ks:
1. Phishing Attacks: This is when a hacker poses as a trustworthy party and sends you a fraudulent email or message, hoping you will reveal your personal information voluntarily.
2. Brute Force Attacks: In this type of attack, the hacker tries to guess a password by iterating through all possible combinations of allowable characters.
3. Dictionary Attacks: This involves using a pre-generated list of commonly used passwords and trying them against user accounts.
4. Credential Stuffing: Hackers use leaked login credentials from one website and try them on multiple other websites in order to gain unauthorized access.
5. Man-in-the-Middle Attacks: In this type of attack, the hacker intercepts communication between the user and the website, allowing them to access sensitive information like passwords.
6. Keyloggers: This attack involves using malicious software to record a user’s keystrokes and capture their passwords.
7. SQL Injection Attacks: Hackers inject malicious SQL code into a website’s database query, allowing them to gain unauthorized access to the website and its user data.
8. Cross-Site Scripting (XSS): This attack involves injecting malicious scripts into a trusted website, which then gets executed by the user’s browser, allowing the hacker to steal their information.
9. Denial-of-Service (DoS) Attacks: These attacks overwhelm a website or network with excessive traffic, making it inaccessible to legitimate users.
10. Malware: This refers to various forms of harmful software, such as viruses and ransomware, that can be used to steal passwords and other sensitive information.
1. What are the active online attacks for passwords?
Techniques employed by attackers for active online attacks include password guessing, dictionary and brute-forcing attacks, hash injection, phishing, poisoning, and the use of Trojan spyware keyloggers, among others.
2. What is an example of a password attack?
Examples of password attacks include brute-force attacks, credential stuffing, and password spraying.
3. What are the 3 main types of password attacks?
The three main types of password attacks are phishing, man-in-the-middle attacks, and brute force attacks.
4. What is a password attack?
A password attack is a typical attack vector used to compromise user account authentication. It is one of the most prominent application security concerns and is responsible for most data breaches worldwide.
5. What are the most common ways of password attacks?
The most common ways of password attacks include brute-forcing, dictionary attacks, password spraying, and credential stuffing.
6. What are the different types of online attacks?
The different types of online attacks include malware attacks, phishing attacks, SQL injection attacks, cross-site scripting (XSS) attacks, denial-of-service (DoS) attacks, and more.
7. What is the most common password attack?
Phishing attacks are currently the most common type of password attack. Phishing emails and messages trick users into revealing their passwords or other personal information.
8. What are the most common password attacks?
The most common types of password attacks include phishing attacks, brute force attacks, dictionary attacks, and credential stuffing.
9. What are the risks of password attacks?
Password attacks can lead to unauthorized access to personal or sensitive information, data breaches, financial loss, identity theft, and compromised online accounts.
10. How can I protect myself from password attacks?
To protect yourself from password attacks, it is important to use strong and unique passwords, enable multi-factor authentication whenever possible, be cautious of phishing attempts, keep your software and devices updated, and use a reputable antivirus and anti-malware software. Regularly monitoring your accounts for any suspicious activities is also recommended.
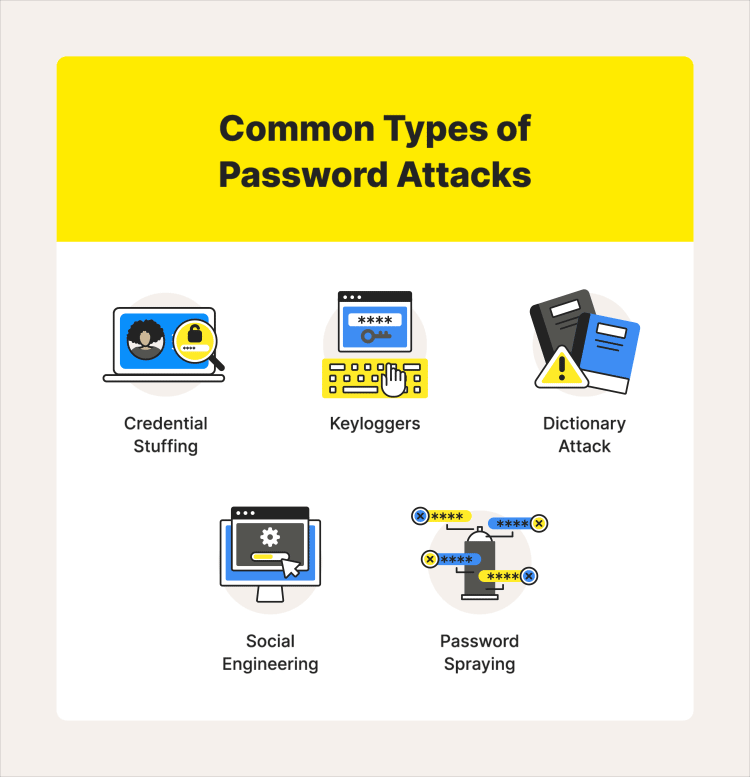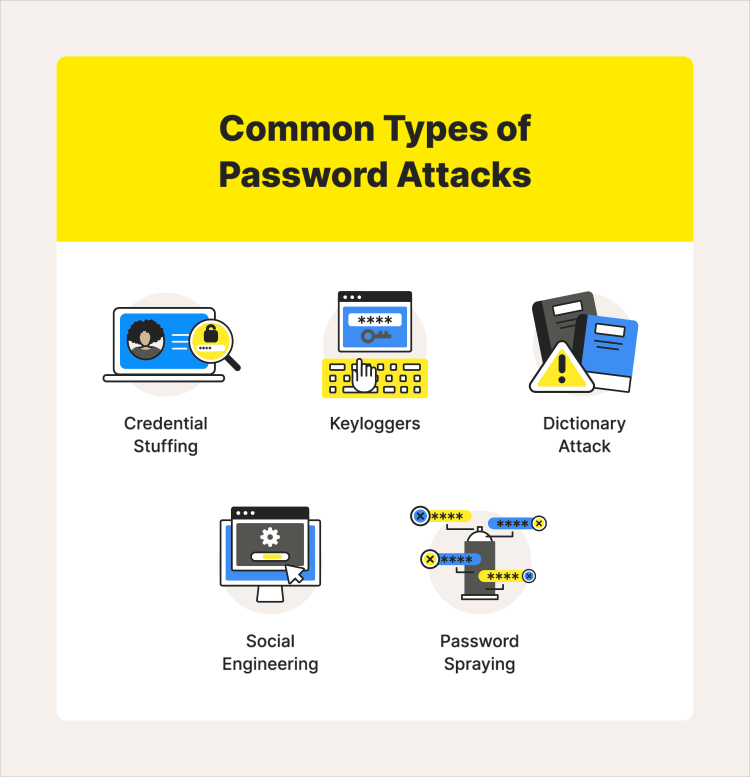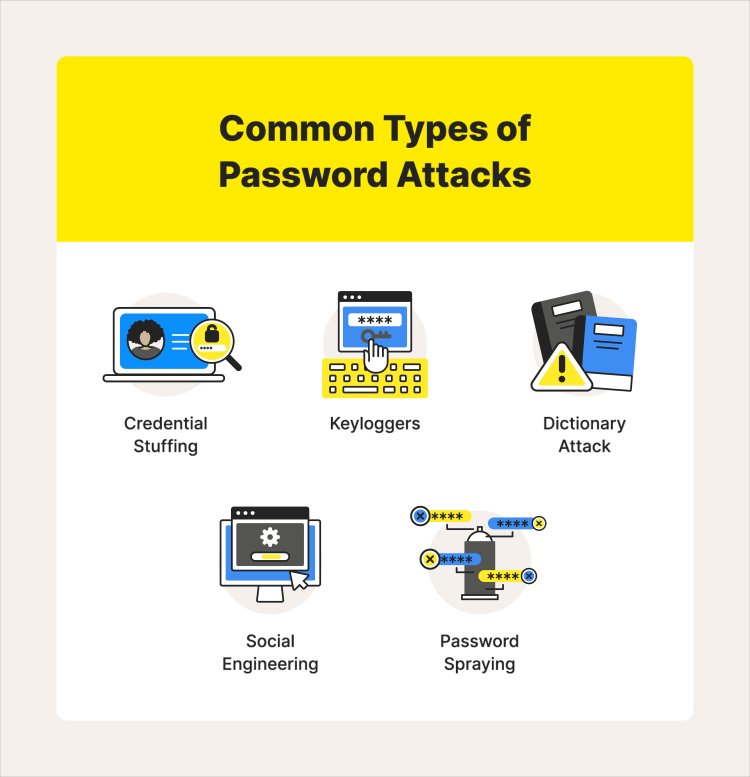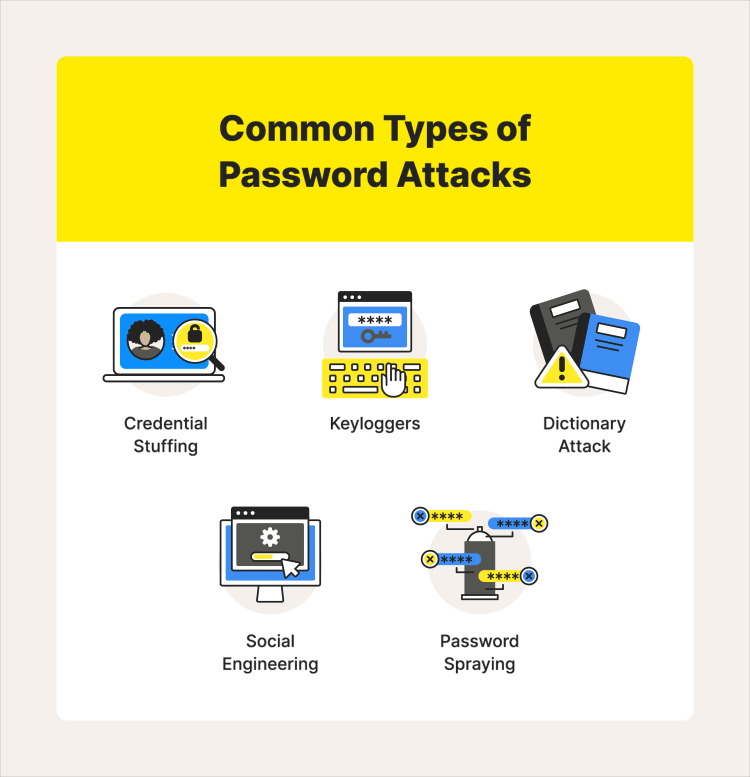
What are the active online attacks for passwords
Active Online Attacks :
An attacker must communicate with target machines to realize password access. Techniques employed by the attacker to perform active online attacks include password guessing, dictionary and brute-forcing attack, hash injection, phishing, Poisoning, using Trojan spyware key loggers, etc.
What is an example of a password attack
Password attacks are malicious ways hackers attempt to gain access to your account. Examples of password attacks include brute-force attacks, credential stuffing, and password spraying.
Cached
What are the 3 main types of password attacks
Six Types of Password Attacks & How to Stop ThemPhishing. Phishing is when a hacker posing as a trustworthy party sends you a fraudulent email, hoping you will reveal your personal information voluntarily.Man-in-the-Middle Attack.Brute Force Attack.Dictionary Attack.Credential Stuffing.Keyloggers.
Cached
What is a password attack
A password attack is a typical attack vector used to compromise user account authentication. As one of the most prominent application security concerns, it's responsible for most data breaches worldwide. Password breaches have far-reaching repercussions.
What are the most common ways of passwords attacks
The most common attack methods include brute forcing, dictionary attacks, password spraying, and credential stuffing. Brute forcing is the attempt to guess a password by iterating through all possible combinations of the set of allowable characters.
What are the different types of online attacks
7 Common Types of CyberattacksMalware. Malware refers to various forms of harmful software, such as viruses and ransomware.Phishing.SQL Injection Attack.Cross-Site Scripting (XSS)Denial-of-Service (DoS)
What is the most common password attack
1. Phishing Attacks. Phishing is currently the type of password attack that's getting the most press online—and it's easy to see why. With 75% of organizations having experienced a phishing attack, being targeted can't be avoided—but falling for phishing attacks, can be.
What are the most common password attacks
From phishing to rainbow table attacks, we'll take you through the most common types of password attacks and how they work.Phishing Attacks.Credential Stuffing Attacks.Brute Force Attacks.Dictionary Attacks.Password Spraying Attacks.Keylogger Attacks.Man-In-The-Middle Attacks.Rainbow Table Attacks.
What are the 5 types of cyber attacks
What are the 10 Most Common Types of Cyber AttacksMalware.Denial-of-Service (DoS) Attacks.Phishing.Spoofing.Identity-Based Attacks.Code Injection Attacks.Supply Chain Attacks.Insider Threats.
What are common passwords to avoid
The top 10 most common passwords list in 2023:123456.123456789.qwerty.password.12345.qwerty123.1q2w3e.12345678.
What are the top 3 most common cyber attacks
What are the 10 Most Common Types of Cyber AttacksPhishing.Spoofing.Identity-Based Attacks.Code Injection Attacks.Supply Chain Attacks.Insider Threats.DNS Tunneling.IoT-Based Attacks.
What are 3 types of network attacks
What are the Common Types of Network AttacksUnauthorized access. Unauthorized access refers to attackers accessing a network without receiving permission.Distributed Denial of Service (DDoS) attacks.Man in the middle attacks.Code and SQL injection attacks.Privilege escalation.Insider threats.
What are common password hackers using
Most hackable passwords
Second came “123456” followed by the slightly longer “123456789.” Rounding out the top five were “guest” and “qwerty.” Most of those log-ins can be cracked in less than a second.
What are the six 6 types of attacks on network security
Six Types Of Cyber Threats To Protect AgainstMalware. Malware is an umbrella term for many forms of harmful software — including ransomware and viruses — that sabotage the operation of computers.Phishing.SQL Injection Attack.Cross-Site Scripting (XSS) Attack.Denial of Service (DoS) Attack.Negative Commentary Attacks.
What is the most hacked password
USA – Top 20 Most Used Passwordspassword.123456.123456789.12345678.1234567.password1.12345.1234567890.
What types of passwords can easily be hacked into
Easy to remember sequences of numbers and letters are among the most commonly hacked passwords, according to new data. Passwords with obvious sequences of numbers like '1234' or letters like 'qwerty' (letters from the top row of the keyboard) were also among the world's most frequently hacked passwords.
What are 90% of cyber attacks
Fend Off Phishing : Learn how more than 90% of all cyber attacks begin with phishing. Find out how attackers leverage phishing attacks to gain access to protected systems, hosts, and networks.
What is the most common attacks on network today
Malware is the most common type of cyberattack, mostly because this term encompasses many subsets such as ransomware, trojans, spyware, viruses, worms, keyloggers, bots, cryptojacking, and any other type of malware attack that leverages software in a malicious way.
How do hackers know your password
The easiest and most common way that hackers get passwords is from data breaches, in which huge amounts of user data has already been leaked or stolen from companies. This data, which often includes usernames and passwords, is compiled into databases and may be sold on the dark web or downloaded freely on forums.
What methods do hackers use to steal your password
Keylogger programs enable hackers to spy on you, as the malware captures everything you type. Once inside, the malware can explore your computer and record keystrokes to steal passwords. When they get enough information, hackers can access your accounts, including your email, social media, and online banking.
What are four 4 common attacks on WIFI
The most common types of wireless network attacks are the following:packet sniffing.rogue access points.Wi-Fi phishing and evil twins.spoofing attacks.encryption cracking.MitM attacks.DoS attacks.Wi-Fi jamming.
What are the 10 types of cyber attacks
What are the 10 Most Common Types of Cyber AttacksMalware.Denial-of-Service (DoS) Attacks.Phishing.Spoofing.Identity-Based Attacks.Code Injection Attacks.Supply Chain Attacks.Insider Threats.
Which password Cannot be hacked
A strong password is a unique word or phrase a hacker cannot easily guess or crack. Here are the main traits of a reliable, secure password: At least 12 characters long (the longer, the better). Has a combination of upper and lowercase letters, numbers, punctuation, and special symbols.
What do 80% of cyber attacks involve
Recent research[3] reveals that over 80% of breaches involved the use of weak or stolen passwords; as access to corporate networks and applications are increasingly through corporate mobile devices or employee personal devices under BYOD schemes, poor cyber hygiene at an individual level does have a direct impact on …
What is the most common passwords hackers use
Most hackable passwords
| Position | Password |
|---|---|
| 1 | password |
| 2 | 123456 |
| 3 | 12123456789 |
| 4 | guest |