Summary
The 4 D’s in security: The approach to business security consists of four key layers, including deter, detect, delay, and defend.
Key Points:
- Deter: Implement measures to discourage potential threats.
- Detect: Utilize systems and tools to identify any unauthorized access.
- Delay: Create obstacles and delays to prevent immediate breach.
- Defend: Employ strategies to protect against attacks and mitigate damages.
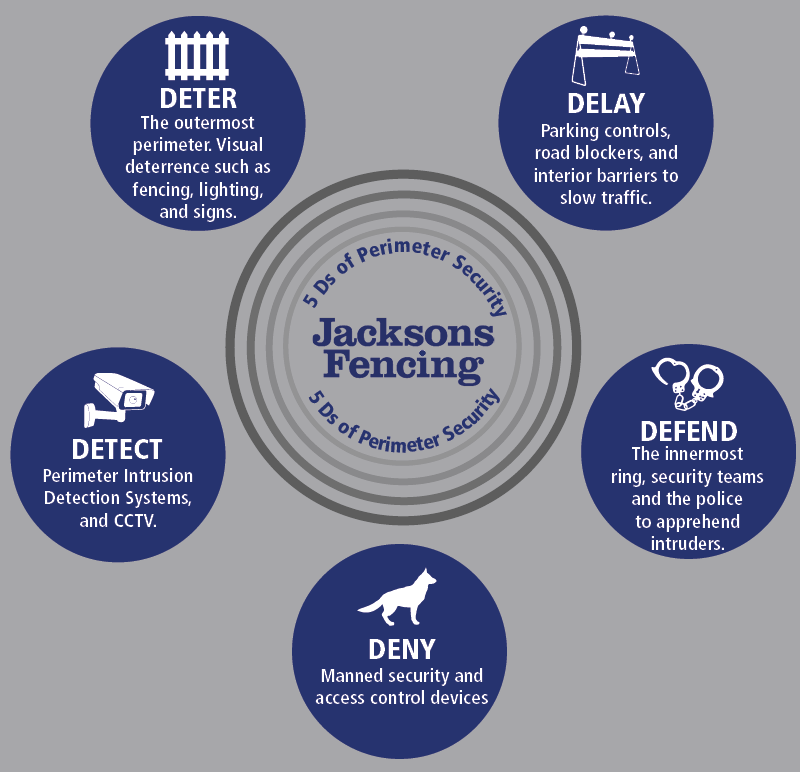
The 5 D’s of security: The 5 D’s of perimeter security (Deter, Detect, Deny, Delay, Defend) work together to prevent unauthorized access and allow for effective response.
The 3 D’s in security: Organizations can reduce the probability of incidents by following the principles of deterrence, detection, and delay.
Deter, Detect, and Defend identity theft: Safeguard your information by shredding documents with personal information, protecting your Social Security number, and avoiding unnecessary exposure.
The D’s of defense: In self-defense, the 5 D’s include deciding not to be a victim, deterring aggression, disrupting attacks, disengaging from dangerous situations, and debriefing afterward.
ABCD security: Asset Based Cyber Defense (ABCD) helps Singaporean SMEs and enterprises secure against cyber threats by utilizing CSA “Be Safe Online” Essentials.
The 7 P’s in security: Principal threat profiling encourages consideration of people, places, personality, prejudices, personal history, political/religious views, and private lifestyle to identify direct or indirect threats.
The 6 D’s of cyber security: Implementing the 6 D’s (Deter, Detect, Defend, Deflect, Document, and Delay) in your cyber-defense strategy helps protect against cyber threats.
Questions and Answers
- What are the 4 D’s in security?
The four D’s in security include deter, detect, delay, and defend. - What are the 5 D’s of perimeter security?
The 5 D’s of perimeter security are deter, detect, deny, delay, and defend. - What are the 3 D’s in security?
The three D’s in security are deter, detect, and delay. - How can you deter, detect, and defend against identity theft?
To safeguard against identity theft, shred financial documents with personal information, protect your Social Security number, and avoid carrying it in your wallet or writing it on checks. - What are the D’s of defense?
The D’s of defense in the context of self-defense are decide, deter, disrupt, disengage, and debrief. - What is ABCD security?
ABCD (Asset Based Cyber Defence) helps Singaporean SMEs and enterprises secure against cyber activity by incorporating CSA “Be Safe Online” Essentials. - What are the 7 P’s in security?
The 7 P’s in security for principal threat profiling are people, places, personality, prejudices, personal history, political/religious views, and private lifestyle. - What are the 6 D’s of cyber security?
The 6 D’s of cyber security are deter, detect, defend, deflect, document, and delay.
What are the 4 D’s in security
While they might not look great on a report card, straight Ds across the board is the goal when it comes to business security. The approach consists of four key layers — deter, detect, delay and defend.
What are the 5 D’s of security
The 5 Ds of perimeter security (Deter, Detect, Deny, Delay, Defend) work on the 'onion skin' principle, whereby multiple layers of security work together to prevent access to your site's assets, giving you the time and intelligence you need to respond effectively.
What are the 3 D’s in security
When your organization is creating a security plan, there are three important steps that need to be considered in order to mitigate risk before an incident occurs. These are the three Ds of security: deter, detect, and delay. The three Ds are a way for an organization to reduce the probability of an incident.
Cached
How do you deter detect and defend identity theft
There are some simple ways to safeguard your information from identity thieves, including: Shred financial documents and paperwork with personal information before you discard them. Protect your Social Security number. Don't carry your Social Security card in your wallet or write your Social Security number on a check.
Cached
What are the Ds of defense
5 D's of Self DefenseDecide. The first step is to decide not to be a victim.Deter. Once you leave an area of safety, it's important to deter and prevent any acts of aggression.Disrupt.Disengage.Debrief.We're Here to Help.
What is ABCD security
Known as Asset Based Cyber Defence, ABCD helps Singaporean SMEs and enterprises in securing against malicious cyber activity by incorporating the CSA “Be Safe Online” Essentials.
What are the 7 P’s in security
The fundamental SIA threat and risk assessment training encourages the CPO to use the seven Ps of principal threat profiling: people, places, personality, prejudices, personal history, political/religious views, and private lifestyle to look for direct and indirect threats.
What are the 6 Ds of cyber security
In this article, we will discuss the 6 D's of cyber security and how you can implement them in your own cyber-defense strategy — Deter, Detect, Defend, Deflect, Document, and Delay. Creating a holistic approach to your cyber-security plan using these six references can drastically reduce your organization's risk.
What do the 3 D’s stand for
Direct, Delegate and Distract
What are the 3 Ds The 3 Ds stands for Direct, Delegate and Distract. These are the three main reactive green dot strategies when intervening in a potential red dot situation.
How do you detect identity theft
Warning signs of ID theftBills for items you did not buy.Debt collection calls for accounts you did not open.Information on your credit report for accounts you did not open.Denials for loan applications.Mail stops coming to – or is missing from – your mailbox.
What can you do to deter identity theft questions
These include:Freeze your credit.Collect mail daily.Review credit card and bank statements regularly.Shred documents containing personal information before disposing of them.Create different passwords for your accounts.Review credit reports annually.Install antivirus software.
What is the difference between deterrence and defence
Deterrence means prevention of war; defence means limiting or ending the war; balance of power means there should be a balance between bigger and smaller countries and alliance building means a coalition of states.
What does DS mean in war
D/D – dishonorable discharge. DS – detached service.
What are the 4 types of ABCD
The following are the four varieties of English alphabets, based on the styles of writing they are used for:Small letters.Capital letters.Cursive letters.Print letters.
What does 4Cs mean in security
4Cs of Cloud Native. Security: Code, Container, Cluster, and Cloud.
What are the 6 Ps of security
These unique functions are known as "the six Ps" (planning, policy, programs, protection, people, and project management).
What are the six pillars of security
I will now discuss these:Risk and compliance.External threat and vulnerability management.Internal threat and vulnerability management.Third party risk management.User risk management.Incident response and disaster recovery plans.
What are the 7 stages of cyber security
7 stages of the cyber attack lifecycleReconnaissance. The preliminary stage of any cyber attack sees the threat actor gathering intelligence and research on their target(s).Weaponisation.Delivery.Exploitation.Installation.Command and control.Actions on objectives.
What are the 7 layers of cyber security
The Seven Layers Of CybersecurityMission-Critical Assets. This is data that is absolutely critical to protect.Data Security.Endpoint Security.Application Security.Network Security.Perimeter Security.The Human Layer.
What are the 4 DS in psychology
In general, the four common features of an abnormality are: deviance, distress, dysfunction, and danger.
What is the 4 DS of psychology
Psychologists often classify behavior as abnormal using 4 D's: deviance, distress, dysfunction, and danger. Providing a straightforward definition of abnormality is tricky because abnormality is relative, but the definition has several primary characteristics.
How do you check if my SSN is being used
To see if someone's using your SSN, check your credit report. You can check it online through AnnualCreditReport.com, the only authorized website for free credit reports. Or you can call their phone number at 1-877-322-8228 to request your free copy.
What are three 3 warning signs of identity theft
8 Warning Signs of Identity TheftUnrecognized bank or credit card transactions.Unfamiliar inquiries on your credit report.Unexpected bills or statements.Unexpected lack of bills or statements.Surprise credit score drop.Denial of loan or credit applications.Calls from debt collectors.
Can someone open a credit card in my name without my Social Security number
An identity thief would have to obtain personal details such as your name, birthdate and Social Security number in order to open a credit card in your name. However, it is a federal crime to do this, and it can result in jail time when the thief is caught for their behavior.
How a person can detect identity theft
Changes in your credit score can indicate identity theft. For example, if someone takes out utility bills in your name and doesn't pay them, your credit score may dip. Checking your credit report from each of the three major credit bureaus Equifax, Experian, and TransUnion can help pinpoint the problem.