Should I use VPN for remote desktop
While you don’t need a VPN to access or use remote desktops, it is highly recommended that you secure connections between any of your devices and the networks they connect to.
Why would you use RDS instead of VPN
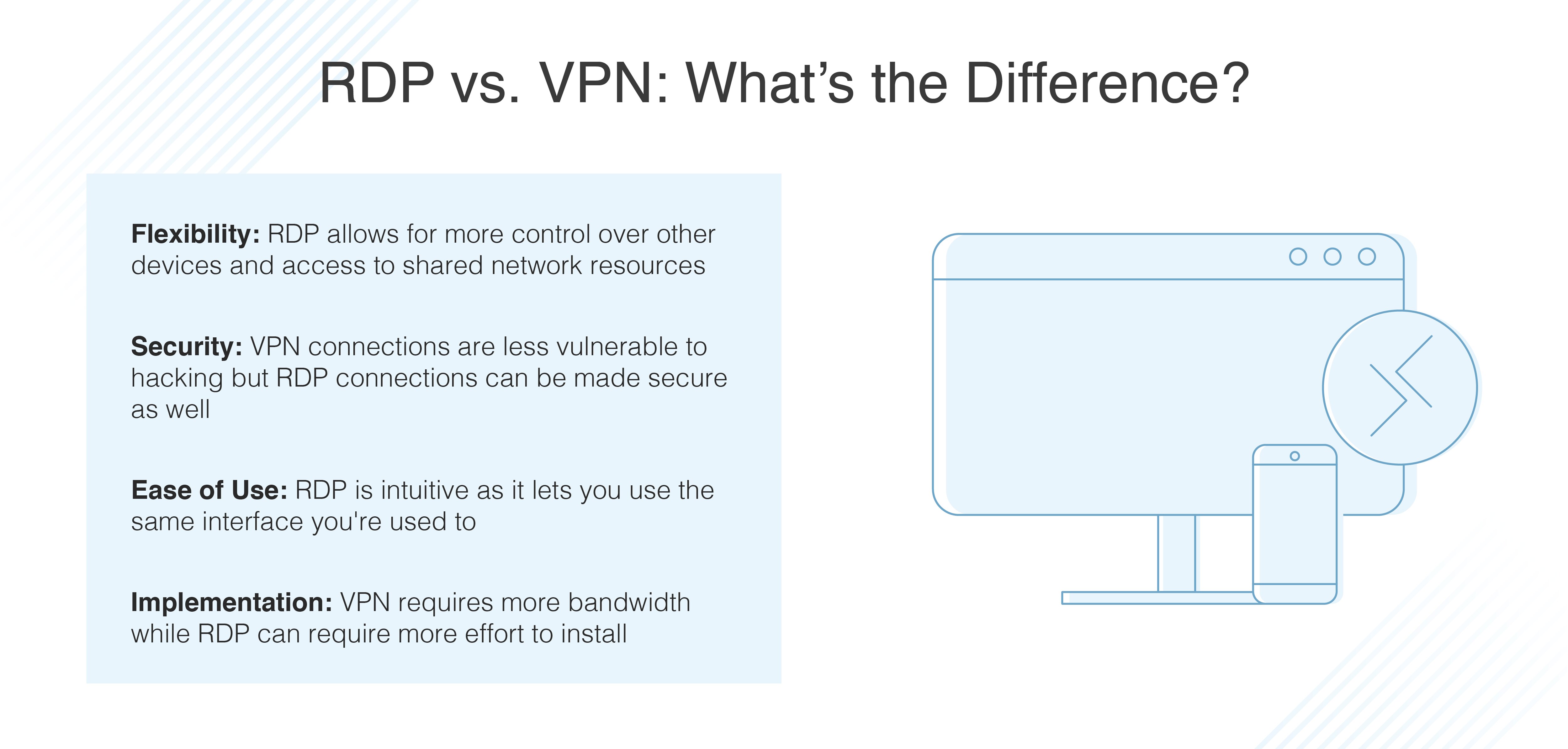
Unlike VPN, RDP typically enables users to access applications and files on any device, at any time, over any type of connection. The biggest advantage of RDP is that you have access to network resources, databases, and line-of-business software applications without the limitations and high bandwidth demands of VPN.
Is RDP secure without VPN
Is RDP safe without VPN? Unfortunately, the answer is NO. However, there still are options for us to improve the security of remote desktop connections. For example, you can disable RDP when not used, restrict access using firewalls, use third-party remote access services, etc.
Is Remote Access more secure than VPN
Although both VPN and RDP are encrypted through internet connection, a VPN connection is less accessible to threats than a remote desktop connection. For this reason, VPN is often considered more secure than RDP.
When I shouldn’t use VPN
Why shouldn’t I use a VPN? A VPN might reduce your connection speed even if your internet service provider isn’t throttling your speed. Using a VPN on mobile will increase your mobile data usage. Using a VPN is considered an offense in some countries, and you can get fined or even be incarcerated for it.
Why should you not always use a VPN
Using a VPN at home is preferable, advised even, but it isn’t always essential. The main reason it may not be necessary is that your internet activity should already be shielded by your password-protected Wi-Fi network. The other concern is connecting to a remote server can slow your connection speed.
What is the difference between RDS and VPN
RDS: Unlike VDI, RDS functions so that users on the server are provided with an identical server interface, regardless of the user or instance. VPN: The VPN only offers an established point-to-point connection via a tunnel. Processing occurs on the client system—which differs from both VDI and RDS.
Can you be tracked through RDP
1) Can Remote Desktop (RDP) Be Monitored? Yes. Using CurrentWare’s remote desktop monitoring software, administrators can track and monitor RDP sessions to ensure compliance, security, and productivity.
Should I use VPN for remote desktop
While you don't need a VPN to access or use remote desktops, it is highly recommended that you secure connections between any of your devices and the networks they connect to.
Why would you use RDS instead of VPN
Unlike VPN, RDP typically enables users to access applications and files on any device, at any time, over any type of connection. The biggest advantage of RDP is that you have access to network resources, databases, and line-of-business software applications without the limitations and high bandwidth demands of VPN.
Cached
Is RDP secure without VPN
Is RDP safe without VPN Unfortunately, the answer is NO. However, there still are options for us to improve the security of remote desktop connections. For example, you can disable RDP when not used, restrict access using firewalls, use third-party remote access services, etc.
Is Remote Access more secure than VPN
Although both VPN and RDP are encrypted through internet connection, a VPN connection is less accessible to threats than a remote desktop connection. For this reason, VPN is often considered more secure than RDP.
When I shouldn’t use VPN
Why shouldn't I use a VPNA VPN might reduce your connection speed even if your internet service provider isn't throttling your speed;Using a VPN on mobile will increase your mobile data usage;Using a VPN is considered an offense in some countries, and you can get fined or even be incarcerated for it.
Why should you not always use a VPN
Using a VPN at home is preferable, advised even, but it isn't always essential. The main reason it may not be necessary, is that your internet activity should already be shielded by your password-protected Wi-Fi network. The other concern is connecting to a remote server can slow your connection speed.
What is the difference between RDS and VPN
RDS: Unlike VDI, RDS functions so that users on the server are provided with an identical server interface, regardless of the user or instance. VPN: The VPN only offers an established point-to-point connection via a tunnel. Processing occurs on the client system—which differs from both VDI and RDS.
Can you be tracked through RDP
1) Can Remote Desktop (RDP) Be Monitored Yes. Using CurrentWare's remote desktop monitoring software you can monitor the computer activities of your end-users. This includes logon/logoff events, internet history, and application usage.
How safe is RDP over internet
Is RDP secure Remote Desktop Protocol is designed to enable authorized users to access data and remote systems. However, RDP security is not infallible. There are certain vulnerabilities inherent to using RDP that threat actors can potentially exploit to gain unauthorized access.
What are 2 drawbacks of VPNs as a remote access solution
A VPN Will Not Make You Completely Anonymous.Your Privacy Depends On Your VPN Service.It's Illegal to Use a VPN in Some Countries.Good VPN Services Cost Money.Using a VPN Slows Down Your Connection Speeds.VPNs Increase Data Consumption.Some Online Services Ban VPN Users.
Do hackers use remote access
RDP has become a common way for hackers to steal valuable information from devices and networks. It is specifically vulnerable because of its ubiquity. Since so many businesses use it, the odds accessing an improperly secured network are higher and hackers have a better chance of breaking through.
Is it OK to leave VPN on all the time
The short answer is: Yes, you should keep your VPN on at all times. By encrypting the traffic that you send and receive, VPNs can prevent your personal data from being intercepted by third parties. This data includes your web browsing history, physical location, IP address, and more.
What does VPN not protect you from
A VPN helps you stay invisible and behind the scenes, but it doesn't give you immunity against online risks like malware, ransomware, phishing attacks, or even computer viruses. That's where your antivirus software comes in.
What is the dark side of VPN
Data leakage. Whenever you use a VPN, you trust that provider with your personal and sensitive data and online activities. That is why it's important to use a provider that has robust security precautions and most free VPNs don't have that. This can lead to data leakages that put your sensitive data at risk.
Is RDP secure over the Internet
Is RDP secure Remote Desktop Protocol is designed to enable authorized users to access data and remote systems. However, RDP security is not infallible. There are certain vulnerabilities inherent to using RDP that threat actors can potentially exploit to gain unauthorized access.
Is A VPN better than a DNS server
DNS is a better option due to its lightweight nature. It does not use encryption so you can enjoy the full speed of your standard internet connection. However, keep in mind that VPNs don't always slow down your connection. Working in a government-restricted environment.
How secure is RDP over Internet
Is RDP secure Remote Desktop Protocol is designed to enable authorized users to access data and remote systems. However, RDP security is not infallible. There are certain vulnerabilities inherent to using RDP that threat actors can potentially exploit to gain unauthorized access.
Can someone access my computer remotely without me knowing
Because if a computer is remotely accessing your computer, then the screen of your computer will be locked, which means no one can remotely access your computer without letting you know it. This is what happens when someone remotely accesses your computer.
Does RDP hide IP address
Both VPN and RDP, in some way, encrypt your internet traffic. Both provide private access to a server or device that might be located thousands of miles away. If you've ever used Teamviewer or similar applications, you know what RDP is and how you can access a computer or server from anywhere.
Why you shouldn’t use VPN all the time
Why shouldn't I use a VPN A VPN might reduce your connection speed even if your internet service provider isn't throttling your speed; Using a VPN on mobile will increase your mobile data usage; Using a VPN is considered an offense in some countries, and you can get fined or even be incarcerated for it.
When should a VPN not be used
VPNs ensure data protection from hackers and secure browsing. In result, this prevents advertisers or ISPs from accessing your browsing data. At the same time, there may be times when you need to turn your VPN off. That is when you need to access local sites or devices, such as streaming platforms or a printer.
What is the most secure way to remote access
What are the types of secure remote access strategiesVirtual private network (VPN): VPNs are the most common form of remote access.IPsec VPN:SSL VPN:Desktop sharing:Secure Shell (SSH) remote access:Network access control (NAC):Single sign-on (SSO):Zero Trust network access (ZTNA):
When should you not use a VPN
VPNs ensure data protection from hackers and secure browsing. In result, this prevents advertisers or ISPs from accessing your browsing data. At the same time, there may be times when you need to turn your VPN off. That is when you need to access local sites or devices, such as streaming platforms or a printer.
Can VPNs be hacked
VPN services can be hacked, but it's extremely difficult to do so. Most premium VPNs use OpenVPN or WireGuard protocols in combination with AES or ChaCha encryption – a combination almost impossible to decrypt using brute force attacks.
Why VPN is not recommended
Why VPN is Not Secure. VPNs are insecure because they expose entire networks to threats like malware, DDoS attacks, and spoofing attacks. Once an attacker has breached the network through a compromised device, the entire network can be brought down.