop Protocol account is your objective, you are up the creek without a paddle with getting administrative privileges. The best way to get that going is to get a Remote Desktop Protocol server all things being equal.
Why would you use RDP
It enables network administrators to remotely diagnose problems that individual users encounter and gives users remote access to their physical work desktop computers. RDP can be used by employees working from home or traveling who need access to their work computers.
Why you should disable RDP
Introduction. It is always advisable to reduce security risks by disable unnecessary services. These instructions disable Remote Desktop Protocol (RDP) service, which is commonly leveraged by adversaries to attack Windows computers, such as the RDP Exploit BlueKeep.
How safe is RDP over Internet
Is RDP secure Remote Desktop Protocol is designed to enable authorized users to access data and remote systems. However, RDP security is not infallible. There are certain vulnerabilities inherent to using RDP that threat actors can potentially exploit to gain unauthorized access.
Can you be tracked through RDP
1) Can Remote Desktop (RDP) Be Monitored Yes. Using CurrentWare's remote desktop monitoring software you can monitor the computer activities of your end-users. This includes logon/logoff events, internet history, and application usage.
How do hackers use RDP
Once an attacker infiltrates an RDP server, they can then sell access to the device on an illicit marketplace instead of controlling and exploiting the device themselves. This is a popular way through which malicious parties access devices via RDP.
Why do people use RDP
It enables network administrators to remotely diagnose problems that individual users encounter and gives users remote access to their physical work desktop computers. RDP can be used by employees working from home or traveling who need access to their work computers.
What are the two types of RDP
There are two major categories of remote desktop software: operating-system-based and third-party solutions.
Why do hackers use RDP
Hackers use RDP to gain access to the host computer or network and then install ransomware on the system. Once installed, regular users lose access to their devices, data, and the larger network until payment is made.
How can you tell if someone is using RDP
Click the Tools tab. In the Windows Tools section, click Remote Control. Click. against the name of a computer to view its remote-control history.
Is it safe to use RDP over the Internet
Is RDP secure Remote Desktop Protocol is designed to enable authorized users to access data and remote systems. However, RDP security is not infallible. There are certain vulnerabilities inherent to using RDP that threat actors can potentially exploit to gain unauthorized access.
What is the point of RDP
What is remote desktop protocol (RDP) Remote desktop protocol (RDP) is a secure network communications protocol developed by Microsoft. It enables network administrators to remotely diagnose problems that individual users encounter and gives users remote access to their physical work desktop computers.
Does RDP hide IP address
Both VPN and RDP, in some way, encrypt your internet traffic. Both provide private access to a server or device that might be located thousands of miles away. If you've ever used Teamviewer or similar applications, you know what RDP is and how you can access a computer or server from anywhere.
What is a RDP used for
The Remote Desktop Protocol (RDP) is a protocol, or technical standard, for using a desktop computer remotely. Remote desktop software can use several different protocols, including RDP, Independent Computing Architecture (ICA), and virtual network computing (VNC), but RDP is the most commonly used protocol.
When would you use RDP
RDP can be used by employees working from home or traveling who need access to their work computers. RDP is also often used by support technicians who need to diagnose and repair a user's system remotely and by admins providing system maintenance.
Can you get hacked by RDP
Remote Desktop Protocol can be hugely useful, but this technology is not airtight in terms of security, and can, in fact, be hacked.
What do hackers use RDP for
Hackers use RDP to gain access to the host computer or network and then install ransomware on the system. Once installed, regular users lose access to their devices, data, and the larger network until payment is made.
What are the risks of using RDP
What are the main RDP security vulnerabilitiesWeak user sign-in credentials. Most desktop computers are protected by a password, and users can typically make this password whatever they want.Unrestricted port access. RDP connections almost always take place at port 3389*.
Is it possible to get tracked behind RDP
Even if you're using an IP address, your internet service provider (ISP) will see everything – even see through the masking of VPN. So technically, you can be tracked through RDP if you're not using a VPN. But even so, you would need to remove access limits and make the connection OPEN.