Vulnerability and Risk
Vulnerability refers to the susceptibility of being harmed or affected by external factors, whether they are natural or human-induced hazards. It considers the probability of harmful consequences or expected losses, such as deaths, injuries, property damage, disruptions in livelihoods, economic activity, or environmental damage. Vulnerability arises from the interactions between these hazards and vulnerable conditions.
For example, in the context of cybersecurity, an employee’s susceptibility to a phishing email is a vulnerability. If they mistakenly open an attachment, malware can be released onto their system, causing significant problems.
There are various examples of vulnerability, including susceptibility to humidity, dust, soiling, natural disasters, poor encryption, or firmware vulnerability.
Risk, on the other hand, refers to the possibility of something bad happening. It involves uncertainty about the effects or implications of an activity with respect to something humans value, such as health, well-being, wealth, property, or the environment. Risk often focuses on negative and undesirable consequences. Examples of risk include damage by fire, flood, or other natural disasters, as well as unexpected financial loss due to an economic downturn or bankruptcy of other businesses that owe you money.
In the field of information security, there are four main types of vulnerabilities: network vulnerabilities, operating system vulnerabilities, process vulnerabilities, and human vulnerabilities.
There are six types of vulnerability that can be identified in research subjects:
- Cognitive vulnerability
- Juridic vulnerability
- Deferential vulnerability
- Medical vulnerability
- Allocational vulnerability
- Infrastructural vulnerability
Questions:
- What is vulnerability and risk?
- Can you provide an example of vulnerability risk?
- What are some examples of vulnerability?
- Can you provide five examples of vulnerability?
- Can you give an example of risk?
- What are the four main types of vulnerability in information security?
- How would you define risk?
- Can you list six types of vulnerability?
Vulnerability refers to the susceptibility of being harmed or affected by external factors, while risk refers to the possibility of something bad happening.
Phishing emails can be a vulnerability risk. An employee’s susceptibility to fall for these emails is the vulnerability. If they open an attachment, it can release malware onto their system, causing significant problems.
Examples of vulnerability include susceptibility to humidity, dust, soiling, natural disasters, poor encryption, or firmware vulnerability.
Examples of vulnerability can range from telling someone when they’ve upset you or sharing something personal about yourself that you normally wouldn’t to admitting to past mistakes.
An example of risk includes damage by fire, flood, or other natural disasters. It can also involve unexpected financial loss due to an economic downturn or bankruptcy of other businesses that owe you money.
The four main types of vulnerabilities in information security are network vulnerabilities, operating system vulnerabilities, process vulnerabilities, and human vulnerabilities.
Risk is the possibility of something bad happening. It involves uncertainty about the effects or implications of an activity with respect to something humans value, often focusing on negative and undesirable consequences.
Six types of vulnerability can be identified: cognitive vulnerability, juridic vulnerability, deferential vulnerability, medical vulnerability, allocational vulnerability, and infrastructural vulnerability.
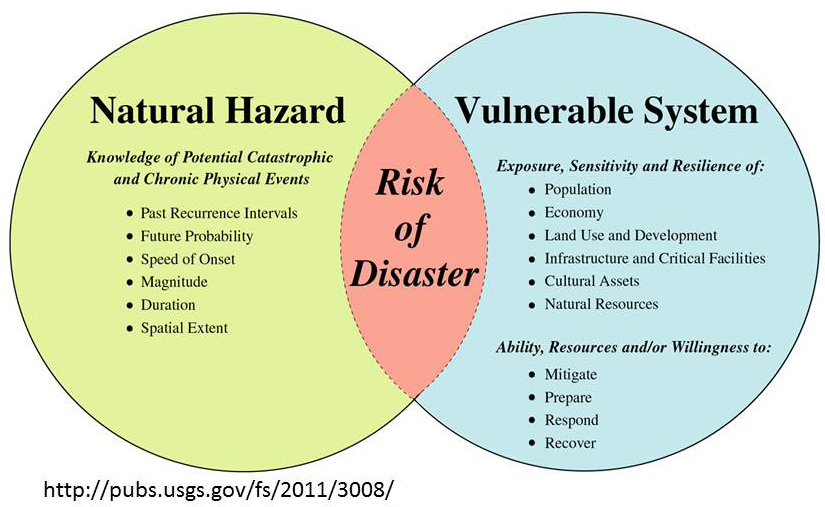
What is vulnerability and risk explain
It considers the probability of harmful consequences, or expected losses (deaths, injuries, property, livelihoods, economic activity disrupted or environmentally damaged) resulting from interactions between natural or human induced hazards and vulnerable conditions.
What is an example of vulnerability risk
In this example, the phishing email is the threat and the employee's susceptibility to be fooled is the vulnerability. If they mistakenly open the attachment, the malware will be released onto their system and cause huge problems.
What are 3 examples of vulnerability
Vulnerability Examples
Any susceptibility to humidity, dust, soiling, natural disaster, poor encryption, or firmware vulnerability.
What are 5 example of vulnerability
To illustrate the principles above, here are 11 specific examples of vulnerability: Telling someone when they've upset you, respectfully but honestly. Sharing something personal about yourself that you normally wouldn't. Admitting to mistakes you have made in the past.
What is a risk example
Examples of uncertainty-based risks include: damage by fire, flood or other natural disasters. unexpected financial loss due to an economic downturn, or bankruptcy of other businesses that owe you money.
What are the 4 main types of vulnerability
The four main types of vulnerabilities in information security are network vulnerabilities, operating system vulnerabilities, process (or procedural) vulnerabilities, and human vulnerabilities.
What’s the definition of risk
In simple terms, risk is the possibility of something bad happening. Risk involves uncertainty about the effects/implications of an activity with respect to something that humans value (such as health, well-being, wealth, property or the environment), often focusing on negative, undesirable consequences.
What are the 6 types of vulnerability
In a list that is intended to be exhaustively applicable to research subjects, six discrete types of vulnerability will be distinguished—cognitive, juridic, deferential, medical, allocational, and infrastructural.
What is a real life example of vulnerability
Other examples of vulnerability include these: A weakness in a firewall that lets hackers get into a computer network. Unlocked doors at businesses, and/or. Lack of security cameras.
What are the 4 types of risk
The main four types of risk are:strategic risk – eg a competitor coming on to the market.compliance and regulatory risk – eg introduction of new rules or legislation.financial risk – eg interest rate rise on your business loan or a non-paying customer.operational risk – eg the breakdown or theft of key equipment.
How do you define risk
Meaning behind the meaning
In its modern sense, the word risk has two distinct meanings: it can mean both the possibility of danger and simultaneously its potential consequences. The first definition emphasizes the source of the risk, while the second focuses on the target exposed to the risk.
What is vulnerability in simple words
ˈvəl-nər-bəl. : capable of being physically or emotionally wounded. : open to attack or damage. a vulnerable position. vulnerability.
What are the 10 factors of vulnerability
What are the top 10 factors affecting vulnerability to Covid-19Age.Deprivation.Diabetes.Severe asthma.Sex.Race.Obesity.Heart, kidney, liver and respiratory diseases.
What is an example of risk
Examples of uncertainty-based risks include: damage by fire, flood or other natural disasters. unexpected financial loss due to an economic downturn, or bankruptcy of other businesses that owe you money.
What are the 4 levels of vulnerability
The four continuous stages of identification, prioritization, remediation, and reporting are essential for an effective vulnerability management process.
What are 4 types of vulnerability examples
Types of vulnerability include social, cognitive, environmental, emotional or military.
What are the 3 levels of risk
1.3 Risk levels
We have decided to use three distinct levels for risk: Low, Medium, and High.
What are the 8 key risk types
These risks are: Credit, Interest Rate, Liquidity, Price, Foreign Exchange, Transaction, Compliance, Strategic and Reputation.
What is an example of vulnerable
able to be easily physically or mentally hurt, influenced, or attacked: I felt very vulnerable, standing there without any clothes on. It is on economic policy that the Democrats are most vulnerable. Tourists are more vulnerable to attack, because they do not know which areas of the city to avoid.
Which are the 4 key drivers of vulnerability
4 key drivers of customer vulnerabilityHealth. Conditions or illnesses that affect one's ability to complete day-to-day tasks, both mentally and physically.Life Events. Such as bereavement, job loss or relationship breakdown.Resilience. Low ability to withstand and manage financial or emotional shocks.Capability.
What are the common types of vulnerability
Different types of Security Vulnerabilities:Unpatched Software.Misconfiguration.Weak Credentials.Easy-to-phish-users.Trust Relationship.Compromised Credentials.Malicious Insider.Missing/Poor Encryption.
What are the 4 categories of risk
The main four types of risk are:strategic risk – eg a competitor coming on to the market.compliance and regulatory risk – eg introduction of new rules or legislation.financial risk – eg interest rate rise on your business loan or a non-paying customer.operational risk – eg the breakdown or theft of key equipment.
What are the 4 risk levels
The levels are Low, Medium, High, and Extremely High. To have a low level of risk, we must have a somewhat limited probability and level of severity. Notice that a Hazard with Negligible Accident Severity is usually Low Risk, but it could become a Medium Risk if it occurs frequently.
What are the 4 main categories of risk
The main four types of risk are:strategic risk – eg a competitor coming on to the market.compliance and regulatory risk – eg introduction of new rules or legislation.financial risk – eg interest rate rise on your business loan or a non-paying customer.operational risk – eg the breakdown or theft of key equipment.
What are the 4 levels of risk
The levels are Low, Medium, High, and Extremely High. To have a low level of risk, we must have a somewhat limited probability and level of severity. Notice that a Hazard with Negligible Accident Severity is usually Low Risk, but it could become a Medium Risk if it occurs frequently.