Summary of the Article
The article discusses various components and aspects of information security. Here are the key points covered in 10 paragraphs:
1. The U.S. Department of Defense has identified the five pillars of information assurance: confidentiality, integrity, availability, authenticity, and non-repudiation of user data.
2. A good security plan includes several key components: risk assessment, security policies and procedures, training and awareness, physical security measures, emergency response plan, and regular testing and review.
3. The CIA triad, consisting of confidentiality, integrity, and availability, represents the three main components of information security.
4. An information technology security plan is a formal document that outlines the security requirements for an information system and describes the security controls in place or planned for meeting those requirements.
5. The four main security technology components are deterrence (convincing unwanted persons that unauthorized access is unlikely), detection, delay, and response.
6. The four qualities of information security, according to a proposed standard, include access control, availability, data quality, compliance, and technical aspects.
7. The security planning process consists of five steps: identification of assets, exposure of loss events, assignment of occurrence probability factors, assessment of the impact of occurrence, and determination of appropriate safeguards.
8. The three components of an information system are technology, people, and processes. These components work together to support the organization’s information needs and goals.
9. Continuous monitoring and evaluation are essential for maintaining effective information security. Regular assessments of risks and vulnerabilities help identify areas for improvement and ensure that security measures remain up to date.
10. Collaboration and communication between all stakeholders, including employees, management, and external partners, are crucial for successful information security implementation and management.
Questions and Answers
1. What are the 5 components of information security?
The five components of information security are confidentiality, integrity, availability, authenticity, and non-repudiation of user data.
2. What are the main components of a security plan?
The main components of a security plan include risk assessment, security policies and procedures, training and awareness, physical security measures, emergency response plan, and regular testing and review.
3. What are the 3 components of good information security?
The three main components of good information security are confidentiality, integrity, and availability, also known as the CIA triad.
4. What is an information technology security plan?
An information technology security plan is a formal document that provides an overview of the security requirements for an information system and describes the security controls in place or planned for meeting those requirements.
5. What are the four main security technology components?
The four main security technology components are deterrence, detection, delay, and response.
6. What are the four qualities of information security?
According to a proposed standard, the four qualities of information security are access control, availability, data quality, compliance, and technical aspects.
7. What are the five steps in the security planning process?
The five steps in the security planning process are identification of assets, exposure of loss events, assignment of occurrence probability factors, assessment of the impact of occurrence, and determination of appropriate safeguards.
8. What are the three components of an information system?
The three components of an information system are technology, people, and processes.
9. What is the importance of continuous monitoring and evaluation in information security?
Continuous monitoring and evaluation are essential for maintaining effective information security. Regular assessments of risks and vulnerabilities help identify areas for improvement and ensure that security measures remain up to date.
10. What is the role of collaboration and communication in information security?
Collaboration and communication between all stakeholders, including employees, management, and external partners, are crucial for successful information security implementation and management.
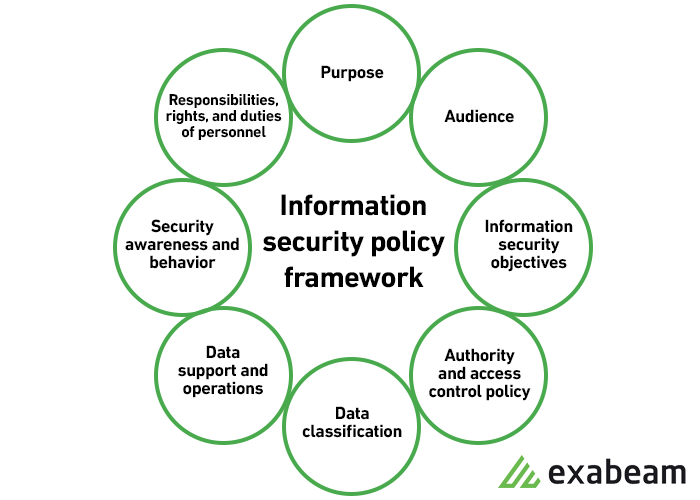
What are the 5 components of information security
The U.S. Department of Defense has promulgated the Five Pillars of Information Assurance model that includes the protection of confidentiality, integrity, availability, authenticity, and non-repudiation of user data.
What are the main components of a security plan
Here are the key components of a good security plan:Risk Assessment. The first step in developing a security plan is to conduct a risk assessment.Security Policies and Procedures.Training and Awareness.Physical Security Measures.Emergency Response Plan.Regular Testing and Review.
Cached
What are the 3 components of good information security
When we discuss data and information, we must consider the CIA triad. The CIA triad refers to an information security model made up of the three main components: confidentiality, integrity and availability. Each component represents a fundamental objective of information security.
What is the information technology security plan
Definition(s): A formal document that provides an overview of the security requirements for an information system and describes the security controls in place or planned for meeting those requirements.
Cached
What are the four 4 main security technology components
The four components are:Deterrence. The initial layer of security; the goal of deterrence is to convince unwanted persons that a successful effort to enter an unauthorized area is unlikely.Detection.Delay.Response.
What are the 4 qualities of information security
This standard proposed an operational definition of the key concepts of security, with elements called "security objectives", related to access control (9), availability (3), data quality (1), compliance, and technical (4).
What are the five steps in the security planning process
The security planning process consists of the following five steps:Assets are identified.Loss events are exposed.Occurrence probability factors are assigned.Impact of occurrence is assessed.
What are the three 3 components of an information system
Information systems are defined by the components that make up the system, and the role those components play in an organization. Information systems can be viewed as having three core components: technology, people, and process that take the data and transform it into information.
What is the purpose of IT security plan
Compliance Requirements
These laws and policies are generally designed to protect individuals and organizations against the unauthorized disclosure of information that could compromise their identity or privacy.
How do I create an information security plan
Steps to Create an Information Security PlanForm a Security Team.Assess System Security Risks, Threats and Vulnerabilities.Identify Current Safeguards.Perform Cyber Risk Assessment.Perform Third-Party Risk Assessment.Classify and Manage Data Assets.Identify Applicable Regulatory Standards.Create a Compliance Strategy.
What are the four pillars of a strong IT security strategy
Practice.Practice.In addition to employee security training, organizations can also measure their current position and improve their security controls by simulating attacks, leveraging Red and Blue team exercises.Anticipate.Detect.Respond.
What are the 4 types of information security
There are four types of information technology security you should consider or improve upon:Network Security.Cloud Security.Application Security.Internet of Things Security.
What are the 7 P’s of information security
We outline the anatomy of the AMBI-CYBER architecture adopting a balanced scorecard, multistage approach under a 7Ps stage gate model (Patient, Persistent, Persevering, Proactive, Predictive, Preventive, and Preemptive).
What are the 6 P’s of information security
InfoSec management oversees a specialized program, certain aspects of its managerial responsibility are unique. These unique functions are known as "the six Ps" (planning, policy, programs, protection, people, and project management).
What are the 7 elements of security model
The 7 Elements of Human Security are defined by the United Nations as: Economic, Environmental, Food, Health, Political, Personal and Community. We design projects and initiatives with our partners that holistically address these areas of Human Security.
What are the 4 P’s in security
In general, Information Security professionals suggest that protecting sensitive data requires a combination of people, processes, polices, and technologies.
What are the four 4 components of an information system
The main components of information systems are computer hardware and software, telecommunications, databases and data warehouses, human resources, and procedures.
What are the components of an information system plan
An information system is essentially made up of five components hardware, software, database, network and people. These five components integrate to perform input, process, output, feedback and control.
What are the four major purposes of information security
Information security protects sensitive information from unauthorized activities, including inspection, modification, recording, and any disruption or destruction.
What are the 4 objectives of planning for security
What Are The Four Objectives of Planning For Security.How We Can Identify and Protect a NetworkHow We Can Access Control a NetworkHow We Can Protect a NetworkHow We Can Monitor a Network
What are the 4 objectives in planning of information security
This FIPS standard covers the security objectives of confidentiality, integrity, availability, and nonrepudiation.
What are the 4 elements of data security plan
An effective security system comprises of four elements: Protection, Detection, Verification & Reaction. These are the essential principles for effective security on any site, whether it's a small independent business with a single site, or a large multinational corporation with hundreds of locations.
What are the five 5 key points to be considered before implementing security strategy
There are five key steps to implementing risk-based security and, though time-consuming, they will align security with the goals of the organization.Step 1: Asset valuation.Step 2: Identify threats.Step 3: Identify vulnerabilities.Step 4: Risk profiling.Step 5: Risk treatment.
What are the 4 fundamentals of security
There are four main principles of information security: confidentiality, integrity, availability, and non-repudiation.
What are the six components of information security
Hence, information systems can be viewed as having six major components: hardware, software, network communications, data, people, and processes. Each has a specific role, and all roles must work together to have a working information system.