Application Guard is a security feature in Windows 10 that isolates Microsoft Edge from the rest of the system, creating a virtualized environment to protect against malware and attacks. While it does provide an extra layer of protection, whether it is worth it or not depends on your specific needs and risk tolerance. If you frequently browse the internet and visit potentially risky websites, Application Guard can help protect your system from malicious code. However, if you primarily use other web browsers or have other robust security measures in place, the benefits of Application Guard may be limited. Ultimately, it is up to you to weigh the potential security benefits against any potential limitations or impacts on performance.
What is the purpose of Credential Guard quizlet
Credential Guard is a component of Windows Defender that is a virtualization-based isolation technology for Local Security Authority Subsystem Service (LSASS). Its purpose is to prevent attackers from stealing credentials.
Cached
Should I turn on Credential Guard
Despite its usefulness in preventing credential stealing and Pass the Hash attacks, Credential Guard will cause some services and protocols to break. For instance, enabling the security feature prevents you from using Windows To Go, Kerberos unconstrained delegation, and DES encryption.
Cached
Should I enable Windows Defender Credential Guard
We recommend enabling Windows Defender Credential Guard before a device is joined to a domain. If Windows Defender Credential Guard is enabled after domain join, the user and device secrets may already be compromised.
What is the Credential Guard process
Credential Guard prevents attackers from dumping credentials stored in LSASS by running LSASS in a virtualized container that even a user with SYSTEM privileges cannot access. The system then creates a proxy process called LSAIso (LSA Isolated) for communication with the virtualized LSASS process.
Cached
What are the benefits of a credential
Earning a credential demonstrates your commitment to your career and gives you valuable insights and real-world skills you can use on the job. Credentials also validate your knowledge and skills, enhance your credibility, boost your confidence and earn your respect among clients and peers.
What are three reasons why credentialing is important for a medical assistant entry and advancement in the medical environment
The following paragraphs will describe the top 3 reasons why medical credentialing is important: 1) Prevents revenue loss, 2) Protects your patients, and 3) Mitigates lawsuits and reputational damage. A primary fiscal reason to properly credential medical staff is to assure compliance to state and federal regulations.
Is it safe to give your credentials
Never use your credentials and passwords to create accounts on social networks or virtual stores. Never share your passwords with others; they are personal, non-transferable, and should never be revealed.
Is Application Guard worth it
If you haven't heard of this feature, it launches the Edge browser in an isolated environment as a way to protect your PC and your data from malware. For whatever reason, this feature hasn't gotten much press. Even so, it is definitely worth taking the time to install it.
Does Windows Defender security lock your computer
No, it is not real. It is a fake warning designed to scare you into performing steps that could get your computer infected, or make you share sensitive personal information that could later be used in financial fraud or identity theft.
Is it risky to turn off Windows Defender
But don't disable Defender unless you have another antivirus program ready to be installed. That's because without active anti-virus protection, you're exposed to a massive security risk. It's also not advisable to run multiple antivirus programs at the same time.
How do I set up Credential Guard to work
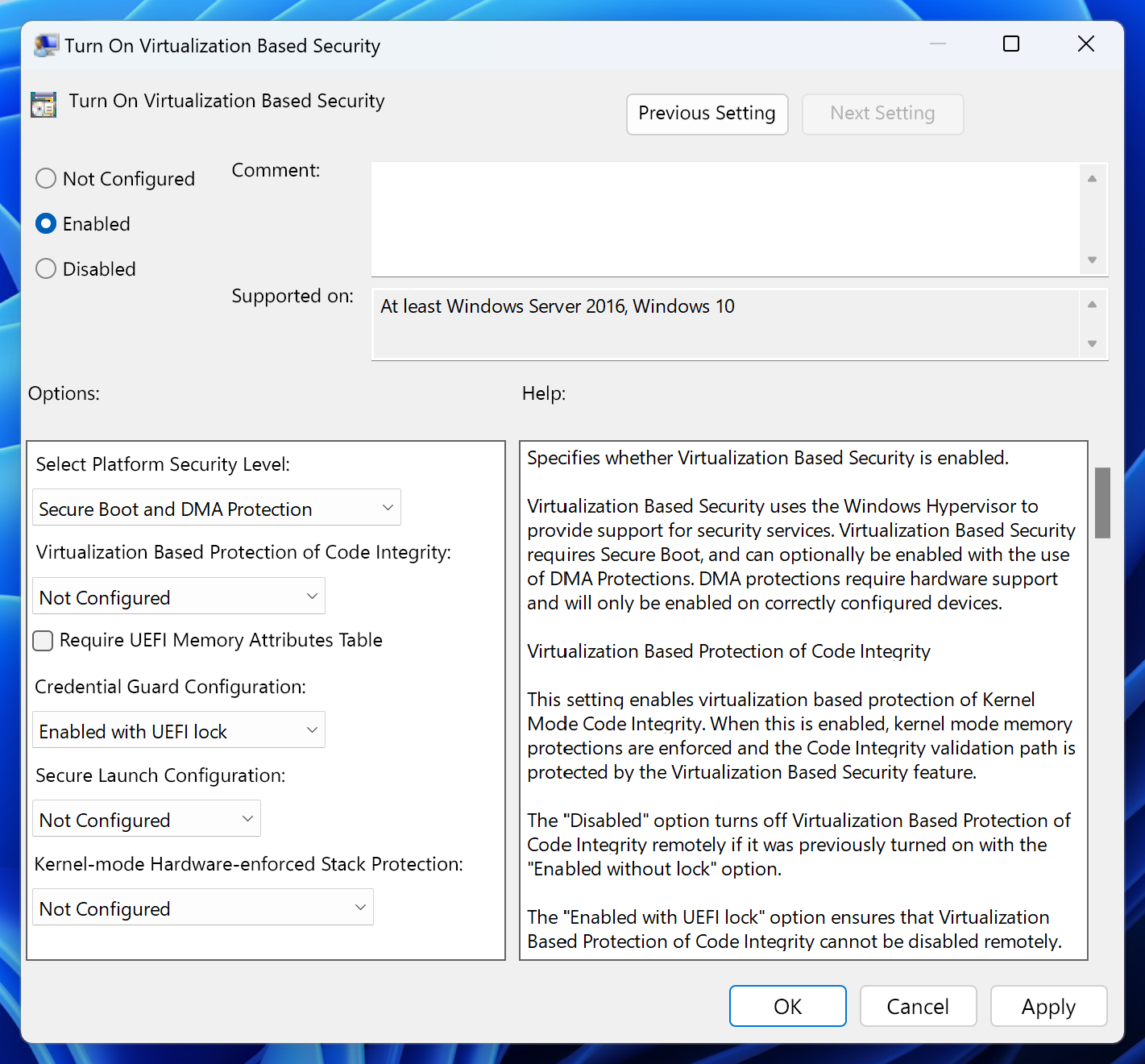
Option 2: Enabling Credential Guard using Group Policy
Alternatively, you can use Group Policy Manager to enable Credential Guard. Create a GPO and go to Computer Configuration > Administrative Templates > System > Device Guard. Then set Turn on Virtualization Based Security to Enabled, as shown below.
How are credentials captured
When the target tries to log in, the credentials are captured by the attacker. The attacker installs malware on a target's computer which will capture the target's keystrokes during log in and forward them to the attacker.
What does it mean to receive credentials
Credentials offer proof of a fact, or of qualifications. A driver's license, a doctor's badge, or a diploma all count as credentials — as long as they're real! One document can be a credential, but the word usually still gets pluralized.
What is a credential and what does it mean
1. : something that gives a title to credit or confidence. also : qualification sense 3a. the applicant with the best credentials. credentials plural : testimonials or certified documents showing that a person is entitled to credit or has a right to exercise official power.
What are the benefits of credentialing
The advantages of credentialing include enhanced recognition, credibility, and mobility in the field of DOD Human Resources, and the promotion and acknowledgment of a recognized body of knowledge in a technical field.
What are the benefits of credentialing in healthcare
Maintain Patient Safety
Credentialing helps to protect patient safety by ensuring practices and physicians have the experience and skills necessary to perform procedures on patients. The process helps reduce the risk of medical errors that may be caused by incompetent providers.
Why is it important to verify credentials
Verification efforts should determine if the license or certification is valid, current, and in good standing. This verification should also uncover any disciplinary actions, adverse actions or complaints associated with that license.
Should I put my credentials after my name
“The only academic credentials (degrees) that you should list after your name at the top of the résumé should be doctorate level degrees, such as MD, DO, DDS, DVM, PhD, and EdD. A master's degree or bachelor's degree should never be included after your name.
What are the requirements for application guard
Hardware requirements
| Hardware | Description |
|---|---|
| Hardware memory | Microsoft requires a minimum of 8-GB RAM |
| Hard disk | 5-GB free space, solid state disk (SSD) recommended |
| Input/Output Memory Management Unit (IOMMU) support | Not required, but recommended |
How do I bypass application guard
Launch the control panel and go to Programs > Uninstall a Program. On the Programs and Features window, select Turn Windows features on or off. From the list of features, untick or uncheck the box “Microsoft Defender Application Guard” and click OK.
Why is my computer locked up by Windows Defender security warning
The fake Windows Defender security warning is usually hidden among your browser extensions. Luckily, deleting and reinstalling, or resetting your browser to the default settings, with no extensions enabled and your cache cleared, will normally remove the warning message.
Is there any risk in turning off Windows Defender
But don't disable Defender unless you have another antivirus program ready to be installed. That's because without active anti-virus protection, you're exposed to a massive security risk. It's also not advisable to run multiple antivirus programs at the same time.
Is Windows Defender good enough to remove viruses
Yes, Windows Defender is a good basic virus protection software. You may not find everything you want if you are extremely security focused. A third-party antivirus or anti-malware software will likely find threats that Windows Defender may miss.
What are the disadvantages of Windows Defender
Cons of Windows DefenderLacks integrated dashboard for all devices using Windows Defender.No accountability if the computer is infected by malware.Limited features for large scale use.Slows down installation of frequently-used applications.
How does remote Credential Guard work
Introduced in Windows 10, version 1607, Windows Defender Remote Credential Guard helps you protect your credentials over a Remote Desktop connection by redirecting Kerberos requests back to the device that's requesting the connection. It also provides single sign-on experiences for Remote Desktop sessions.
