Summary of the Article:
What information will encryption protect
Encryption helps provide data security for sensitive information. It takes plain text, like a text message or email, and scrambles it into an unreadable format called “ciphertext.” This protects the confidentiality of digital data stored on computer systems or transmitted through a network like the internet.
What are the 3 types of data that can be encrypted
DES, AES, and RSA are the three primary encryption types. 3DES, a more recent block cipher, uses three independent 56-bit keys for triple protection.
Does all data need to be encrypted
Ultimately, it is up to the user to decide whether their data should be encrypted. However, it is generally recommended to use encryption to protect both the data and oneself.
Why should information be encrypted
Encryption helps protect private information, sensitive data, and enhances the security of communication between client apps and servers. Even if unauthorized access occurs, encrypted data remains unreadable.
When should you use encryption
Encryption is commonly used to protect data in transit and data at rest. It is employed when using ATMs, making online purchases, or transmitting sensitive information online.
What is an example of encrypted data
Websites that transmit credit card and bank account numbers often encrypt this information to prevent identity theft and fraud.
What is an example of encrypted information
Websites that transmit credit card and bank account numbers often encrypt this information to prevent identity theft and fraud.
What is the most common data encryption
The most common data encryption is Advanced Encryption Standard (AES).
Questions:
- What information will encryption protect?
- What are the three types of data that can be encrypted?
- Does all data need to be encrypted?
- Why should information be encrypted?
- When should you use encryption?
- What is an example of encrypted data?
- What is an example of encrypted information?
- What is the most common data encryption?
Answers:
- Encryption helps protect sensitive information and ensures data security.
- The three types of data that can be encrypted are DES, AES, and RSA.
- While it is ultimately up to the user, it is generally recommended to encrypt data for added protection.
- Information should be encrypted to protect privacy, enhance security, and prevent unauthorized access.
- Encryption should be used when transmitting data online, making online purchases, or using ATMs.
- An example of encrypted data is the transmission of credit card and bank account numbers on secure websites.
- Encrypted information often includes credit card and bank account numbers transmitted through secure websites.
- The most common data encryption is Advanced Encryption Standard (AES).
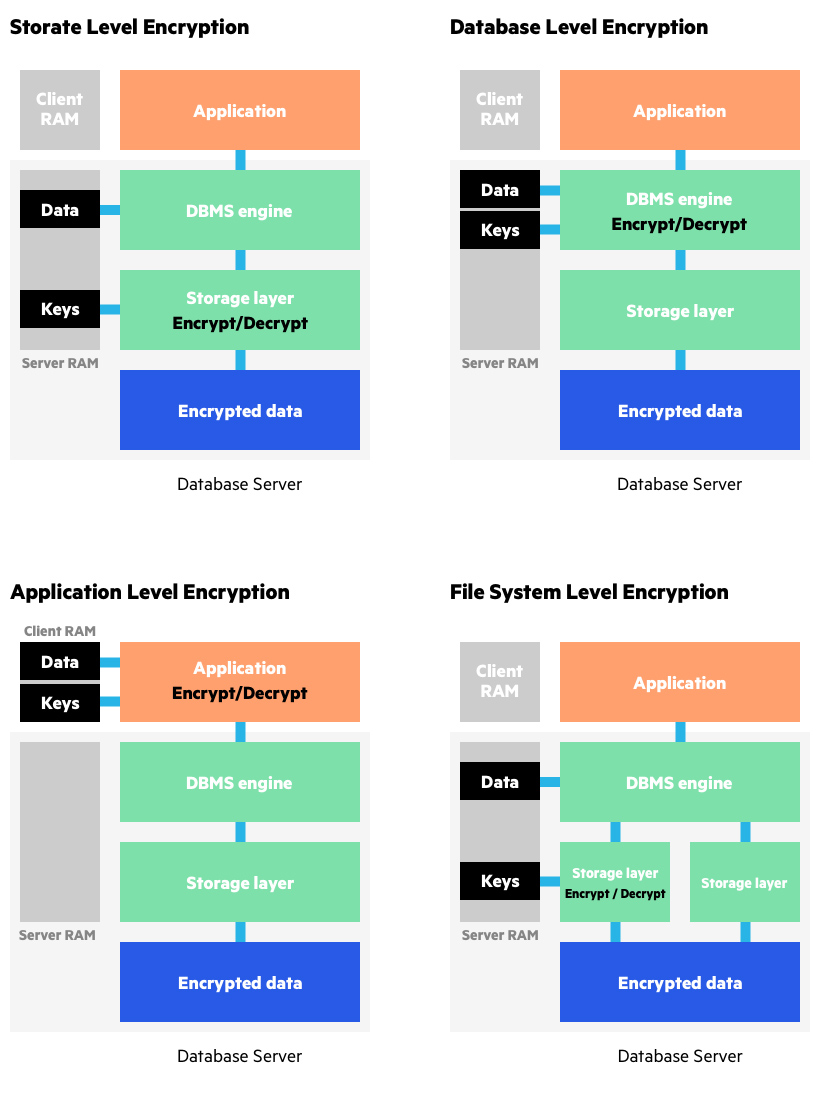
What information will encryption protect
It helps provide data security for sensitive information. Encryption takes plain text, like a text message or email, and scrambles it into an unreadable format — called "ciphertext." This helps protect the confidentiality of digital data stored on computer systems or transmitted through a network like the internet.
What are the 3 types of data that can be encrypted
DES, AES, and RSA are the three primary encryption types. A more recent 3DES is a block cipher that is still in use today. The Triple Data Encryption Standard (3DES) does exactly what its name says. For triple protection, it employs three independent 56-bit keys rather than a single 56-bit key.
Cached
Does all data need to be encrypted
Final Thoughts. It is ultimately up to you, the user, on whether or not you feel your data should be encrypted. In most cases it is best to err on the side of caution and use encryption to not only protect the data but protect yourself and the university.
Why should information be encrypted
It helps protect private information, sensitive data, and can enhance the security of communication between client apps and servers. In essence, when your data is encrypted, even if an unauthorized person or entity gains access to it, they will not be able to read it.
Cached
When should you use encryption
Encryption is commonly used to protect data in transit and data at rest. Every time someone uses an ATM or buys something online with a smartphone, encryption is used to protect the information being relayed.
What is an example of encrypted data
Encryption is an important way for individuals and companies to protect sensitive information from hacking. For example, websites that transmit credit card and bank account numbers encrypt this information to prevent identity theft and fraud.
What is an example of encrypted information
Encryption is an important way for individuals and companies to protect sensitive information from hacking. For example, websites that transmit credit card and bank account numbers encrypt this information to prevent identity theft and fraud.
What is the most common data encryption
Advanced Encryption Standard (AES)
1. Advanced Encryption Standard (AES) The Advanced Encryption Standard is a symmetric encryption algorithm that is the most frequently used method of data encryption globally. Often referred to as the gold standard for data encryption, AES is used by many government bodies worldwide, including in the U.S.
When should you encrypt data
When should encryption be used Any time data is stored, it should be encrypted to ensure security. For instance, this could be on a removable storage drive or your computer's hard drive. Responsible organizations will encrypt any data they store.
What type of data is not encrypted
Encrypted data is commonly referred to as ciphertext, while unencrypted data is called plaintext.
What are 3 purposes of encryption
Not only does it keep the data confidential, but it can authenticate its origin, ensure that data has not changed after it was sent, and prevent senders from denying they sent an encrypted message (also known as nonrepudiation).
What is the most common use for encryption
1. Advanced Encryption Standard (AES) The Advanced Encryption Standard is a symmetric encryption algorithm that is the most frequently used method of data encryption globally. Often referred to as the gold standard for data encryption, AES is used by many government bodies worldwide, including in the U.S.
What is simple encryption examples
An example of basic encryption is swapping each letter with the one that holds its opposite position in the alphabet. That means “a” is replaced with “z,” “b” with “y” and so on.
What is the most common encryption
Advanced Encryption Standard (AES)
1. Advanced Encryption Standard (AES) The Advanced Encryption Standard is a symmetric encryption algorithm that is the most frequently used method of data encryption globally. Often referred to as the gold standard for data encryption, AES is used by many government bodies worldwide, including in the U.S.
What is an example of data encryption in everyday life
Cryptography in Everyday LifeAuthentication/Digital Signatures. Authentication and digital signatures are a very important application of public-key cryptography.Time Stamping.Electronic Money.Secure Network Communications.Anonymous Remailers.Disk Encryption.
What situations would you use encryption and why
Encryption is commonly used to protect data in transit and data at rest. Every time someone uses an ATM or buys something online with a smartphone, encryption is used to protect the information being relayed.
What are examples of data encryption
Encryption is an important way for individuals and companies to protect sensitive information from hacking. For example, websites that transmit credit card and bank account numbers encrypt this information to prevent identity theft and fraud.
What are the 2 types of encryption and which one is better to be used
There are two types of encryption in widespread use today: symmetric and asymmetric encryption. The name derives from whether or not the same key is used for encryption and decryption.
What are some examples of where encryption is used
Encryption is commonly used to protect data in transit and data at rest. Every time someone uses an ATM or buys something online with a smartphone, encryption is used to protect the information being relayed.
How do I encrypt my personal data
The two most widely used methods for data encryption are public key, also known as asymmetric encryption, and private key, or symmetric encryption. Both rely on key pairs but differ in how the sending and receiving parties share the keys and handle the encrypt/decrypt process.
What is the common use of encryption
Encryption is commonly used to protect data in transit and data at rest. Every time someone uses an ATM or buys something online with a smartphone, encryption is used to protect the information being relayed.
When should data be encrypted
In broad terms, there are two types of data you should encrypt: personally identifiable information and confidential business intellectual property. Personally Identifiable Information (PII)PII includes any kind of information another person can use to uniquely identify you.
What are some examples of encryption
Examples of encryption algorithmsDES encryption.3DES encryption.AES encryption.RSA encryption.Twofish encryption.RC4 encryption.Encryption helps maintain data integrity.Encryption helps organizations adhere to regulations.
In which of the following scenarios must you use encryption when sending information
If you send the data unencrypted there is a risk that if it was lost or stolen any third party could gain unauthorised access to the personal data. It is therefore necessary for you to consider encryption as a means of adding an additional layer of protection.
What happens to your data when it is encrypted
Data encryption converts data from a readable, plaintext format into an unreadable, encoded format: ciphertext. Users and processes can only read and process encrypted data after it is decrypted. The decryption key is secret, so it must be protected against unauthorized access.