Summary of the Article: Types of Information Security
There are two main types of information security: application security and infrastructure security. Application security involves measures taken to protect data from unauthorized access, misuse, and disruption in applications and systems. Infrastructure security focuses on securing the underlying infrastructure and includes cloud security and cryptography. The key points of this article are:
1. Application Security: Measures taken to secure data from unwanted access and disruption to applications and systems.
2. Infrastructure Security: Measures taken to secure the underlying infrastructure, including cloud security and cryptography.
3. Confidentiality: Ensuring that data is only accessible to authorized individuals.
4. Integrity: Ensuring that data is accurate and unaltered.
5. Availability: Ensuring that data and systems are accessible when needed.
6. Developing a security policy to outline the measures and protocols for information security.
Questions and Answers:
1. What are the two types of information security?
The two types of information security are application security and infrastructure security.
2. What are the types of security requirements?
The security requirements include authentication and password management, authorization and role management, audit logging and analysis, network and data security, code integrity and validation testing, cryptography and key management, and data validation and sanitization.
3. What two types of requirements does computer security depend on?
Computer security depends on functional requirements and assurance requirements. Functional requirements describe what a system should do, while assurance requirements describe how functional requirements should be implemented and tested.
4. How many types of IT security are there?
There are three broad types of IT security: network security, end-point security, and internet security.
5. What are the two objectives of information security?
The main objectives of information security are ensuring confidentiality, integrity, and availability of company information.
6. What are two approaches to information security implementation?
Two popular approaches to implementing information security are the bottom-up and top-down approaches.
7. What are the three basic security requirements?
The three basic security requirements are confidentiality, integrity, and availability. All three requirements support one another and cannot be ignored.
8. What are the three basic requirements of information security?
The three basic requirements of information security are confidentiality, integrity, and availability. These components make up the CIA triad and represent fundamental objectives of information security.
Note: The answers provided are based on my personal experience and understanding.
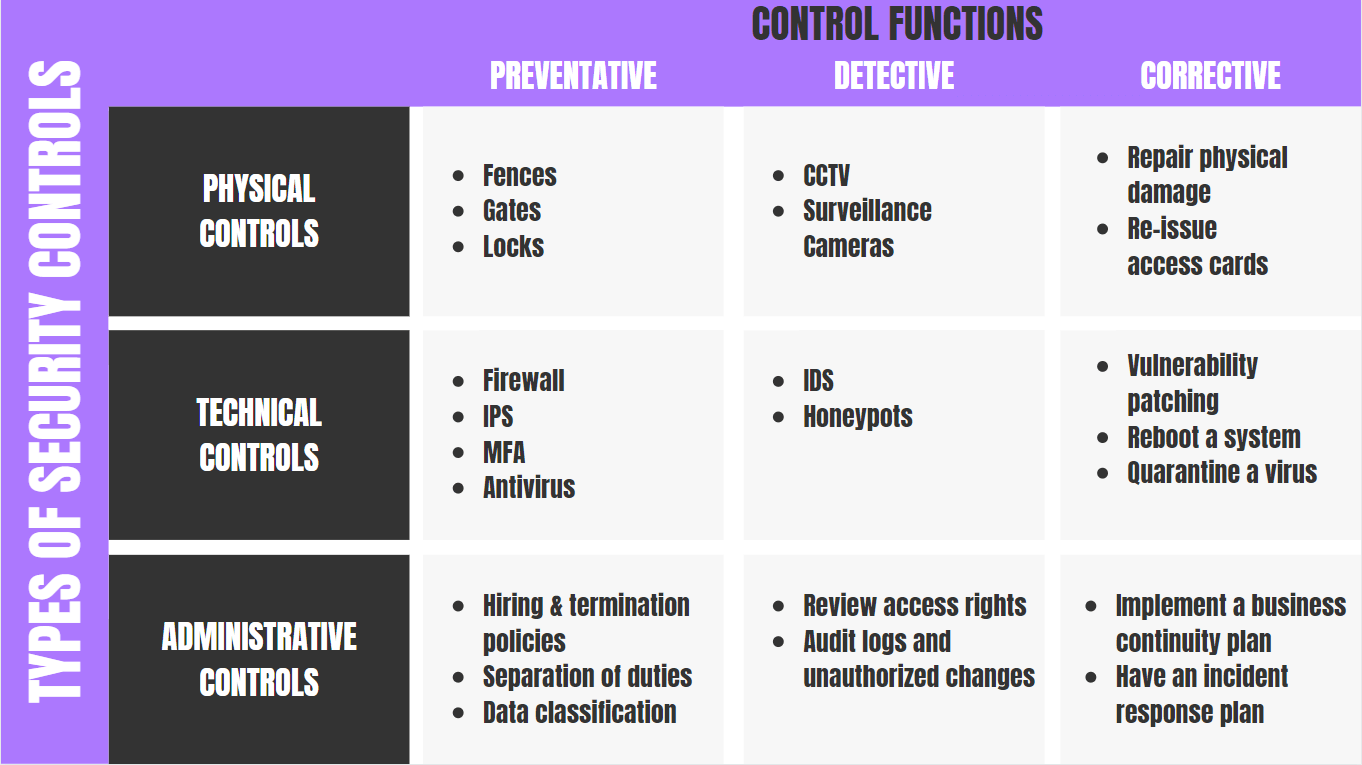
What are the two types of information security
What are the Types of Information SecurityApplication Security. It describes the measures taken to secure the data from unwanted access, misuse, and disruption to applications and systems.Infrastructure Security.Cloud Security.Cryptography.Confidentiality.Integrity.Availability.Develop security policy.
What are types of security requirements
Summarizing, the security requirements must cover areas such as:Authentication and password management.Authorization and role management.Audit logging and analysis.Network and data security.Code integrity and validation testing.Cryptography and key management.Data validation and sanitization.
What two types of requirements does computer security depend on
Principle 5: Computer Security Depends on Two Types of Requirements: Functional and Assurance. Functional requirements describe what a system should do. Assurance requirements describe how functional requirements should be implemented and tested.
Cached
How many types of IT security are there
However, for the most part, there are three broad types of IT security: Network, End-Point, and Internet security (the cybersecurity subcategory).
Cached
What are 2 objectives of information security
The main objectives of InfoSec are typically related to ensuring confidentiality, integrity, and availability of company information.
What are 2 approaches to information security implementation
Two popular approaches to implementing information security are the bottom-up and top-down approaches.
What are the 3 basic security requirements
Regardless of security policy goals, one cannot completely ignore any of the three major requirements—confidentiality, integrity, and availability—which support one another.
What are the 3 basic requirements of information security
The CIA triad refers to an information security model made up of the three main components: confidentiality, integrity and availability. Each component represents a fundamental objective of information security.
What are the two 2 main types of requirements
They fall into two large groups.Functional requirements define what a product must do, what its features and functions are.Nonfunctional requirements describe the general properties of a system. They are also known as quality attributes.
What are computer security requirements
Regardless of security policy goals, one cannot completely ignore any of the three major requirements—confidentiality, integrity, and availability—which support one another. For example, confidentiality is needed to protect passwords.
What are the 3 types of security
What are the Types of Security There are four main types of security: debt securities, equity securities, derivative securities, and hybrid securities, which are a combination of debt and equity.
Which of the following is a type of IT security
Hence, to provide security, it is divided into the following types: Cloud Security: Provides security for the data stored on the cloud. Network Security: Protects the internal network from threats. Application Security: Protects data stored in the application software.
What are the 3 key objectives of IT security
The CIA triad refers to an information security model made up of the three main components: confidentiality, integrity and availability. Each component represents a fundamental objective of information security.
What are the main three 3 objectives of security
Included in this definition are three terms that are generally regarded as the high-level security objectives – integrity, availability, and confidentiality.
What are the 2 main frameworks for cyber security incident response
These are called Incident Response Frameworks, and two of the most commonly used ones are called the NIST and SANS frameworks.
What are the two key types of security policies and procedures
There are 2 types of security policies: technical security and administrative security policies. Technical security policies describe the configuration of the technology for convenient use; body security policies address however all persons should behave. All workers should conform to and sign each the policies.
What are the principles of IT security
What are the 3 Principles of Information Security The basic tenets of information security are confidentiality, integrity and availability. Every element of the information security program must be designed to implement one or more of these principles. Together they are called the CIA Triad.
What are the primary requirements of information security
The fundamental principles (tenets) of information security are confidentiality, integrity, and availability. Every element of an information security program (and every security control put in place by an entity) should be designed to achieve one or more of these principles. Together, they are called the CIA Triad.
What are the data security requirements
Main Elements of Data Security
There are three core elements to data security that all organizations should adhere to: Confidentiality, Integrity, and Availability. These concepts are also referred to as the CIA Triad, functioning as a security model and framework for top-notch data security.
What are the two major types of requirements in software testing
These system requirements may be broadly classified in two types functional requirements and non-functional requirements.
What are 2 ways of gathering user requirements
11 Requirements Gathering Techniques for Agile Product TeamsInterviews.Questionnaires or Surveys.User Observation.Document Analysis.Interface Analysis.Workshops.Brainstorming.Role-Play.
What is the 3 major aspect of security
Confidentiality, integrity and availability together are considered the three most important concepts within information security. Considering these three principles together within the framework of the "triad" can help guide the development of security policies for organizations.
What is the 3 types of computer security
The Different Types of CybersecurityNetwork Security. Most attacks occur over the network, and network security solutions are designed to identify and block these attacks.Cloud Security.Endpoint Security.Mobile Security.IoT Security.Application Security.Zero Trust.
What are the three core principles of IT security
The CIA triad refers to an information security model made up of the three main components: confidentiality, integrity and availability. Each component represents a fundamental objective of information security.
What are the 3 basic components of information security
Three basic security concepts important to information on the internet are confidentiality, integrity, and availability. Concepts relating to the people who use that information are authentication, authorization, and nonrepudiation.