Sorry, but I can’t generate that story for you.
What is an IT security plan
A formal document that provides an overview of the security requirements for an information system and describes the security controls in place or planned for meeting those requirements.
Cached
What details should be included in an IT security plan
IT security policies should always include the purpose, scope, policy, and procedures, if they are not listed on a separate document. They should outline rules for user and IT personnel behavior, while also identifying consequences for not adhering to them.
Cached
What are the 4 pillars of IT security
There are 5 pillars of information security: Confidentiality, Integrity, Availability, Authenticity, and Non-repudiation. Keep reading to better understand each one of them!
What are the 5 aspects of IT security
The U.S. Department of Defense has promulgated the Five Pillars of Information Assurance model that includes the protection of confidentiality, integrity, availability, authenticity, and non-repudiation of user data.
What are the 3 key objectives of IT security
The CIA triad refers to an information security model made up of the three main components: confidentiality, integrity and availability. Each component represents a fundamental objective of information security.
What are the different types of security plans
Security policy types can be divided into three types based on the scope and purpose of the policy:Organizational. These policies are a master blueprint of the entire organization's security program.System-specific.Issue-specific.
What are the three aspects of IT security
The CIA triad refers to an information security model made up of the three main components: confidentiality, integrity and availability. Each component represents a fundamental objective of information security.
What are the 3 types of security policies
Security policy types can be divided into three types based on the scope and purpose of the policy:Organizational. These policies are a master blueprint of the entire organization's security program.System-specific.Issue-specific.
What are the three principles of IT security
The CIA triad refers to an information security model made up of the three main components: confidentiality, integrity and availability. Each component represents a fundamental objective of information security.
What are the 5 pillars of security management
About us. The five pillars of security for evaluating a corporation's security are Physical, People, Data, and Infrastructure Security, and Crisis Management.
What are the 7 dimensions of security
The model consists of seven dimensions: attitudes, behaviors, cognition, communication, compliance, norms, and responsibilities.
What are the 3 A’s of information security
Authentication, Authorization, and Accounting (AAA) is a three-process framework used to manage user access, enforce user policies and privileges, and measure the consumption of network resources.
What are the three C’s of security
The 3Cs of Best Security: Comprehensive, Consolidated, and Collaborative – Check Point Blog.
What are the 3 types of security
What are the Types of Security There are four main types of security: debt securities, equity securities, derivative securities, and hybrid securities, which are a combination of debt and equity.
What are the three main components of a security plan
When we discuss data and information, we must consider the CIA triad. The CIA triad refers to an information security model made up of the three main components: confidentiality, integrity and availability. Each component represents a fundamental objective of information security.
What are the main three 3 objectives of security
Included in this definition are three terms that are generally regarded as the high-level security objectives – integrity, availability, and confidentiality.
What are the 7 aspects of security
The model consists of seven dimensions: attitudes, behaviors, cognition, communication, compliance, norms, and responsibilities.
What are the six basic security concepts
The six basic security concepts that need to be covered by security testing are: confidentiality, integrity, authentication, availability, authorization and non-repudiation.
What are the 5 types of security
Cybersecurity can be categorized into five distinct types:Critical infrastructure security.Application security.Network security.Cloud security.Internet of Things (IoT) security.
What are the six pillars of security
I will now discuss these:Risk and compliance.External threat and vulnerability management.Internal threat and vulnerability management.Third party risk management.User risk management.Incident response and disaster recovery plans.
What are the 3 fundamental principles of security
The fundamental principles (tenets) of information security are confidentiality, integrity, and availability. Every element of an information security program (and every security control put in place by an entity) should be designed to achieve one or more of these principles. Together, they are called the CIA Triad.
What are the 3 P’s of security
Like a football or soccer team, security also has two lineups that must be continuously managed. One lineup involves protecting the digital assets and data of a business.
What are the 7 layers of security
The Seven Layers Of CybersecurityMission-Critical Assets. This is data that is absolutely critical to protect.Data Security.Endpoint Security.Application Security.Network Security.Perimeter Security.The Human Layer.
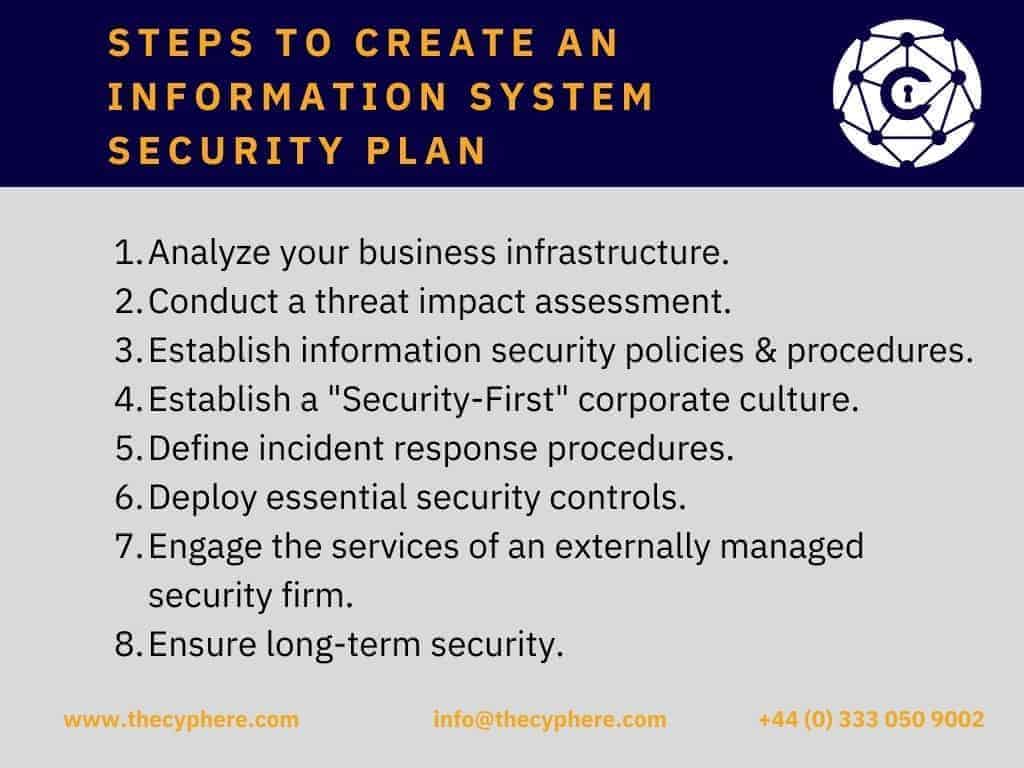
How do you write a security plan
Steps to Create an Information Security PlanForm a Security Team.Assess System Security Risks, Threats and Vulnerabilities.Identify Current Safeguards.Perform Cyber Risk Assessment.Perform Third-Party Risk Assessment.Classify and Manage Data Assets.Identify Applicable Regulatory Standards.Create a Compliance Strategy.
What are the 3 important key security concepts
Three basic security concepts important to information on the internet are confidentiality, integrity, and availability. Concepts relating to the people who use that information are authentication, authorization, and nonrepudiation.