the approach to managing cybersecurity risks. It focuses on five core functions: Identify, Protect, Detect, Respond, and Recover. These functions help organizations assess and prioritize their cybersecurity risks, implement appropriate safeguards, monitor for any potential threats, respond quickly to any incidents, and recover from any attacks or breaches.
What are some popular security frameworks used in IT security? Some popular security frameworks used in IT security include the National Institute of Standards and Technology (NIST) Cybersecurity Framework, ISO/IEC 27001, COBIT (Control Objectives for Information and Related Technologies), and the Payment Card Industry Data Security Standard (PCI DSS). These frameworks provide guidelines and best practices for organizations to establish and maintain effective security controls.
How does a security framework help organizations? A security framework helps organizations by providing a structured approach to managing cybersecurity risks. It allows organizations to assess their current security posture, identify vulnerabilities and weaknesses, and implement appropriate measures to mitigate risks. It also helps organizations ensure compliance with relevant laws and regulations, protect sensitive data, and maintain the trust of their customers and stakeholders. Why is it important to have a security framework in place? Having a security framework in place is important because it helps organizations proactively address cybersecurity risks and protect their valuable assets. It provides a systematic and comprehensive approach to managing security, which helps organizations stay ahead of evolving threats and vulnerabilities. It also ensures that security measures are implemented consistently across the organization, reducing the chances of gaps or inconsistencies in security controls. What are some common challenges organizations face when implementing a security framework? Some common challenges organizations face when implementing a security framework include limited resources and budget, lack of awareness and understanding of cybersecurity risks, resistance to change, and the complexity of modern IT environments. Organizations may also face challenges in aligning their security framework with existing business processes and ensuring consistent implementation and enforcement of security controls. How can organizations ensure the effectiveness of their security framework? Organizations can ensure the effectiveness of their security framework by regularly reviewing and updating their security policies and procedures, conducting regular risk assessments and vulnerability scans, monitoring for any potential security incidents or breaches, and implementing appropriate response and recovery plans. It is also important for organizations to provide ongoing training and awareness programs for employees to ensure they are equipped with the necessary knowledge and skills to handle security threats. How can organizations measure the effectiveness of their security framework? Organizations can measure the effectiveness of their security framework by implementing key performance indicators (KPIs) and metrics to track the performance of their security controls, incident response time, and the level of compliance with relevant security standards and regulations. Regular audits and assessments can also be conducted to evaluate the organization’s overall security posture and identify any areas for improvement. How can organizations ensure compliance with regulations using a security framework? Organizations can ensure compliance with regulations using a security framework by mapping the requirements of relevant regulations to the controls and processes outlined in the framework. By implementing the recommended security controls and practices, organizations can demonstrate their adherence to regulatory requirements and reduce the risk of penalties or legal consequences. Regular audits and assessments can also be conducted to ensure ongoing compliance and identify any gaps or areas for improvement. How can organizations align their security framework with their business objectives? Organizations can align their security framework with their business objectives by conducting a thorough assessment of their business goals, risks, and priorities. The security framework should be tailored to address the specific needs and challenges of the organization, taking into account its industry, size, and operating environment. Regular communication and collaboration between the IT security team and the business stakeholders is also crucial to ensure that security measures support and enable the organization’s overall success. Can small businesses benefit from implementing a security framework? Absolutely. Small businesses can greatly benefit from implementing a security framework as it helps them identify and address their unique cybersecurity risks and vulnerabilities. By implementing appropriate security controls and practices, small businesses can protect their sensitive data, maintain the trust of their customers, and avoid costly data breaches or regulatory penalties. It also helps small businesses demonstrate their commitment to cybersecurity to potential clients or partners, which can be a competitive advantage in today’s digital landscape. How can organizations ensure the ongoing effectiveness of their security framework? Organizations can ensure the ongoing effectiveness of their security framework by continuously monitoring and evaluating their security posture, conducting regular risk assessments and vulnerability scans, and staying up-to-date with the latest cybersecurity threats and trends. It is also important to regularly review and update security policies and procedures, provide ongoing training and awareness programs for employees, and engage in proactive threat intelligence and incident response activities. By taking a proactive and comprehensive approach to cybersecurity, organizations can continuously enhance their security framework and stay ahead of emerging threats. How can organizations justify the investment in implementing a security framework? Organizations can justify the investment in implementing a security framework by considering the potential costs and consequences of a data breach or security incident. The financial and reputational damage caused by such incidents can far exceed the cost of implementing and maintaining a robust security framework. Additionally, organizations may be required to comply with industry-specific security regulations or contractual obligations that mandate the implementation of security controls. Ultimately, investing in a security framework is an essential step towards protecting the organization’s assets, reputation, and long-term viability. What are some best practices for implementing a security framework? Some best practices for implementing a security framework include conducting a thorough assessment of the organization’s cybersecurity risks and vulnerabilities, involving top management and key stakeholders in the decision-making process, establishing clear roles and responsibilities for implementing and maintaining security controls, providing ongoing training and awareness programs for employees, regularly evaluating and updating security policies and procedures, and engaging in continuous monitoring and improvement of security controls. It is also important to stay updated with the latest cybersecurity trends and best practices and adapt the security framework as needed to address emerging threats. 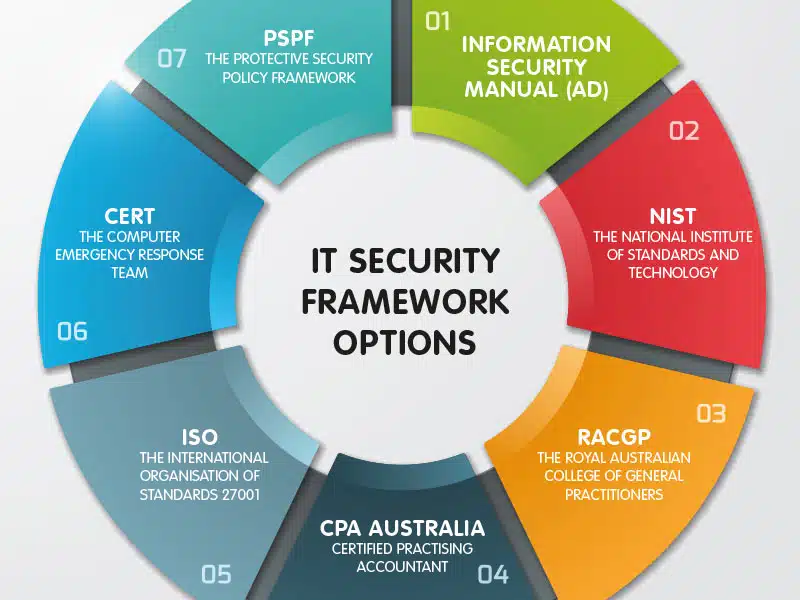
What is meant by a security framework
A security framework defines policies and procedures for establishing and maintaining security controls. Frameworks clarify processes used to protect an organization from cybersecurity risks. They help IT security professionals keep their organization compliant and insulated from cyber threats.
Cached
What is the objective of IT security framework
The framework aims to identify the areas within a business enterprise that are most at risk for data breaches and other compromising activity; and then to implement policies, procedures, and other controls to reduce those risks to acceptable levels.
Cached
What is a framework in cyber security
Cyber security frameworks are sets of documents describing guidelines, standards, and best practices designed for cyber security risk management. The frameworks exist to reduce an organization's exposure to weaknesses and vulnerabilities that hackers and other cyber criminals may exploit.
Cached
What does a security framework look like
A security framework is a compilation of state-mandated and international cybersecurity policies and processes to protect critical infrastructure. It includes precise instructions for companies to handle the personal information stored in systems to ensure their decreased vulnerability to security-related risks.
What are the three pillars of security framework
The CIA triad refers to an information security model made up of the three main components: confidentiality, integrity and availability. Each component represents a fundamental objective of information security.
What are the four pillars of information security framework
Knowledge and awareness of cybercrime threats, information security, technology, and legal requirements. Protection of computing devices. Protection of data.
What are the components of information security framework
The Cybersecurity Framework consists of three main components: the Core, Implementation Tiers, and Profiles. The Framework Core provides a set of desired cybersecurity activities and outcomes using common language that is easy to understand.
What is the framework for IT security risk management
The NIST CSF framework provides a comprehensive set of best practices that standardize risk management. It defines a map of activities and outcomes related to the core functions of cybersecurity risk management—protect, detect, identify, respond, and recover.
What is NIST security framework
The Framework is voluntary. It gives your business an outline of best practices to help you decide where to focus your time and money for cybersecurity protection. You can put the NIST Cybersecurity Framework to work in your business in these five areas: Identify, Protect, Detect, Respond, and Recover.
What are the key elements of Cybersecurity Framework
The Cybersecurity Framework consists of three main components: the Core, Implementation Tiers, and Profiles. The Framework Core provides a set of desired cybersecurity activities and outcomes using common language that is easy to understand.
What are the 7 elements of security model
The 7 Elements of Human Security are defined by the United Nations as: Economic, Environmental, Food, Health, Political, Personal and Community. We design projects and initiatives with our partners that holistically address these areas of Human Security.
What are the 5 elements of security
It relies on five major elements: confidentiality, integrity, availability, authenticity, and non-repudiation.
What are the 5 pillars of security
Understand the 5 PillarsPhysical Security. Physical Security relates to everything that is tangible in your organization.People Security. Humans typically present the greatest threat to an organisation's security, be it through human error or by malicious intent.Data Security.Infrastructure Security.Crisis Management.
What are the 5 new elements of the information security governance framework
The five key functions in the framework are:Identify.Protect.Detect.Respond.Recover.
What are the 3 core elements of information security
The CIA triad refers to an information security model made up of the three main components: confidentiality, integrity and availability.
What are the five major components of IT security management
It relies on five major elements: confidentiality, integrity, availability, authenticity, and non-repudiation.
What are the main components of the risk IT framework
The 5 Components of RMF. There are at least five crucial components that must be considered when creating a risk management framework. They include risk identification; risk measurement and assessment; risk mitigation; risk reporting and monitoring; and risk governance.
What are the 5 components of NIST framework
The core competencies of NIST are aligned with the 5 NIST functions which are Identify, Protect, Detect, Respond and Recover. These five security functions are ever-increasingly relevant to organizations in any sector or community.
What is the difference between NIST framework and ISO 27001
ISO 27001 is an international standard to improve an organization's information security management systems, while NIST CSF helps manage and reduce cybersecurity risks to their networks and data. Both l ISO 27001 and NIST CSF effectively contribute to a stronger security posture.
What are the 5 phases cybersecurity framework
Although The 5 NIST functions, namely Protect, Identify, Detect, Respond, and Recover are similar to other top security frameworks, they contain a number of critical procedures that help minimize the effect of cybersecurity incidents on organizations of any size.
What are the 4 C’s in security
These four layers are Code security, Container security, Cluster security, and Cloud security. Let's take a deep dive into each of the C's to understand them better and also answer some of the most asked questions about the 4C's.
What are the six pillars of security
I will now discuss these:Risk and compliance.External threat and vulnerability management.Internal threat and vulnerability management.Third party risk management.User risk management.Incident response and disaster recovery plans.
What are the 7 P’s in security
The fundamental SIA threat and risk assessment training encourages the CPO to use the seven Ps of principal threat profiling: people, places, personality, prejudices, personal history, political/religious views, and private lifestyle to look for direct and indirect threats.
What are the 4 P’s in security
In general, Information Security professionals suggest that protecting sensitive data requires a combination of people, processes, polices, and technologies.
What are the 7 elements of security
The 7 Elements of Human Security are defined by the United Nations as: Economic, Environmental, Food, Health, Political, Personal and Community.