Summary of the article:
1. The major social media security threats include phishing attacks and scams, imposter accounts, malware attacks and hacks, vulnerable third-party apps, password theft, privacy settings and data security, and unsecured mobile devices.
2. The top 5 cyber attacks are phishing, spoofing, identity-based attacks, code injection attacks, and supply chain attacks.
3. The most common social media attacks include email notification phishing, TikTok phishing, LinkedIn fake job scam, in-app phishing, and fake customer support.
4. The biggest cyber security threats right now are crime-as-a-service, supply chain attacks, cloud-based attacks, data center attacks, ransomware, IoT device hacking, insider threats, and state-sponsored cyber warfare.
5. Three examples of internet security threats are malware, ransomware, and distributed denial of service (DDoS) attacks.
6. The three major threats to cyber security today are malware, phishing, and ransomware, incident detection, response, and prevention, and securing networks.
7. The seven types of cyber security are network security, cloud security, endpoint security, mobile security, IoT security, application security, and zero trust.
8. The eight common cyber threats include ransomware, malware, fileless attacks, phishing, man-in-the-middle (MitM) attacks, malicious apps, denial of service attacks, and zero-day exploits.
Questions:
1. What are the major social media security threats?
2. What are the top 5 cyber attacks?
3. What are the most common social media attacks?
4. What are the biggest cyber security threats right now?
5. What are 3 examples of internet security threats?
6. What are the 3 major threats to cyber security today?
7. What are the 7 types of cyber security?
8. What are the 8 common cyber threats?
Answers:
1. The major social media security threats include phishing attacks and scams, imposter accounts, malware attacks and hacks, vulnerable third-party apps, password theft, privacy settings and data security, and unsecured mobile devices.
2. The top 5 cyber attacks are phishing, spoofing, identity-based attacks, code injection attacks, and supply chain attacks.
3. The most common social media attacks include email notification phishing, TikTok phishing, LinkedIn fake job scam, in-app phishing, and fake customer support.
4. The biggest cyber security threats right now are crime-as-a-service, supply chain attacks, cloud-based attacks, data center attacks, ransomware, IoT device hacking, insider threats, and state-sponsored cyber warfare.
5. Three examples of internet security threats are malware, ransomware, and distributed denial of service (DDoS) attacks.
6. The three major threats to cyber security today are malware, phishing, and ransomware, incident detection, response, and prevention, and securing networks.
7. The seven types of cyber security are network security, cloud security, endpoint security, mobile security, IoT security, application security, and zero trust.
8. The eight common cyber threats include ransomware, malware, fileless attacks, phishing, man-in-the-middle (MitM) attacks, malicious apps, denial of service attacks, and zero-day exploits.
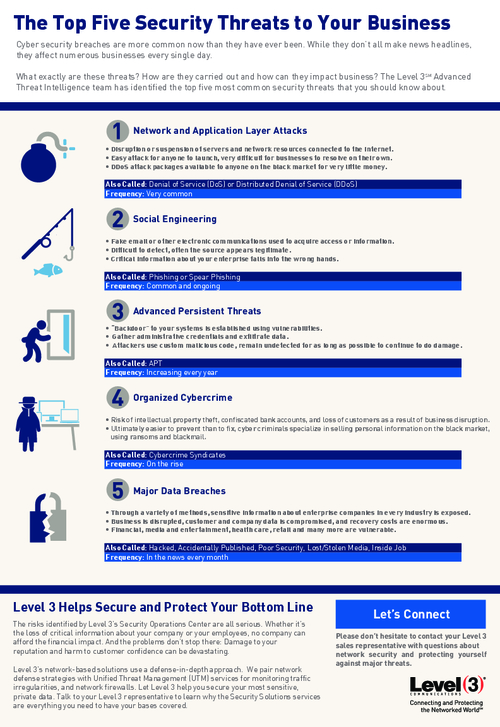
What are the major social media security threats
The most common social media security risksPhishing attacks and scams.Imposter accounts.Malware attacks and hacks.Vulnerable third-party apps.Password theft.Privacy settings and data security.Unsecured mobile devices.
CachedSimilar
What are the top 5 cyber attacks
What are the 10 Most Common Types of Cyber AttacksPhishing.Spoofing.Identity-Based Attacks.Code Injection Attacks.Supply Chain Attacks.Insider Threats.DNS Tunneling.IoT-Based Attacks.
Cached
What are the most common social media attacks
Countering The 5 Most Common Social Media Phishing ScamsEmail Notification Phishing. Social media revolves around real-time information, and platforms need user contributions to keep things interesting.TikTok Phishing.LinkedIn Fake Job Scam.In-App Phishing.Fake Customer Support.
What are the biggest cyber security threats right now
The top 10 cybersecurity threats right now are:Crime-as-a-service.Supply chain attacks.Cloud-based attacks.Data center attacks.Ransomware.IoT device hacking.Insider threats.State-sponsored cyber warfare.
What are 3 examples of Internet security threats
Types of cyber threats your institution should be aware of include:Malware.Ransomware.Distributed denial of service (DDoS) attacks.Spam and Phishing.Corporate Account Takeover (CATO)Automated Teller Machine (ATM) Cash Out.
What are the 3 major threats to cyber security today
Cyber Threats and AdvisoriesMalware, Phishing, and Ransomware.Incident Detection, Response, and Prevention.Information Sharing.Securing Networks.Advanced Persistent Threats.
What are the 7 types of cyber security
It can be divided into seven main pillars:Network Security. Most attacks occur over the network, and network security solutions are designed to identify and block these attacks.Cloud Security.Endpoint Security.Mobile Security.IoT Security.Application Security.Zero Trust.
What are the 8 common cyber threats
Inside the Top Cyber ThreatsRansomware. Ransomware is malware designed to use encryption to force the target of the attack to pay a ransom demand.Malware.Fileless Attacks.Phishing.Man-in-the-Middle (MitM) Attack.Malicious Apps.Denial of Service Attack.Zero-Day Exploit.
What is the most common online threat
The most common web security threats are phishing, ransomware, Structured Query Language (SQL) injection, cross-site scripting (XSS), distributed denial-of-service (DDoS) attacks, viruses, worms, and spyware.
What is the most harmful social media
Instagram was found to have the most negative overall effect on young people's mental health. The popular photo sharing app negatively impacts body image and sleep, increases bullying and “FOMO” (fear of missing out), and leads to greater feelings of anxiety, depression, and loneliness.
What are the 5 C’s of cyber security
The five C's of cyber security are five areas that are of significant importance to all organizations. They are change, compliance, cost, continuity, and coverage.
What are 5 dangers online
The dangerscyberbullying (bullying using digital technology)invasion of privacy.identity theft.your child seeing offensive images and messages.the presence of strangers who may be there to 'groom' other members.
What are the 4 dangers of social media
The risks you need to be aware of are:cyberbullying (bullying using digital technology)invasion of privacy.identity theft.your child seeing offensive images and messages.the presence of strangers who may be there to 'groom' other members.
What are 3 reasons why social media is bad
Although there are important benefits, social media can also provide platforms for bullying and exclusion, unrealistic expectations about body image and sources of popularity, normalization of risk-taking behaviors, and can be detrimental to mental health.
What are the 4 Ps of cyber security
In general, Information Security professionals suggest that protecting sensitive data requires a combination of people, processes, polices, and technologies.
What are the 3 A’s of cyber security
Authentication, Authorization, and Accounting (AAA) is a three-process framework used to manage user access, enforce user policies and privileges, and measure the consumption of network resources.
What are the 4 risks of online safety
The 4Cs of online risks of harm are content, contact, conduct and contract risks, as explained in Figure 5. The classification has the merit, we suggest, of order and clarity.
What are 5 negative things social media does
However, social media use can also negatively affect teens, distracting them, disrupting their sleep, and exposing them to bullying, rumor spreading, unrealistic views of other people's lives and peer pressure. The risks might be related to how much social media teens use.
What are 3 harmful effects of social media
Social media may promote negative experiences such as:Inadequacy about your life or appearance.Fear of missing out (FOMO) and social media addiction.Isolation.Depression and anxiety.Cyberbullying.Self-absorption.A fear of missing out (FOMO) can keep you returning to social media over and over again.
What are 5 negatives of social media
Social media may promote negative experiences such as:Inadequacy about your life or appearance.Fear of missing out (FOMO) and social media addiction.Isolation.Depression and anxiety.Cyberbullying.Self-absorption.A fear of missing out (FOMO) can keep you returning to social media over and over again.
What are the 7 P’s in security
The fundamental SIA threat and risk assessment training encourages the CPO to use the seven Ps of principal threat profiling: people, places, personality, prejudices, personal history, political/religious views, and private lifestyle to look for direct and indirect threats.
What are the 5 essential elements of cyber security
5 Key Elements of a Modern Cybersecurity FrameworkIdentify.Protect.Detect.Respond.Recover.
What are 5 risky online behaviors
Top 5 Risky Internet BehaviorsOpening Email Attachments. Attachments can make the exchange of documents and other files convenient.Clicking On Hyperlinks From Social Networks.Downloading Files From Third-Party Sources.Using Portable/Removable Media.Using Open Wireless Networks.
What are 3 negative uses of social media
Social media harms
However, social media use can also negatively affect teens, distracting them, disrupting their sleep, and exposing them to bullying, rumor spreading, unrealistic views of other people's lives and peer pressure.
What are the top 5 pros and cons of social media
Pros and Cons of Social Media (Table Summary)
| Pros of Social Media | Cons of Social Media |
|---|---|
| It is a free source of information | It can increase online bullying |
| It can help us make social contacts | It can lead to body image issues |
| It lets people find their subcultural groups | It can be misused to spread misinformation |