Summary of DDoS Attacks
1. DDoS Attack Meaning: DDoS Attack stands for “Distributed Denial-of-Service (DDoS) Attack.” It is a cybercrime where an attacker floods a server with internet traffic to prevent users from accessing connected online services and sites.
2. First D in DDoS: A distributed denial-of-service (DDoS) attack is a malicious attempt to disrupt the normal traffic of a targeted server, service, or network by overwhelming it with a flood of Internet traffic.
3. Signs of DDoS Attack: If you’re experiencing the following signs, you might be under a DDoS attack: sudden influx of requests to a specific endpoint or page, flood of traffic from a single IP or range of IP addresses, or sudden spike of traffic occurring at regular intervals or unusual time frames.
4. Types of DDoS Attacks: The three broad types of DDoS attacks are application layer attacks, protocol attacks, and volumetric attacks.
5. Difference Between DoS and DDoS Attacks: A denial-of-service (DoS) attack floods a server with traffic, while a distributed denial-of-service (DDoS) attack uses multiple computers or machines to flood a targeted resource.
6. DoS vs DDoS: A DoS attack floods a server with TCP and UDP packets from a single computer, whereas a DDoS attack involves multiple systems targeting a single system with a DoS attack, bombarding the targeted network with packets from multiple locations.
7. Strongest DDoS Attack Ever: In June 2022, Google successfully mitigated what could have been the largest DDoS attack in the world, peaking at 46 million requests per second, compared to the number of daily requests received by Wikipedia.
8. Hardest Hitting DDoS Attack: GitHub, a popular online code management service, faced one of the largest verifiable DDoS attacks on record, impacting millions of developers.
Unique Questions:
1. How does a DDoS Attack work? A DDoS attack overwhelms a target with a high volume of traffic, disrupting its normal functioning and preventing legitimate users from accessing the targeted resource.
2. What are the motivations behind DDoS attacks? Motivations for DDoS attacks can vary, including revenge, ideological conflicts, competition sabotage, ransom demands, or simply disruption for fun.
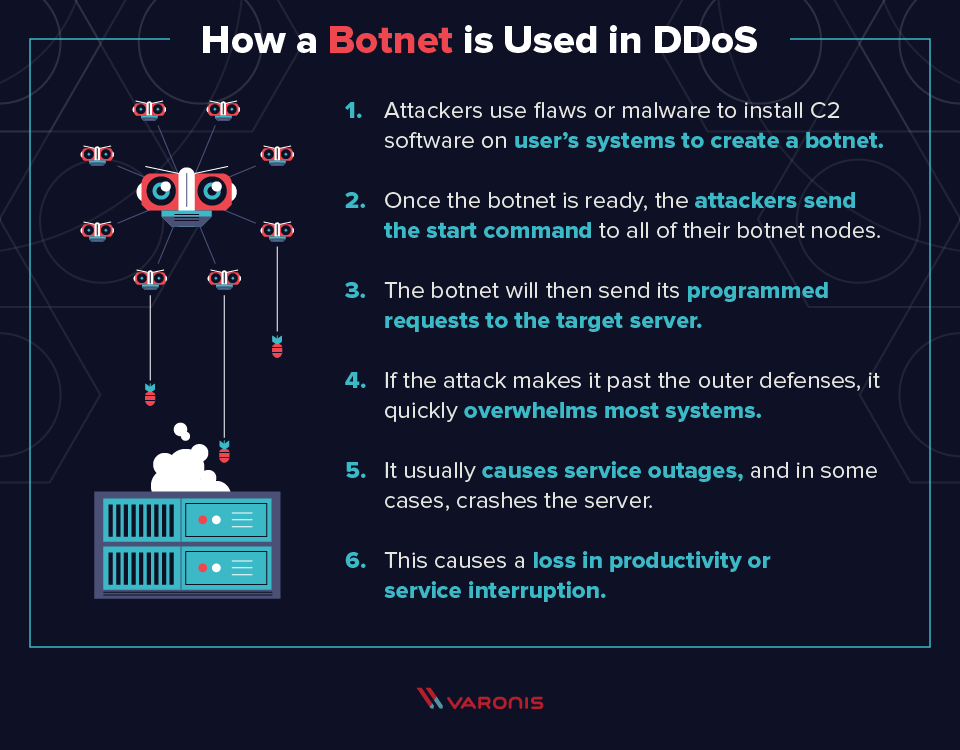
3. How do attackers launch a DDoS attack? Attackers often use botnets, a network of compromised computers, to generate a massive volume of traffic directed at the target. These botnets can be created through malware infections or by exploiting vulnerable systems.
4. How can organizations defend against DDoS attacks? Organizations can employ various strategies such as implementing robust network security measures, using traffic filtering systems, employing load balancers, and partnering with DDoS mitigation service providers.
5. What are the legal consequences of launching a DDoS attack? Launching a DDoS attack is illegal in most jurisdictions and can result in severe penalties, including imprisonment and hefty fines.
6. How do DDoS attacks impact businesses? DDoS attacks can lead to significant financial losses for businesses, including revenue loss from disrupted online services, additional expenses to mitigate the attack, reputational damage, and loss of customer trust.
7. Are there any preventive measures organizations can take to minimize the risk of DDoS attacks? Organizations can take preventive measures such as regularly updating software and systems, implementing strong access controls, monitoring network traffic for any unusual patterns, and conducting regular vulnerability assessments.
8. Can smaller organizations also be targeted by DDoS attacks? Yes, smaller organizations can also be targeted by DDoS attacks, as attackers may target any online service or resource that they perceive as vulnerable or may have ulterior motives.
9. What are the impacts of DDoS attacks on individuals? Individuals may experience disrupted access to online services and websites, loss of sensitive personal information if targeted platforms are compromised, and potential financial scams exploiting the chaos caused by DDoS attacks.
10. Are IoT devices vulnerable to being used in DDoS attacks? Yes, IoT (Internet of Things) devices can be vulnerable and exploited by attackers to participate in DDoS attacks, as many IoT devices lack robust security measures.
What does the D in DDoS stand for
Distributed Denial-of-Service
DDoS Attack Meaning
DDoS Attack means "Distributed Denial-of-Service (DDoS) Attack" and it is a cybercrime in which the attacker floods a server with internet traffic to prevent users from accessing connected online services and sites.
Cached
What is the first D in DDoS
A distributed denial-of-service (DDoS) attack is a malicious attempt to disrupt the normal traffic of a targeted server, service or network by overwhelming the target or its surrounding infrastructure with a flood of Internet traffic.
Am I getting DDoS D
If you're experiencing one or more of these signs, you might be under DDoS attack: A sudden influx of requests to a specific endpoint or page. A flood of traffic that originates from a single IP or range of IP addresses. A sudden spike of traffic that occurs at regular intervals or at unusual time frames.
What are the 3 types of DDoS attacks
Three broad types of DDoS attacks are as follows.Application layer attacks. The application layer is where the server generates the response to an incoming client request.Protocol attacks.Volumetric attacks.
Cached
What does DDoS mean and DoS
distributed denial-of-service
What Is the Difference Between DoS Attacks and DDoS Attacks A denial-of-service (DoS) attack floods a server with traffic, making a website or resource unavailable. A distributed denial-of-service (DDoS) attack is a DoS attack that uses multiple computers or machines to flood a targeted resource.
What is DDS vs DDoS
A DoS attack is a denial of service attack where a computer is used to flood a server with TCP and UDP packets. A DDoS attack is where multiple systems target a single system with a DoS attack. The targeted network is then bombarded with packets from multiple locations.
What is the strongest DDoS ever
According to The Record, Google stifled what would have been the largest DDoS attack in the world in June of 2022. The attack peaked at 46 million requests per second, which was compared to the number of requests Wikipedia receives every day.
What is the hardest hitting DDoS
One of the largest verifiable DDoS attacks on record targeted GitHub, a popular online code management service used by millions of developers. This attack reached 1.3 Tbps, sending packets at a rate of 126.9 million per second. The GitHub attack was a memcached DDoS attack, so there were no botnets involved.
Do you go to jail for DDoS
The use of booter and stresser services to conduct a DDoS attack is punishable under the Computer Fraud and Abuse Act (18 U.S.C. § 1030), and may result in any one or a combination of the following consequences: Seizure of computers and other electronic devices. Arrest and criminal prosecution.
Can DDoS hack you
A DDoS attack isn't the same thing as hacking, although the two can be linked; the perpetrators aren't attempting to access your website's files or admin, but instead, they cause it to crash or become vulnerable due to the volume of requests.
What are the 4 types of DoS attacks
Types of DOS:Volumetric attacks: This is an Attack where the entire bandwidth of a network is consumed so the authorized clients will not be able to get the resources.Syn flooding:Fragmentation attacks:TCP-State exhaustion attack:Application Layer Attacks:Plashing:
What’s the full meaning of DoS
disk operating system
A DOS, or disk operating system, is an operating system that runs from a disk drive.
Is DDoS a type of DoS
What Is the Difference Between DoS Attacks and DDoS Attacks A denial-of-service (DoS) attack floods a server with traffic, making a website or resource unavailable. A distributed denial-of-service (DDoS) attack is a DoS attack that uses multiple computers or machines to flood a targeted resource.
What is DDS in cyber security
DDS: An Open Standard for Real-Time Applications
The Object Management Group Data Distribution Service is a middleware protocol and API standard that provides data connectivity, extreme reliability and a scalable architecture to meet real-time system requirements.
What is DDS in security
Deeply discounted security (DDS) definition.
Can you go to jail for DDoS
The use of booter and stresser services to conduct a DDoS attack is punishable under the Computer Fraud and Abuse Act (18 U.S.C. § 1030), and may result in any one or a combination of the following consequences: Seizure of computers and other electronic devices. Arrest and criminal prosecution.
Is it illegal to DDoS
Participating in Distributed Denial of Service attacks (DDoS) and DDoS-for-hire services is illegal. The FBI and other law enforcement agencies investigate DDoS attacks as cyber crimes.
Is it illegal to DDoS a school
DDoSing is an Illegal cybercrime in the United States. A DDoS attack could be classified as a federal criminal offense under the Computer Fraud and Abuse Act (CFAA). The use of booter services and stressers also violates this act.
Is it illegal to DDoS on Xbox
DoS and DDoS attacks are illegal in most regions. In gaming, DoS or DDoS attacks may be used as retaliation when a multiplayer match doesn't go the attacker's way or to gain an edge in the competition. Xbox and game publishers monitor for instances of network manipulation and enforce against these violations.
Can someone DDoS your WIFI
Yes, someone can DDoS you with just your IP address. With your IP address, a hacker can overwhelm your device with fraudulent traffic causing your device to disconnect from the internet and even shut down completely.
Can a DDoS be traced back
Can you trace DDoS attacks DDoS attacks are pretty difficult to trace because most of them are distributed over hundreds and thousands of other devices. Also, those who initiate such attacks usually make an effort not to be found.
What are the 5 types of cyber attacks
What are the 10 Most Common Types of Cyber AttacksMalware.Denial-of-Service (DoS) Attacks.Phishing.Spoofing.Identity-Based Attacks.Code Injection Attacks.Supply Chain Attacks.Insider Threats.
What is Layer 4 DDoS
Layer 3 and Layer 4 DDoS Attacks Layer 3 and Layer 4 DDoS attacks are types of volumetric DDoS attacks on a network infrastructure Layer 3 (network layer) and 4 (transport layer) DDoS attacks rely on extremely high volumes (floods) of data to slow down web server performance, consume bandwidth, and eventually degrade …
What did DoS originally stand for
MS-DOS, in full Microsoft Disk Operating System, the dominant operating system for the personal computer (PC) throughout the 1980s.
What does DoS mean in the US
United States Department of State.