Should I turn off two-factor authentication?
Your account is more secure when you need a password and a verification code to sign in. If you remove this extra layer of security, you will only be asked for a password when you sign in. It might be easier for someone to break into your account.
Should I enable two-factor authentication?
2FA is essential to web security because it immediately neutralizes the risks associated with compromised passwords.
What does two-factor authentication do?
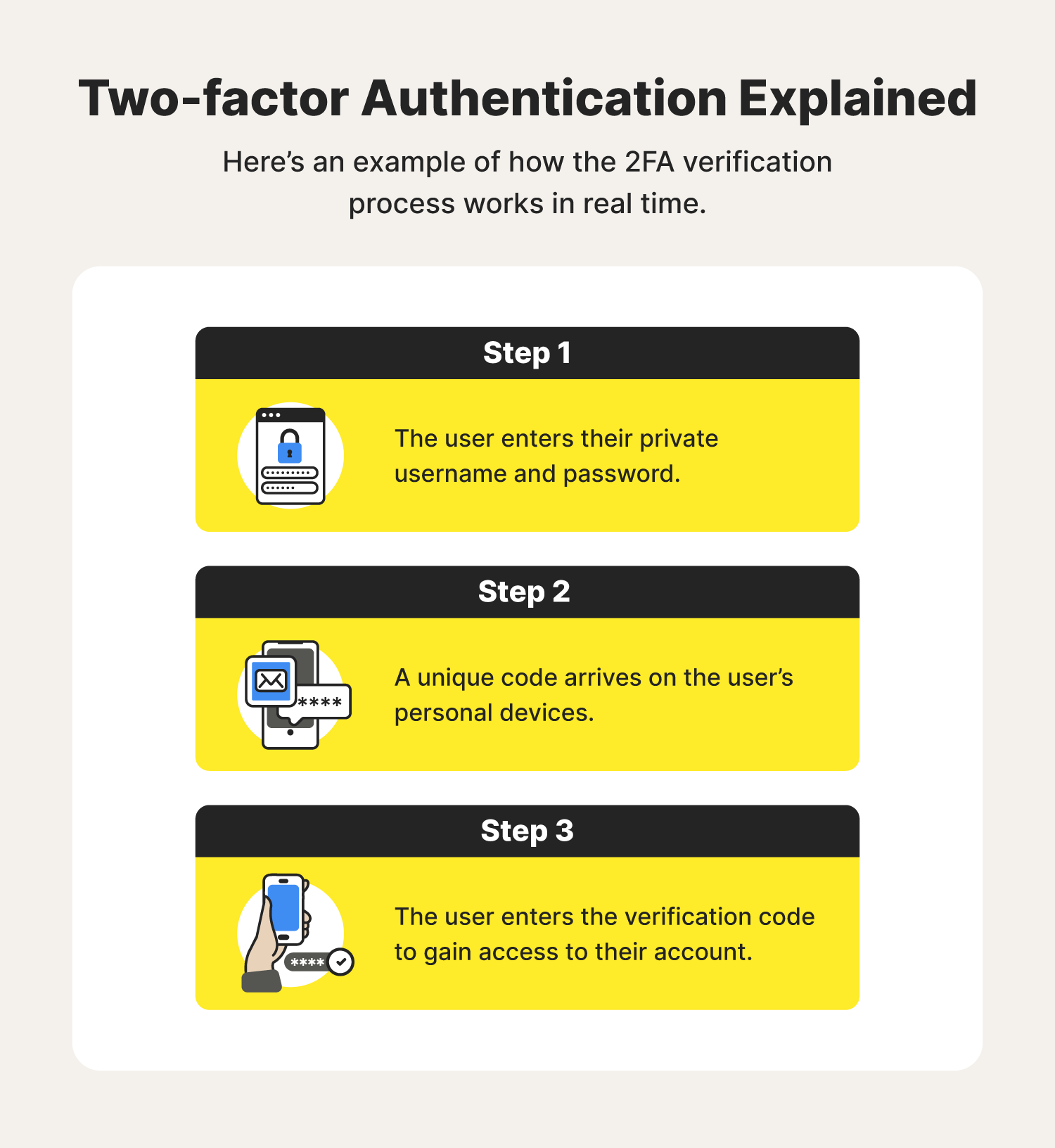
With two-factor authentication, a trusted device or trusted phone number helps verify your identity when you sign in to a new device or browser.
What is two-factor authentication and is it safe?
Two-factor authentication (2FA) is a security measure that requires consumers two factors to verify their digital identity. Meaning, it does not grant access if the user cannot produce the right username and password, both unique to the individual.
What’s the main disadvantage of two-factor authentication?
Potential downsides to two-factor authentication include increased login time – Users must go through an extra step to log into an application, adding time to the login process.
What are the pros and cons of using two-factor authentication?
The main advantage of two-factor authentication is the increased login security. As for the shortcomings, the main two being the increase in the time of entry into the system and the risk of losing the physical media serving to pass one of the authentication steps (mobile phone, U2F key, OTP-token).
What are three examples of two-factor authentication?
Something you know, like a password or PIN.
Something you have, like your ATM card or your phone.
Something you are, like a fingerprint or voice print.
What triggers two-factor authentication?
The three factors that can be used for two-factor authentication are something you know (like a password), something you have (like a bank card), and something you are (like face ID). 2FA requires two of these three factors. MFA may use all three or even GPS tracking to confirm your physical location.
Should I turn off two-factor authentication
Your account is more secure when you need a password and a verification code to sign in. If you remove this extra layer of security, you will only be asked for a password when you sign in. It might be easier for someone to break into your account.
Should I enable two-factor authentication
2FA is essential to web security because it immediately neutralizes the risks associated with compromised passwords.
What does two-factor authentication do
With two-factor authentication, a trusted device or trusted phone number helps verify your identity when you sign in to a new device or browser.
What is two-factor authentication and is it safe
Two-factor authentication (2FA) is a security measure that requires consumers two factors to verify their digital identity. Meaning, it does not grant access if the user cannot produce the right username and password, both unique to the individual.
What’s the main disadvantage of two-factor authentication
Potential downsides to two-factor authentication
Increased login time – Users must go through an extra step to login into an application, adding time to the login process.
What are the pros and cons of using two-factor authentication
The main advantage of two-factor authentication is the increased login security. As for the shortcomings, the main two being the increase in the time of entry into the system and the risk of losing the physical media serving to pass one of the authentication steps (mobile phone, U2F key, OTP-token).
What are three examples of two-factor authentication
What is two-factor authenticationSomething you know, like a password or PIN.Something you have, like your ATM card, or your phone.Something you are, like a fingerprint or voice print.
What triggers two-factor authentication
The three factors that can be used for two-factor authentication are something you know (like a password), something you have (like a bank card), and something you are (like face ID). 2FA requires two of these three factors. MFA may use all three — or even GPS tracking to confirm your physical location.
What is an example of 2 factor authentication
Examples of Two Factor Authentication
When you use your credit card and are prompted for your billing zip code, that's 2FA in action. Knowledge factors like your zip code may also be passwords or a personal identification number (PIN).
What is the potential downside of the two-factor authentication
Potential downsides to two-factor authentication
Increased login time – Users must go through an extra step to login into an application, adding time to the login process.
Can your account be hacked after two-factor authentication
The best way to protect yourself from hackers is to develop a healthy amount of scepticism. If you carefully check websites and links before clicking through and also use 2FA, the chances of being hacked become vanishingly small. The bottom line is that 2FA is effective at keeping your accounts safe.
What is better security than two-factor authentication
MFA is more secure than 2FA. But many companies still use 2FA for two reasons. One, it's cheaper and easier to setup. Most software suites support 2FA, but not all of them support MFA.
Which is better a password or two-factor authentication
Unfortunately, passwords are not very secure. On the other hand, Two-Factor Authentication (2FA) is a much more secure form of authentication. 2FA combines a password with an extra layer of security. The extra layer of security in 2FA is something you have (e.g., smartphone) or something you are (e.g., fingerprint).
What is better than 2 factor authentication
MFA is more secure than 2FA. But many companies still use 2FA for two reasons. One, it's cheaper and easier to setup. Most software suites support 2FA, but not all of them support MFA.
What is the strongest form of two-factor authentication
The strongest level of 2FA online account protection and the best phishing attack prevention is a physical security key. The key is a small device that can be added to a keychain and then plugged into a computer's USB port. This is as close to 100% online account protection as is currently possible.
Which 2 are most often used for 2 factor authentication
Two-factor authentication methods rely on a user providing a password as the first factor and a second, different factor — usually either a security token or a biometric factor, such as a fingerprint or facial scan.
Is two-factor authentication automatically on
If you create a new Apple ID on a device with iOS 13.4, iPadOS 13.4, macOS 10.15. 4, or later, your account automatically uses two-factor authentication. If you previously created an Apple ID account without two-factor authentication, you can turn on its extra layer of security at any time.
Which is the most secure authentication factor
Most Secure: Hardware Keys
Source. External hardware keys, like Yubikeys, are among the strongest authentication factors available. Also called FIDO keys, they generate a cryptographically secure MFA authentication code at the push of a button.
Can people get around 2 factor authentication
Tech-savvy attackers can even bypass two-factor authentication without knowing the victim's login credentials. Man-in-the-middle (MiTM) attacks describe the phenomenon of a third party, also known as a man-in-the-middle, intercepting the communication between two systems.
How will I know if my account has been hacked
You get signed out of your online accounts (social media, email, online banking, etc.), or you try to log in and discover your passwords don't work anymore. You receive emails or text messages about login attempts, password resets, or two-factor authentication (2FA) codes that you didn't request.
Which is the safest authentication method
A security best practice is to combine multiple forms of user authentication into a multifactor authentication (MFA) protocol. And there's a reason it's not called multi-method authentication. The goal of MFA is to pull from two or more factors so a threat actor can't gain access using a single attack vector.
Which is the safest authentication mode
Wi-Fi Protected Access II (WPA2) — introduced in 2004 — remains the most popular wireless security protocol. It uses the Counter Mode Cipher Block Chaining Message Authentication Code Protocol (CCMP) based on the Advanced Encryption Standard (AES) encryption algorithm for stronger security measures.
Which is the safest authentication type
CategoriesThe Three Types of Authentication Factors.Least Secure: Passwords.More Secure: One-time Passwords.More Secure: Biometrics.Most Secure: Hardware Keys.Most Secure: Device Authentication and Trust Factors.
What is an example of two-factor authentication
Examples of Two Factor Authentication
When you use your credit card and are prompted for your billing zip code, that's 2FA in action. Knowledge factors like your zip code may also be passwords or a personal identification number (PIN).
Which type of authentication mode is not recommended
If non-authentication is used, any user can be successfully authenticated without the need of entering the user name and password. Therefore, you are not advised to use non-authentication for device or network security purposes.
