gs and perimeters of a property and may not be effective against internal threats. Additionally, perimeter intrusion detection systems can be expensive to install and maintain.
In conclusion, a perimeter security alarm system is an important security measure that uses various devices to monitor the boundaries of a property and detect unauthorized access. It is essential for property owners who want to ensure the security of their perimeter and deter unwanted visitors. However, there are drawbacks to relying solely on perimeter-based security, as it may not be effective against internal threats and can be expensive to implement. It is important to consider a comprehensive security approach that includes both physical and digital security measures to protect assets, information, and people.
1. What is a perimeter security alarm?
– A perimeter security alarm is a system that uses sensors, cameras, and other devices to monitor a property for unauthorized access. It can sound an alarm when triggered.
2. What is an example of perimeter security?
– Perimeter security can include video analytics, access control, fence sensors, security management, and physical barriers like fences and gates.
3. Who would need a perimeter security system?
– Property owners who want to ensure the security of their perimeter and deter unwanted visitors would benefit from a perimeter security system.
4. What is the difference between perimeter security and physical security?
– Physical security focuses on controlling access to a building or area, while perimeter security specifically monitors the boundaries of a property.
5. What are the two types of perimeter security?
– The two types of barriers used for perimeter protection are natural barriers and structural barriers.
6. Why do you need perimeter security?
– Perimeter security is the first line of defense to protect assets, information, and people using advanced technology.
7. What are the drawbacks of perimeter-based security?
– Perimeter-based security can be static in nature and may not be effective against internal threats that have migrated outside the traditional LAN boundary.
8. What are the disadvantages of a perimeter intrusion detection system?
– A major disadvantage of a perimeter intrusion detection system is that it primarily protects only the openings and perimeters of a property and may not be effective against internal threats. It can also be expensive to install and maintain.
9. How can a perimeter security alarm system be accessed?
– A perimeter security alarm system can be accessed physically or remotely through a control panel.
10. Can perimeter security systems be used in combination with other security measures?
– Yes, perimeter security systems can be used in combination with security lighting and other physical security measures to enhance overall security.
What is a perimeter security alarm
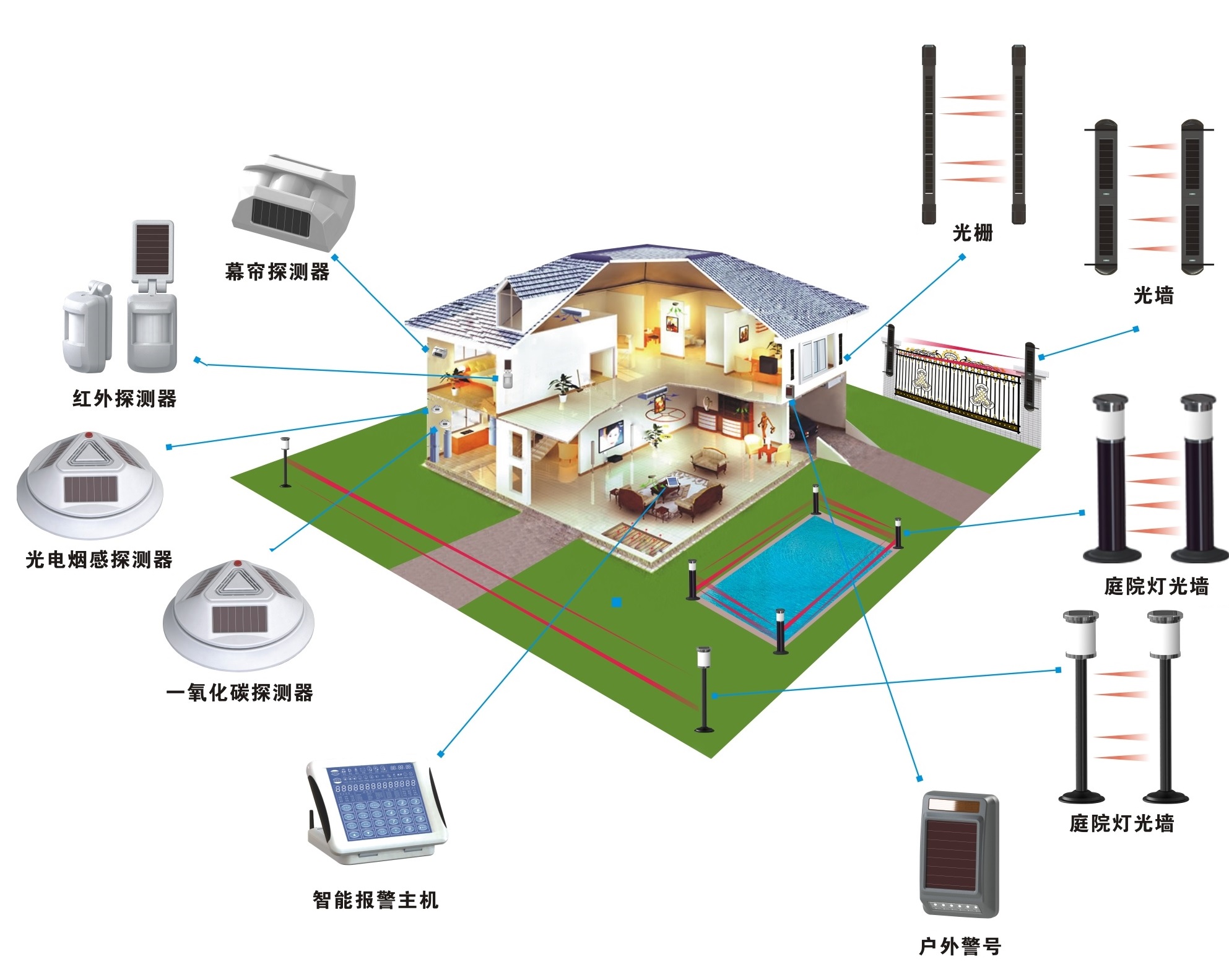
What is a Perimeter Alarm System A perimeter alarm system is an essential security measure that uses sensors, cameras, and other devices to monitor your property for unauthorized access. The control panel can be accessed physically or remotely and can sound a high-decibel siren/alarm when triggered.
Cached
What is an example of perimeter security
Perimeter security can include video analytics, video management, access control, fence sensors, buried sensors, above-ground sensors, security management, and physical security measures such as fences, gates, lighting, and barriers.
Who would need a perimeter security system
Many property owners use this type of system to ensure that their perimeter remains secure. These detection systems can be used around fences and walls. They are also used to cover a large area of the outside perimeter. Some systems can even be used in combination with security lighting to deter any unwanted visitors.
Cached
What is the difference between perimeter security and physical security
Physical security is the most basic and important part of information security. It is not just about locking the door but also knowing who has access to what, when, where and how. Physical security perimeters are used to identify the physical boundaries of a building or area and control access to it.
What are the two types of perimeter security
There are two types of barriers used for perimeter protection: natural barriers and structural barriers.
Why do you need perimeter security
Perimeter security is the first line of defense to protect your assets, information, and people using advanced technology. Just as the human skin protects the body against the external environment and infections, the perimeter security system is designed to keep away unauthorized intrusion in your property.
What are the drawbacks of perimeter based security
The biggest problem with perimeter-based security is that it is static in nature. Over the years, apps, devices and users have migrated outside the traditional LAN boundary and, thus, are untrusted from an architectural standpoint.
What are the disadvantages of perimeter intrusion detection system
The major disadvantage is that it protects only the openings. If the burglar bursts through a wall, comes through the ventilation system, or stays behind after closing, perimeter protection is useless. 1. Door switches.
What is the most common form of perimeter security devices
Lighting
Lighting is the most common form of perimeter security devices or mechanisms. Your entire site should be clearly lit. This provides for easy identification of personnel and makes it easier to notice intrusions.
What is the primary issue with a perimeter-based network security
The primary issue with a perimeter-based network security strategy in which countermeasures are deployed at a handful of well-defined ingress and egress points to the network is that it relies on the assumption that everything on the internal network can be trusted.
What are two types of perimeter security systems
The different forms of perimeter security include:Perimeter protection.Perimeter CCTV surveillance.Perimeter detection systems.Access control.
What are the drawbacks of perimeter-based security
The biggest problem with perimeter-based security is that it is static in nature. Over the years, apps, devices and users have migrated outside the traditional LAN boundary and, thus, are untrusted from an architectural standpoint.