Summary:
1. Beeping things in stores – Security Tags
These are useless without a detection system. The two most commonly used retail security programs are Sensormatic and Checkpoint.
2. Alarms on clothes – Clothing Security Tags
A clothing security tag is a small “signal transmitter” that is placed on merchandise to protect it. It signals to the EAS antennas and triggers an alarm if someone gets too close.
3. Detectors at stores – Detection Antennas
These antennas send out signals and receive responses from security tags or labels attached to products. When an item with an active tag passes by, an alarm sounds.
4. Triggers of sensors at stores – Magnetic Fields
Sensors on the doorway transmit and receive a weak magnetic field. When an active anti-theft tag enters this zone, the sensor reads the changes in the magnetic waves and triggers an alarm.
5. Beep codes – POST Codes
Beep codes are also known as POST codes. They are short tests performed by the motherboard BIOS or UEFI when a computer powers on.
6. Detectors at the front of stores – Metal Detectors or Foil Detectors
These detectors are designed to detect special foil bags used by shoplifters. They can be separate antennas or integrated into anti-theft systems at the entrance of a store.
7. Removing anti-shoplifting devices – Plastic Grocery Bag Method
One method to remove anti-shoplifting devices involves using a plastic grocery bag. By looping the bag through the space between the tag and the clothing and pulling it snug, the device can be removed.
8. Consequences of cutting a security tag
If a security tag is cut off and taken out of a store, the person may face charges for removal of the device and theft. The charges range from a simple misdemeanor to a class “C” felony.
Questions:
1. What are the beeping things in stores called?
Security Tags.
2. What are the alarms on clothes called?
Clothing Security Tags.
3. What are the detectors at stores?
Detection Antennas.
4. What triggers the sensors at stores?
Magnetic Fields.
5. What are beep codes called?
POST Codes.
6. What are the detectors at the front of stores called?
Metal Detectors or Foil Detectors.
7. How do I remove anti-shoplifting devices?
Using the Plastic Grocery Bag Method.
8. What happens if you cut a security tag?
Possible charges for removal of the device and theft.
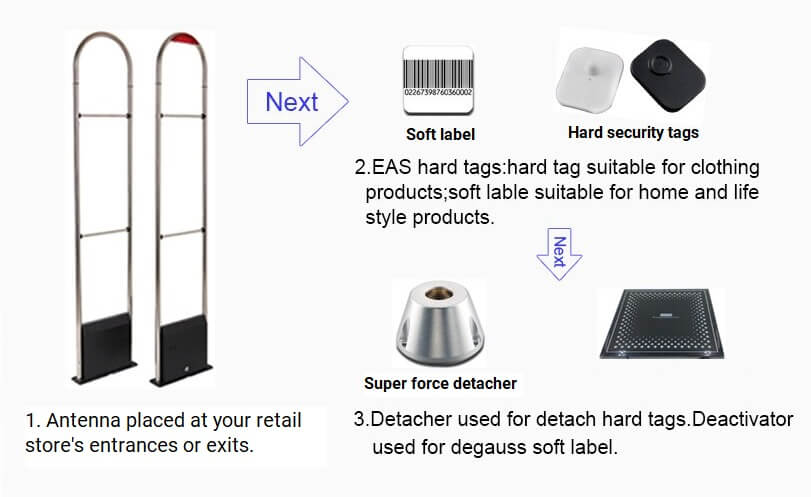
What are the beeping things in stores called
Without a detection system, security tags are useless.
The detection system usually is connected to software that controls the sensitivity, volume and duration of the alarm. Sensormatic and Checkpoint are the two most commonly used retail security programs.
Cached
What are the alarms on clothes called
A clothing security tag is one crucial part of an EAS system. The tag is a small “signal transmitter” that you put on the merchandise that you want to protect. The tag will signal to the EAS antennas to make them alarm if they come to close.
What are the detectors at stores
These detection antennas send out a signal, and security tags or labels attached to products and merchandise within a store answer back. When an item with an active tag or label passes by or between these antennas, an alarm sounds, indicating an item is leaving the store.
Cached
What triggers the sensors at stores
In stores, there are sensors on the doorway that transmit and receive a weak magnetic field. When an active anti-theft tag (meaning it hasn't been demagnetized) enters this zone, oscillation will occur, and the sensor will read the changes in the magnetic waves, causing an alarm to go off.
Cached
What are beep codes called
It may also be called the POST code. When a computer powers on, the motherboard BIOS or UEFI performs a short test called POST.
What are the detectors at the front of stores
Metal detectors are designed to detect special foil bags that are used by attackers for shoplifting. Such metal detectors are also called foil detectors or foil bags. They can be made as separate antennas installed at the entrance to the store or integrated into anti-theft systems.
How do I remove anti shoplifting devices
So here's pants. And pretty much everybody has a plastic grocery bag lying around somewhere. Take the bag circle it through the space between the tag and the clothing pulling it snug so that way it
What happens if you cut a security tag
If you take the security tag off the jacket and leave the store with it, on top of being charged with removal of the device, you could also be prosecuted for theft. The charges for this offense range from a simple misdemeanor to a class “C” felony. Again, the level depends on the value of the stolen item.
What is a shoplifting sensor called
Electronic article surveillance (EAS) is a type of system used to prevent shoplifting from retail stores, pilferage of books from libraries, or unwanted removal of properties from office buildings. EAS systems typically consist of two components: EAS antennas and EAS tags or labels.
How do you shoplift without the alarm going off
Yes, aluminum foil will block security tags. Therefore, it is often used to block sensors from catching signals sent by anti-theft devices. The primary reason is that several layers of aluminum foil can block radio signals. It gets creative with special bags lined with aluminum foil to avoid detection at the cashier.
What is a 3 beep alarm
3 Beeps and a Pause: EMERGENCY. This type of chirp means that smoke has been detected in your home. You and your family need to evacuate and call 9-1-1 once safely outside.
What is the code for 3 beeps
You can check the manufacturer's guide on beep error codes. Usually, a 3-beep error indicates a system memory error. If it is, please check your ram module if it is seated properly.
What sets off shoplifting alarms
By attaching security tags to your products, retailers can trigger off an alarm if a shoplifter walks out with a product with the tag still on through the electronic sensors at the exit gates. There are many types of EAS devices you can use like tags, labels, antennas, spider tags and more.
What triggers shoplifting alarms
What triggers the alarm is the magnet. However, magnets are usually placed near the barcode so the cashier knows and can deactivate the magnet simply by scanning the item. That makes many people mistakenly think that unscanned barcodes set off alarms.
Does RFID stop shoplifting
These tags have traditionally been used by retailers to track products along the supply chain and to alert store associates when an item might be low and need restocking. But with the RFID tagging becoming more common, retailers have started to use the tags to combat theft.
How do shoplifters remove security tags
In retail stores, cashiers can use a magnetic removal tool to turn off the security tag, and then anti-theft strips are demagnetized.
What is the hardest security tag to remove
In terms of security, shell tags are the shape considered hardest to prise open and remove illegally.
What are anti-theft devices called
Security pedestals, otherwise known as antennas or security gates, are set up at the store entry / exit as a theft deterrent. They will alert you if any active tag or label has passed through them indicating a product may have been stolen.
What are 3 examples of security devices used to prevent shoplifting
In addition to giving you advice on the solutions currently available to outsmart thieves (alarms, security gates and guards, surveillance cameras etc.), we propose a brand new system to help you considerably reduce shrinkage !
What does 4 beeps alarm mean
Carbon monoxide alarms
Here's a simple guide: Smoke alarms alert you with three beeps in a row. Carbon monoxide alarms alert you with four beeps.
What is a 1 3 2 beep code
Now only "no memory failure" conditions generate the beep code, the beep pattern is 1-3-2 (1 beep, then 3 beeps, then 2 beeps). This beep code tells you that the computer encountered a memory problem. Note: The new beep codes emit only memory failure symptoms.
What alarm beeps 3 times in a row
3 Beeps, 2 second pause, repeat Off Off Condition: Non-originating Smoke Alarm. Recommendation: Another interconnected smoke alarm has sensed smoke, causing all interconnected units to sound. If hazard is identified, take all precautions if an alarm sounds by calling an Emergency Service and getting out of the home.
What is the beeping code called
It may also be called the POST code. When a computer powers on, the motherboard BIOS or UEFI performs a short test called POST.
What are 3 common shoplifting techniques
Techniques of shoplifting include (1) hiding merchandise in loose clothing, (2) palming expensive objects and substituting for them, (3) using box devices that can be placed over items that are trapped by a spring device, or (4) using a 'booster' belt with a series of hooks on which stolen objects are placed.
How serious is RFID theft
How secure are RFID credit cards RFID credit cards are considered to be as safe as EMV chip cards, and data theft concerning RFID cards is uncommon. This is because of how these cards transmit information and what information is shared.