html format without tags html, head, body, title – only formatting for text. 1 – summary of the article in h2 with key points in 10 paragraphs each paragraph for 3000 characters is MANDATORY in html format with line breaks br and formatting key points in strong, then 15 unique questions based on text in strong tags and detailed answers rewrite or unique from text, not copypast, each answer for 3000 characters is MANDATORY as much information as possible in html with line breaks and BR and lists. Tone of voice – personal experience from my point of view like I use it, no repetition, without introduction and conclusion
Summary of the Article: Data Protection Principles
1. Lawfulness, fairness, and transparency: These principles are found at the outset of the GDPR and inform all other provisions of the legislation.
2. Purpose limitation: Data should only be collected for a specified purpose and should not be further processed in a manner that is incompatible with that purpose.
3. Data minimisation: Only collect and retain the data that is necessary for the intended purpose.
4. Accuracy: Data should be accurate, and if necessary, kept up to date.
5. Storage limitation: Data should not be kept for longer than is necessary.
6. Integrity and confidentiality: Data should be secured and protected against unauthorized access, loss, or damage.
7. Accountability: Organizations must be able to demonstrate compliance and take responsibility for their data processing activities.
Questions and Answers:
1. What is the 6th principle of the Data Protection Act?
The 6th principle of the Data Protection Act is accountability, which requires organizations to take responsibility for their data processing activities and demonstrate compliance with data protection regulations.
2. What are the six essential data protection methods?
The six essential data protection methods are:
- Lawfulness, fairness, and transparency
- Purpose limitation
- Data minimisation
- Accuracy
- Storage limitation
- Integrity and confidentiality
3. What are the seven principles of data protection?
The seven principles of data protection are:
- Lawfulness, fairness, and transparency
- Purpose limitation
- Data minimisation
- Accuracy
- Storage limitation
- Integrity and confidentiality
- Accountability
4. What are four of the six data protection principles?
Four of the six data protection principles are: lawfulness, fairness and transparency; purpose limitation; data minimisation; and accuracy.
5. What are the eight main principles of data protection?
The eight main principles of data protection are:
- Fair and Lawful Use, Transparency
- Specific for Intended Purpose
- Minimum Data Requirement
- Need for Accuracy
- Data Retention Time Limit
- The right to be forgotten
- Ensuring Data Security
- Accountability
…
15. What are the 5 pillars of data protection?
The five pillars of data protection are: integrity of data in its original form, availability for authorized parties, identity authenticity, data confidentiality, and non-repudiation.
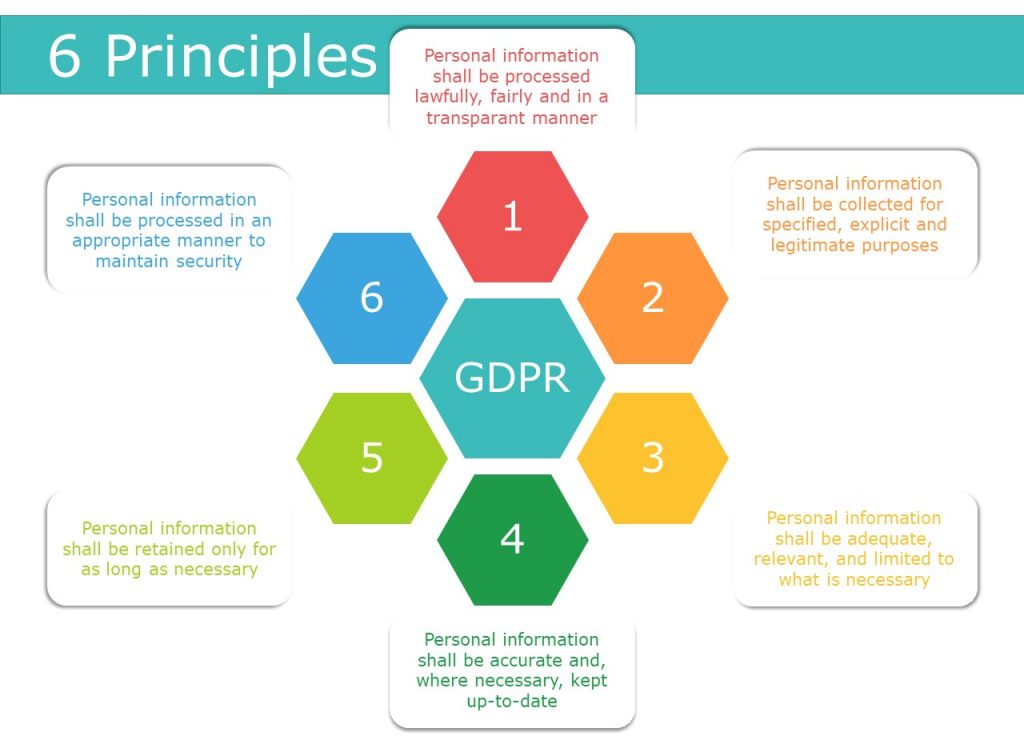
What is the 6 principle of the Data Protection Act
Lawfulness, fairness, and transparency; ▪ Purpose limitation; ▪ Data minimisation; ▪ Accuracy; ▪ Storage limitation; ▪ Integrity and confidentiality; and ▪ Accountability. These principles are found right at the outset of the GDPR, and inform and permeate all other provisions of that legislation.
What are the six 6 essential data protection methods
We take a look at each principle in this blog, and provide advice on how they should fit within your GDPR compliance practices.Lawfulness, fairness and transparency.Purpose limitation.Data minimisation.Accuracy.Storage limitation.Integrity and confidentiality.
What are the 7 principles of data protection
The principles are: Lawfulness, Fairness, and Transparency; Purpose Limitation; Data Minimisation; Accuracy; Storage Limitations; Integrity and Confidentiality; and Accountability.
Cached
What are four of the six data protection principles
Lawfulness, fairness and transparency. Purpose limitation. Data minimisation. Accuracy.
What are the 8 main principles of data protection
What Are the Eight Principles of the Data Protection ActFair and Lawful Use, Transparency. The principle of this first clause is simple.Specific for Intended Purpose.Minimum Data Requirement.Need for Accuracy.Data Retention Time Limit.The right to be forgotten.Ensuring Data Security.Accountability.
How many data protection principles are there
The Seven Principles
At the heart of both the GDPR and the DPA are principles that are designed to act as the foundations upon which data protection legislation is built, informing the ways in which all organisations should adhere to data protection and compliance issues.
What are the 6 Ds of cyber security
In this article, we will discuss the 6 D's of cyber security and how you can implement them in your own cyber-defense strategy — Deter, Detect, Defend, Deflect, Document, and Delay. Creating a holistic approach to your cyber-security plan using these six references can drastically reduce your organization's risk.
What are the 5 pillars of data protection
The five pillars are integrity of data in its original form, availability for authorized parties, identity authenticity, data confidentiality and non-repudiation.
What are the 8 data protection principles
What are the Eight Principles of the Data Protection Act
| 1998 Act | GDPR |
|---|---|
| Principle 1 – fair and lawful | Principle (a) – lawfulness, fairness and transparency |
| Principle 2 – purposes | Principle (b) – purpose limitation |
| Principle 3 – adequacy | Principle (c) – data minimisation |
| Principle 4 – accuracy | Principle (d) – accuracy |
Why is the 8 principles for Data Protection Act important
As a business service provider, we also deal with personal data given by customers. The 8 Principles of Data Protection Act 1998 make sure our personal information is safe. It is a vital step for businesses to secure their customer's personal data by following the laws.
What are the 5 C’s of cyber security
The five C's of cyber security are five areas that are of significant importance to all organizations. They are change, compliance, cost, continuity, and coverage.
What are the six 6 types of attacks on network security
Six Types Of Cyber Threats To Protect AgainstMalware. Malware is an umbrella term for many forms of harmful software — including ransomware and viruses — that sabotage the operation of computers.Phishing.SQL Injection Attack.Cross-Site Scripting (XSS) Attack.Denial of Service (DoS) Attack.Negative Commentary Attacks.
What are the 4 levels of data protection
Data Classification Levels
These can be adopted by commercial organizations, but, most often, we find four levels, Restricted, Confidential, Internal, Public.
What are the eight data protection rights
Explanation of rights to rectification, erasure, restriction of processing, and portability. Explanation of right to withdraw consent. Explanation of right to complain to the relevant supervisory authority. If data collection is a contractual requirement and any consequences.
What are the 3 A’s of cyber security
Authentication, Authorization, and Accounting (AAA) is a three-process framework used to manage user access, enforce user policies and privileges, and measure the consumption of network resources.
What are the 5 types of network security
Types of Network Security ProtectionsFirewall. Firewalls control incoming and outgoing traffic on networks, with predetermined security rules.Network Segmentation.Remote Access VPN.Email Security.Data Loss Prevention (DLP)Intrusion Prevention Systems (IPS)Sandboxing.Hyperscale Network Security.
What are the three A’s of security and data protection
The CIA triad refers to an information security model made up of the three main components: confidentiality, integrity and availability.
How many data protection rules are there
The GDPR sets out seven principles for the lawful processing of personal data. Processing includes the collection, organisation, structuring, storage, alteration, consultation, use, communication, combination, restriction, erasure or destruction of personal data.
Why is the 8 principles for data protection Act important
As a business service provider, we also deal with personal data given by customers. The 8 Principles of Data Protection Act 1998 make sure our personal information is safe. It is a vital step for businesses to secure their customer's personal data by following the laws.
What are the three C’s of security
The 3Cs of Best Security: Comprehensive, Consolidated, and Collaborative – Check Point Blog.
What are the names of the 5 key security principles
The U.S. Department of Defense has promulgated the Five Pillars of Information Assurance model that includes the protection of confidentiality, integrity, availability, authenticity, and non-repudiation of user data.
What are the 3 most important pillars of information security
The CIA triad refers to an information security model made up of the three main components: confidentiality, integrity and availability.
What is the golden rule of data protection
HONESTY – Companies must be honest about the data collected, used, bought, or sold. TRANSPARENCY – Companies need to stop burying data collection policies deep within lengthy legal documents and instead be straightforward with all consumers (regardless of their level of tech-savviness) regarding data privacy practices.
What is the 3 major division of security
There are three primary areas or classifications of security controls. These include management security, operational security, and physical security controls.
What are the three states of data
The three states of data are data at rest, data in motion and data in use. Data can change states quickly and frequently, or it may remain in a single state for the entire life cycle of a computer.