ryone can monitor the encrypted communication. However, there are certain methods that can be used to monitor end-to-end encryption. For example, malware or spyware can be installed on one of the devices involved in the communication, allowing a third party to access the decrypted information. Additionally, metadata such as the time and duration of communication can still be monitored, even with end-to-end encryption in place.
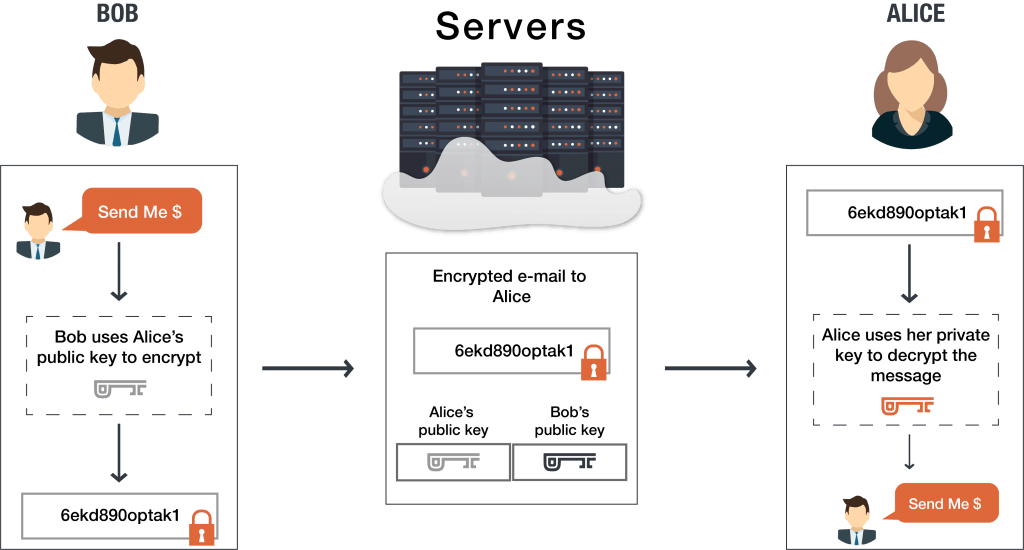
What are the pros and cons of end-to-end encryption
The Pros of End-to-End EncryptionProtection of Privacy.Integrity of Data.Highly Sensitive Data Exchanges.Device Level Over Server Level.Avoiding High-Cost Attacks and Reputation Damage.Ledger is Still Available.Unreliable Receiving Devices.Law Enforcement and Surveillance Concerns.
Cached
What are the benefits of encryption
Benefits of Using Encryption Technology for Data SecurityEncryption is Cheap to Implement.Encryption Can Save You from Regulatory Fines.Encryption Can Help to Protect Remote Workers.Encryption Increases the Integrity of Our Data.Encryption Can Increase Consumer Trust.
What is the downside of end-to-end encryption
Disadvantages of end-to-end encryption
The security that end-to-end privacy offers might be limited if a third party gets physical access to the device at either end of the transmission — not only can they read existing messages, but also send new ones.
Cached
Can end-to-end encryption be hacked
Can end-to-end encryption be hacked. Unfortunately, everything, including end-to-end encryption, can be hacked. It is just a matter of time. The great thing about end-to-end encryption is that even though it can be hacked, it would take hundreds if not thousands of years to do so.
What are the disadvantages of an encrypted message
The user would be unable to explore the encrypted file if the password or key got the loss. However, using simpler keys in data encryption makes the data insecure, and randomly, anyone can access it.
What are 3 purposes of encryption
Not only does it keep the data confidential, but it can authenticate its origin, ensure that data has not changed after it was sent, and prevent senders from denying they sent an encrypted message (also known as nonrepudiation).
What are two reasons to use encryption
It helps protect private information, sensitive data, and can enhance the security of communication between client apps and servers. In essence, when your data is encrypted, even if an unauthorized person or entity gains access to it, they will not be able to read it.
Can end-to-end encryption be monitored
In theory, end-to-end encryption means that only the sender and receiver hold the keys they need to decrypt their message. Not even an app's owners can peek in.
Can end-to-end encryption be broken
Can end-to-end encryption be hacked. Unfortunately, everything, including end-to-end encryption, can be hacked. It is just a matter of time. The great thing about end-to-end encryption is that even though it can be hacked, it would take hundreds if not thousands of years to do so.
Can governments see end-to-end encryption
No individual or entity – no hacker, no cybercriminal, no company or organization or government – can access data and communications protected with end-to-end encryption. It's the ultimate tool to protect individuals' right to privacy.
Why would someone use encrypted messaging
Why would someone send me an encrypted message An encrypted message prevents any outside parties from reading the message, even if they are able to intercept it. Without the proper keys to unencrypt the message, no one except the sender and recipient can read the message's contents.
What are the 4 objectives of encryption
Cryptography has four major goals: confidentiality, integrity, authentication, and non-repudiation.
What are the three goals of encryption
Goals of CryptographyData Privacy(confidentiality)Data Authenticity(it came from from where it claims)Data integrity(it has not been modified on the way) in the digital world.
Can police see end-to-end encrypted messages
End-to-end encryption (E2EE) is a system that, amongst others, allows mobile phone users to communicate with each other without anyone else eavesdropping. So, the police cannot listen in either, even if they are authorized to tap the communication.
Can the FBI see signal
Messages are encrypted end to end, FBI cannot access them. Signal does not store messages or user data outside of registration date and date of last use. Signal features screen lock and pin to make accessing messages, even with access to device, slightly more difficult to prevent snooping.
Can my phone be hacked if encrypted
Can an encrypted device be hacked Yes, encrypted devices are still vulnerable to spyware. With encryption, the data on your device stays scrambled and unreadable until the password is entered.
Can hackers see encrypted messages
No, hackers cannot see encrypted data, as it is scrambled and unreadable until the encryption key (or passphrase) is used to decrypt it. However, if a hacker manages to obtain the encryption key or crack the encryption algorithm, then they can gain access to the data.
Can FBI read end-to-end encryption
With some exceptions, many major E2EE messaging services hand over all kinds of data to federal law enforcement, and cloud backups can even enable the disclosure of stored messages sent on two of the biggest E2EE messaging apps.
Can police read end-to-end encrypted messages
In general, law enforcement does not have access to end-to-end encrypted (E22E) messages sent via these services.
Why would someone encrypt their phone
Whole-phone encryption means that all the data contained on a device is protected from unauthorised access. It would prevent, for example, somebody accessing your data if your phone was lost or stolen and protected with the encryption PIN or password.
Can the FBI see my texts
Maximum of seven days' worth of specified users' text chats (Only when end-to-end encryption has not been elected and applied and only when receiving an effective warrant; however, video, picture, files, location, phone call audio and other such data will not be disclosed).
Can the government see encrypted data
Because of warrant-proof encryption, the government often cannot obtain the electronic evidence and intelligence necessary to investigate and prosecute threats to public safety and national security, even with a warrant or court order.
Can police recover Signal messages
Signal is designed to never collect or store any sensitive information. Signal messages and calls cannot be accessed by us or other third parties because they are always end-to-end encrypted, private, and secure.
Can the NSA see my texts
2. Big Tech passes your data to the NSA. Facebook, Google, Apple, and six other leading online services have all gone on record as having given their customers' data to the NSA, as legally required by the “PRISM” program. Data shared includes emails, messages, and documents.
Why would you encrypt your phone
Encrypting your device means that the data (such as credit card info, social security numbers, addresses, or any other extremely personal information) that is entered into the phone will be jumbled up, making it indecipherable to anyone who might be trying to steal your information.