Summary:
1. Security Detection: Security detection relies on sensing technology to detect the presence or activities of people.
2. Detection in Cyber Security: Threat detection is the process of analyzing a security ecosystem to find malicious users and abnormal activity.
3. Goals of Security Detection: The three main security goals are confidentiality, integrity, and availability.
4. Three Main Detection Types: The three main types of detection are signature-based, anomaly-based, and hybrid intrusion detection.
5. TSA and Tampons: TSA body scanners cannot detect tampons as they cannot see inside the body.
6. Working of Security Detectors: Store sensors detect light reflected by the lighting system and generate a signal that tags and labels respond to.
7. Example of Detection: Detection can be seen at airports with German Shepherds trained to detect drugs or explosives.
8. Types of Detection in Cyber Security: Some popular methods include threat intelligence, behavior analytics, intruder traps, and threat hunting.
Questions:
- What is the principle of security detection?
- What does detection mean in cyber security?
- What are the goals of security detection?
- What are the three main types of detection?
- Can TSA see my tampon during a body scan?
- How do security detectors work?
- What is an example of detection?
- What are the types of detection in cyber security?
The principle of security detection relies on sensing technology to detect the presence or activities of people.
Detection in cyber security is the process of analyzing a security ecosystem to find malicious users and abnormal activity.
The three main goals of security detection are to protect confidentiality, preserve integrity, and promote availability of data.
The three main types of detection are signature-based, anomaly-based, and hybrid intrusion detection.
No, TSA body scanners cannot see inside the body and therefore cannot detect tampons.
Security detectors in stores detect light reflected by the lighting system and generate a signal that tags and labels respond to.
An example of detection is the use of German Shepherds at airports to detect drugs or explosives.
Some types of detection in cyber security include threat intelligence, behavior analytics, intruder traps, and threat hunting.
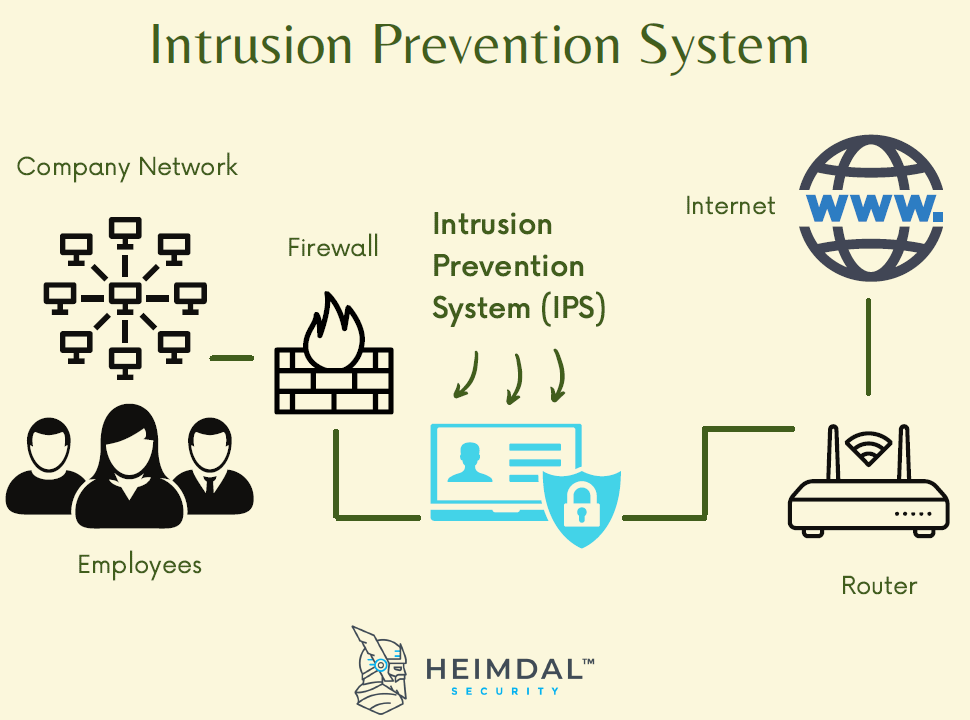
What is the security detect
The principle of detection relies on sensing technology to discover the presence of a person or object within its field of view. That is, if the purpose of security technology is to detect the presence or activities of people, then the detection methods must be devised to respond to these stimuli.
What does detection mean in cyber security
Threat detection is the process of analyzing a security ecosystem at the holistic level to find malicious users, abnormal activity and anything that could compromise a network. Threat detection is built on threat intelligence, which involves tools that are strategic, tactical and operational.
What are the goals of security detection
Principle 2: The Three Security Goals Are Confidentiality, Integrity, and AvailabilityProtect the confidentiality of data.Preserve the integrity of data.Promote the availability of data for authorized use.
What are the three main detection types
The 3 Intrusion Detection System MethodsSignature-Based Intrusion Detection. Signature-Based Intrusion Detection Systems (SIDS) aim to identify patterns and match them with known signs of intrusions.Anomaly-Based Intrusion Detection.Hybrid Intrusion Detection.
Cached
Can TSA see my tampon
Can you see a tampon during an airport body scan This is a frequently asked question on Google, and if it's something you're worried about, you can breathe a sigh of relief. Airport body scanners can't see inside the body and therefore can't detect a tampon on a TSA female body scan image.
How do security detectors work
The store sensors detect light reflected by the lighting system. From there, it generates an analog signal that is sent to the decoder. Then, security tags and labels attached to the products in the store respond to the signal.
What is an example of detection
Detection is the act of noticing or discovering something. At the airport, you might see German Shepherds trained in the detection of drug smuggling or explosives in luggage.
What are the types of detection in cyber security
Here are four popular threat detection methods and how they work.Threat intelligence.User and attacker behavior analytics.Intruder traps.Threat hunting.Security event detection technology.Network threat technology.Endpoint threat technology.Security data lake implementation.
What are the 4 basic security goals
Those are the factors that should determine the solutions you need to meet your objectives for data availability, integrity, confidentiality and traceability.Availability.Integrity.Confidentiality.Traceability.
What are the 3 main goals of security *
Confidentiality, integrity, availability.
What are detection methods
The method detection limit (MDL) is the minimum concentration of a substance that can be measured and reported with 99% confidence that the analyte concentration is greater than zero and is determined from analysis of a sample in a given matrix containing the analyte [2].
What are the two types of detection systems
What Are the Types of Intrusion Detection Systems There are two main types of IDSes based on where the security team sets them up: Network intrusion detection system (NIDS). Host intrusion detection system (HIDS).
What shows up on TSA screen
Transportation Security Administration (TSA) screeners at airports check passengers and personal items for dangerous items such as weapons, chemicals and liquids that are not allowed as carry-on items.
Does TSA know when you’re on your period
Maybe a regular pad that has too much blood on it would show too What about tampons Either way, if you're on your period the TSA agent will most likely know. She even showed me the picture of my scan.
What can trigger a security alarm
Excessive dust, spider webs, and loose sensors and detectors can all be the source of false alarms.
What can detectors detect
With sophisticated detectors, operators can determine whether a particular concealed target is lead, iron, aluminum, gold, copper, or silver, based on the metal's conductivity. Detectors also can be programmed to search for a single, predetermined target, regardless of size, while disregarding all other metals.
What are the types of detection
Detection Methods (1)Types of Detection Methods. When choosing a detection method for a given substance, typically we would first check the structure of that substance.UV-Visible Detection.Refractive Index Detection.Fluorescence Detection.Electrochemical Detection.Evaporative Light Scattering Detector.
What is the purpose of detection
Finally, the art of detection, also known as following clues, is the work of a detective in attempting to reconstruct a sequence of events by identifying the relevant information in a situation.
What are 4 methods of threat detection
Threat detection can be summarized into four types: Configuration, Modeling (Anomalies), Indicators, and Behavioral Analytics. Understanding the difference in these types and how to use each enables industrial control system (ICS) security teams to defend their environments appropriately.
What are the 5 types of security
Cybersecurity can be categorized into five distinct types:Critical infrastructure security.Application security.Network security.Cloud security.Internet of Things (IoT) security.
What are the 5 C’s in security
Change, Compliance, Cost, Continuity, and Coverage; these are all fundamental considerations for an organization.
What do the 4 C’s stand for in security
The Four C's in Closing
To be a successful partner in the government sector, you should be mindful of the four C's: commitment, compliance, coverage and communication.
What are the three C’s of security
The 3Cs of Best Security: Comprehensive, Consolidated, and Collaborative – Check Point Blog.
What are the four basic for security
This framework consists of four elements – assets, vulnerabilities, threats, and controls. We define each of these terms, provide examples for each, and describe how they are related to each other.
Why do I always get flagged at TSA
As shown in more detail below, this additional screening could be caused by things like: Your name matching a name of interest in a database. You raising suspicions while going through airport security. Your bag getting flagged when going through an x-ray machine.
