To format the provided text in HTML without the specified tags, the following structure can be used:
Summary of the article:
Some examples of security countermeasures include locks, card readers, biometric readers, alarms, and computers for monitoring and controlling access. Closed-Circuit Television (CCTV) integrates cameras, recorders, switches, keyboards, and monitors to allow viewing and recording of security events.
Key Points:
1. Preventative controls protect vulnerabilities and make an attack unsuccessful or reduce its impact.
2. Corrective controls reduce the effect of an attack.
3. Detective controls discover the attack and trigger preventative or corrective controls.
4. Countermeasures are actions taken to weaken the effect of another action or situation, or to make it harmless.
5. Management, operational, and technical controls (safeguards or countermeasures) are prescribed for information systems to protect confidentiality, integrity, and availability.
6. The five security measures every business needs are surveillance, digital security, off-site data storage, printer protection, and secure server rooms.
7. The three types of countermeasures are preventative, detective, and corrective.
8. Cybersecurity countermeasures are protective measures prescribed to meet security requirements for an information system.
9. The three types of countermeasures are preventative, detective, and corrective.
10. Countermeasures are categorized into protective and preventive groups.
Questions:
1. What is an example of security countermeasures?
Some examples are locks, card readers, biometric readers, alarms, and computers to monitor and control access. Closed-Circuit Television (CCTV) is the integration of cameras, recorders, switches, keyboards, and monitors to allow viewing and recording of security events.
2. What are the two types of countermeasures?
Preventative Controls – These controls protect vulnerabilities and make an attack unsuccessful or reduce its impact.
Corrective Controls – These controls reduce the effect of an attack.
Detective Controls – These discover the attack and trigger preventative or corrective controls.
3. What are countermeasures?
Also countermeasure. A counter-measure is an action that you take in order to weaken the effect of another action or a situation, or to make it harmless.
4. What are the three countermeasures?
The management, operational, and technical controls (i.e., safeguards or countermeasures) prescribed for an information system to protect the confidentiality, integrity, and availability of the system and its information.
5. What are the five security measures?
Security 101: Five Security Measures Every Business Needs
- Surveillance – Physical security and surveillance are the foundation of your security. No solid security strategy would be complete without them.
- Digital Security
- Off-site Data Storage
- Printer Protection
- Secure Server Rooms
6. What are the three types of countermeasures?
Preventative, detective, and corrective.
7. What are the three cybersecurity countermeasures?
The protective measures prescribed to meet the security requirements (i.e., confidentiality, integrity, and availability) specified for an information system.
8. What are the three types of countermeasures?
Preventative, detective, and corrective.
9. What are the categories of countermeasures?
Countermeasures are divided into two groups, namely protective and preventative.
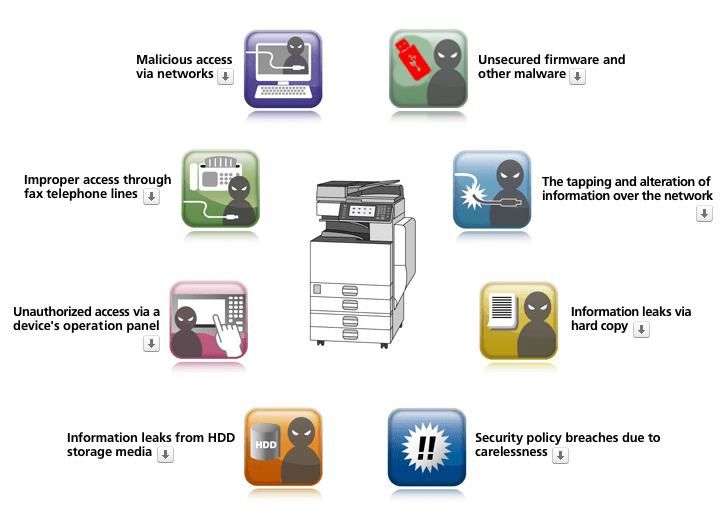
What is an example of security countermeasures
Some examples are locks, card readers, biometric readers, alarms, and computers to monitor and control access. Closed-Circuit Television (CCTV) is the integration of cameras, recorders, switches, keyboards, and monitors to allow viewing and recording of security events.
Cached
What are the 2 types of countermeasures
Tharun KrishnamoorthyPreventative Controls – These controls protect vulnerabilities and make an attack unsuccessful or reduce its impact.Corrective Controls – These controls reduce the effect of an attack.Detective Controls – These discover the attack and trigger preventative or corrective controls.
What are counter measures
also countermeasure. Word forms: plural counter-measures. countable noun. A counter-measure is an action that you take in order to weaken the effect of another action or a situation, or to make it harmless.
What are the three countermeasures
The management, operational, and technical controls (i.e., safeguards or countermeasures) prescribed for an information system to protect the confidentiality, integrity, and availability of the system and its information.
What are the 5 security measures
Security 101: 5 Security Measures Every Business NeedsSurveillance. Physical security and surveillance are the foundation of your security, no solid security strategy would be complete without them.Digital Security.Off-site Data Storage.Printer Protection.Secure Server Rooms.
What are the 3 types of countermeasures
What are the three types of countermeasures Preventative, detective, and corrective.
What are the three cybersecurity countermeasures
The protective measures prescribed to meet the security requirements (i.e., confidentiality, integrity, and availability) specified for an information system.
What are the three types of counter measures
What are the three types of countermeasures Preventative, detective, and corrective.
What are the categories of countermeasures
Countermeasures are divided into two groups, namely protective and preventative measures.
What are the three 3 basic network security measures
Privacy and integrity of sensitive information is ensured through multi-factor authentication, endpoint compliance scanning, and encryption of all transmitted data.
What are three countermeasures that can be used to prevent cryptography attacks
CountermeasuresPatented physically unclonable function (PUF) technology to secure device data.Actively monitored die shield that detects and reacts to intrusion attempts.Cryptographic protection of all stored data from discovery.
What are the six 6 basic network security measures
Here are six essential measures needed to keep your network safe.Keep Informed.Educate Your Team.Know Avenues of Attack and Preempt Them.Install Antivirus and Other Security Programs.Make Sure Your System is Physically Secure.Test Your Security.About the Author.
What are the 7 control types
When a security control is implemented, the function of the control is broadly specified into seven categories:Directive Controls.Deterrent Controls.Preventive Controls.Compensating Controls.Detective Controls.Corrective Controls.Recovery Controls.
How many basic types of counter are
How many types of the counter are there Explanation: Counters are of 3 types, namely, (i)asynchronous/synchronous, (ii)single and multi-mode & (iii)modulus counter. These further can be subdivided into Ring Counter, Johnson Counter, Cascade Counter, Up/Down Counter and such like. 5.
What are the 3 A’s of network security
Authentication, Authorization, and Accounting (AAA) is a three-process framework used to manage user access, enforce user policies and privileges, and measure the consumption of network resources.
What countermeasures can you use against network layers attacks
Firewall SecurityFirewall software is up to date on all security patches.Firewalls are placed between all untrusted networks.Logging is enabled and auditing of unusual activity occurs.Packet filtering is enabled.
What are three 3 security techniques that can be used to protect data
Enforcing communication via secure channels. Performing strong identity verification to ensure devices are not compromised. Limiting the use of third-party software and browsing to unsafe websites. Encrypting data on the device to protect against device compromise and theft.
What are the 4 pillars of network security
Every security posture is built on four pillars:
Prevention: Preparing and training before a threat/attack. Protection: Stopping a known threat/attack. Detection: Detecting an unknown threat/attack. Response: Taking action towards a threat/attack.
What are the three 3 common security controls in cyber security
There are three primary areas or classifications of security controls. These include management security, operational security, and physical security controls.
What are the 4 types of security controls
Some of the more common ones are firewalls, intrusion detection and prevention systems, access control lists, and cryptographic technologies. Each of these controls serves a different purpose.
What are the three types of counters
A combinational circuit is required to be designed and used between each pair of flip-flop in order to achieve the up/down operation.Type of up/down counters.UP/DOWN ripple counters.UP/DOWN synchronous counter.
What is a counter and its types
Counters are generally classified as either synchronous or asynchronous. In synchronous counters, all flip-flops share a common clock and change state at the same time. In asynchronous counters, each flip-flop has a unique clock, and the flip-flop states change at different times.
What are the 3 main ways to prevent security threats
How to Prevent Network AttacksInstall antivirus software. One of the first lines of defense against malware and other viruses is to install antivirus software on all devices connected to a network (Roach & Watts, 2021).Create strong passwords.Enforce security policies.Use firewalls.Monitor activity.
What are the three types of countermeasures
What are the three types of countermeasures Preventative, detective, and corrective.
How many basic types of counters are
How many types of the counter are there Explanation: Counters are of 3 types, namely, (i)asynchronous/synchronous, (ii)single and multi-mode & (iii)modulus counter.