Summary of the article:
1. Is it possible to stop DDoS attacks? In extreme cases, shutting down the services being attacked can prevent immediate damage, but it also stops all user traffic, making it a last resort effort.
2. What is the weakness of DDoS attacks? A SYN flood DDoS attack exploits a weakness in the TCP connection sequence, known as the “three-way handshake.”
3. Can DDoS attacks be prevented? While it is not possible to completely prevent a DDoS attack, implementing intrusion prevention, threat management strategies, and continuous monitoring can make it harder for attackers to carry out the attack.
4. What is the best prevention for a DDoS attack? Setting up a DDoS response plan, fortifying network security systems, monitoring network traffic, using multiple servers and cloud protection, implementing best security practices, and performing security assessments are effective prevention measures.
5. How long do DDoS attacks usually last? Depending on the severity, DDoS attacks can last up to a day or more, but with proper planning and security measures, small to mid-sized attacks can usually be managed in a matter of hours or minutes.
6. Why are DDoS attacks illegal? The use of booter and stresser services for conducting DDoS attacks is punishable under the Computer Fraud and Abuse Act, resulting in consequences such as seizure of devices, arrest, and criminal prosecution.
7. Why are DDoS attacks difficult to stop without rate limiting measures? DDoS attacks distribute requests among millions of IP addresses, making it challenging to stop them without measures like rate limiting.
8. What are three reasons for DDoS attacks? DDoS attacks can be motivated by extortion attempts, ideological reasons, or to disrupt businesses or services.
Unique questions based on the text:
1. How can shutting down services as a last resort to stop DDoS attacks affect businesses? Shutting down services can lead to potential loss of customers and revenue.
2. How does a SYN flood DDoS attack exploit a weakness in the TCP connection sequence? It takes advantage of the three-way handshake process, requiring a SYN request, SYN-ACK response, and ACK response.
3. What are some measures that can make it harder for attackers to carry out DDoS attacks? Intrusion prevention, threat management, and continuous monitoring can make it more difficult for attackers to execute DDoS attacks.
4. How can one fortify network security systems to prevent DDoS attacks? Strengthening network security infrastructure, using multiple servers and cloud protection, and implementing security best practices can help prevent DDoS attacks.
5. How can the duration of DDoS attacks be managed? With robust planning and security partnerships, small to mid-sized DDoS attacks can be managed within hours or minutes.
6. What are the legal consequences of conducting DDoS attacks using booter and stresser services? It is punishable under the Computer Fraud and Abuse Act and can result in seizure of devices, arrest, and criminal prosecution.
7. Why do DDoS attacks often distribute requests among many different sources? Distributing the attack allows each source to avoid exceeding rate limits and makes it harder to identify and stop the attack.
8. What are some motivations behind DDoS attacks? Extortion attempts, ideological reasons, and the intent to disrupt businesses or services can be motives behind DDoS attacks.
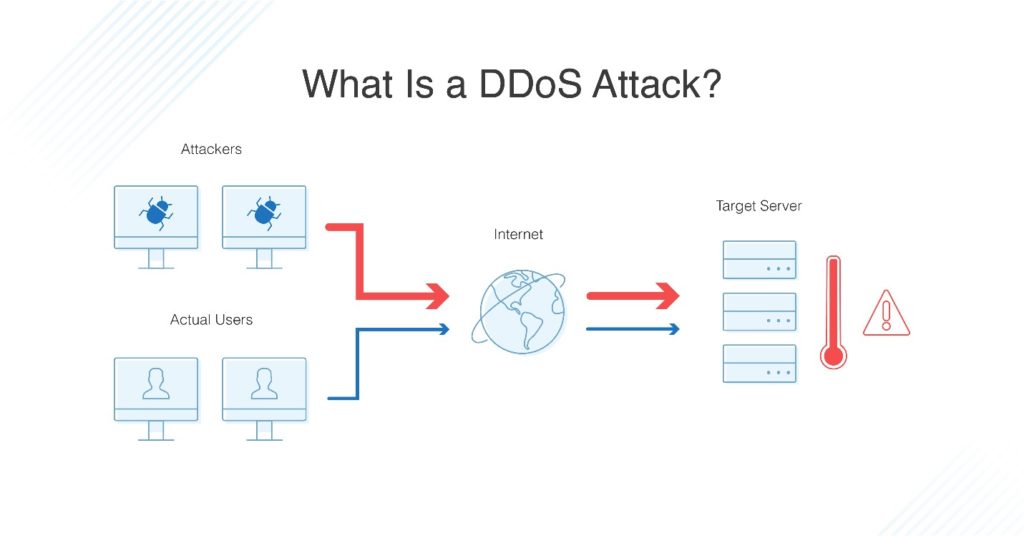
Is it possible to stop DDoS attacks
In extreme cases, you can completely shut down the services being attacked to prevent immediate damage. While this will stop attacker traffic, it stops all user traffic in its entirety. Stopping services can make businesses lose potential customers and revenue, making it a last resort effort to stop DDoS attacks.
Cached
What is DDoS attack weakness
A SYN flood DDoS attack exploits a known weakness in the TCP connection sequence (the “three-way handshake”), wherein a SYN request to initiate a TCP connection with a host must be answered by a SYN-ACK response from that host, and then confirmed by an ACK response from the requester.
Is there no way to prevent DDoS attacks
While there is no way to completely prevent a DDoS attack, having a DDoS strategy that utilizes intrusion prevention and threat management in place, implementing mitigation strategies and continuous monitoring can make it harder for malicious actors to go through with a DDoS attack.
Cached
What is the best prevention for a DDoS attack
How to Prevent DDoS AttacksSet up a DDoS Response Plan.Fortify the Network Security Systems and Infrastructure.Monitor Your Network Traffic.Use Multiple Servers and Cloud Protection.Implement Best Security Practices.Perform Security Assessments.
How long does a DDoS usually last
Depending on the severity of the attack, DDoS attacks can last up to a day or more. But with robust planning and good security partners, you can usually manage small to mid-sized attacks in a matter of hours or minutes.
What makes DDoS illegal
The use of booter and stresser services to conduct a DDoS attack is punishable under the Computer Fraud and Abuse Act (18 U.S.C. § 1030), and may result in any one or a combination of the following consequences: Seizure of computers and other electronic devices. Arrest and criminal prosecution.
Why are DDoS attacks often difficult to stop without measures like rate limiting
However, DDoS attacks have unique challenges because they distribute requests among many different sources, sometimes millions of IP addresses. Distributing the attack allows each source to avoid exceeding the rate limit.
What are 3 reasons for DDoS attack
For example, website owners can be asked to pay a ransom for attackers to stop a DDoS attack. DDoS attacks can have many other motivations including political, hacktivist, terrorist, and business competition. Anyone with a financial or ideological motive can damage an organization by launching a DDoS attack against it.
What makes DDoS attacks possible
DDoS attacks are carried out with networks of Internet-connected machines. These networks consist of computers and other devices (such as IoT devices)which have been infected with malware, allowing them to be controlled remotely by an attacker.
What is the most impactful DDoS attack
Top 5 Most Famous DDoS AttacksWhat is a DDoS attackThe AWS attack of February 2020.The GitHub attack of February 2018.The Dyn attack of October 2016.The Mafiaboy attacks of 2000.The largest DDoS attack ever in September 2017.
Can a DDoS be traced back
Can you trace DDoS attacks DDoS attacks are pretty difficult to trace because most of them are distributed over hundreds and thousands of other devices. Also, those who initiate such attacks usually make an effort not to be found.
Can someone go to jail for DDoS
The use of booter and stresser services to conduct a DDoS attack is punishable under the Computer Fraud and Abuse Act (18 U.S.C. § 1030), and may result in any one or a combination of the following consequences: Seizure of computers and other electronic devices. Arrest and criminal prosecution.
Can you go to jail if you DDoS someone
The use of booter and stresser services to conduct a DDoS attack is punishable under the Computer Fraud and Abuse Act (18 U.S.C. § 1030), and may result in any one or a combination of the following consequences: Seizure of computers and other electronic devices. Arrest and criminal prosecution.
Is it a felony to DDoS someone
Is DDoSing Illegal in the U.S DDoSing is an Illegal cybercrime in the United States. A DDoS attack could be classified as a federal criminal offense under the Computer Fraud and Abuse Act (CFAA). The use of booter services and stressers also violates this act.
Why are DDoS attacks more difficult to deal with than DoS attacks
DDoS attacks are more difficult to detect because they are launched from multiple locations so that the victim can't tell the origin of the attack. Another key difference is the volume of attack leveraged, as DDoS attacks allow the attacker to send massive volumes of traffic to the target network.
Can rate limiting stop DDoS
Cloudflare Rate Limiting, for instance, protects against DDoS attacks, API abuse, and brute force attacks, but it doesn't necessarily mitigate other forms of malicious bot activity, and it doesn't distinguish between good bots and bad bots. In contrast, bot management can holistically detect bot activity in general.
How long do DDoS attacks last
This type of sporadic attack can vary in length, from short-term actions that last for a few minutes to longer strikes that exceed an hour. According to the DDoS Threat Landscape Report 2021 from Swedish telecom Telia Carrier, documented attacks average a 10-minute duration.
How do DDoS attacks start
Most DDoS attacks are done with botnets – groups of computers all acting together. These computers will all attempt to access a website simultaneously, overwhelming the server and bringing it down. How do they get these botnets By hijacking other machines.
What is the simplest DDoS attack
A packet flood is the original and simplest form of DDoS attack types, exploiting basic network traffic protocols to flood a server with millions of redundant requests.
Are DDoS attacks hard
A DDoS attack is surprisingly easy to carry out and affects millions of websites worldwide every year, with the number of attacks rising.
How long does it take for a DDoS to go away
Depending on the severity of the attack, DDoS attacks can last up to a day or more. But with robust planning and good security partners, you can usually manage small to mid-sized attacks in a matter of hours or minutes. Not all attacks take place in a single flood, making them harder to detect.
How long does a DDoS last
This type of sporadic attack can vary in length, from short-term actions that last for a few minutes to longer strikes that exceed an hour. According to the DDoS Threat Landscape Report 2021 from Swedish telecom Telia Carrier, documented attacks average a 10-minute duration.
Is IP stressing illegal
Running it against someone else's network or server, resulting in denial-of-service to their legitimate users, is illegal in most countries.
Is it illegal to DDoS a school
DDoSing is an Illegal cybercrime in the United States. A DDoS attack could be classified as a federal criminal offense under the Computer Fraud and Abuse Act (CFAA). The use of booter services and stressers also violates this act.
Can someone DDoS you with just your IP
Can you DDoS someone with their IP Yes, someone can DDoS you with just your IP address. With your IP address, a hacker can overwhelm your device with fraudulent traffic causing your device to disconnect from the internet and even shut down completely.
