Summary of the Article: Is Encryption Actually Safe?
1. Encryption provides a good level of data security and privacy when implemented correctly. However, it is important to note that no encryption is foolproof, and there can be vulnerabilities that hackers can exploit.
2. Encryption only protects the encrypted data. It does not prevent other online threats, such as malware or phishing attacks.
3. Hackers can break encryption through various methods. One common method is stealing the encryption key itself, while another is intercepting the data either before encryption or after decryption.
4. Key management is a significant downside of using encryption. Efficient key management is crucial to maintain data security measures.
5. Cracking encryption is not as difficult as it may seem. Even individuals with basic knowledge and time can potentially crack encryption. Caution is necessary when choosing encryption methods.
6. The use and regulation of encryption products vary by country. Some countries, including the United States, may ban or heavily regulate the import, export, and use of encryption products due to their potential misuse.
7. AES 256-bit encryption is considered the hardest to crack. While AES 128-bit encryption is also robust, it has never been cracked.
15 Unique Questions about Encryption:
1. Can encryption guarantee 100% data security? Encryption provides a high level of security, but it is not foolproof and can have vulnerabilities.
2. How can hackers break encryption? Hackers can break encryption by stealing encryption keys or intercepting data before or after encryption/decryption.
3. What are the downsides of using encryption? Key management can be challenging, and encryption does not protect against all online threats.
4. Is encryption easy to crack? Encryption can be cracked, especially with basic knowledge and time. Therefore, caution is necessary when choosing encryption methods.
5. Which encryption is the most secure? AES 256-bit encryption is widely considered the strongest commercially available encryption standard.
6. Is encryption illegal in the US? While encryption itself is legal in the US, its import, export, and use may be regulated or restricted due to potential misuse.
7. Can encryption be used for illegal activities? Encryption can be used for illegal activities, which is why its use is regulated in some countries.
8. Are all encryption methods equally secure? No, different encryption methods offer varying levels of security. It is important to choose strong encryption algorithms.
9. Can encryption protect against malware and phishing attacks? Encryption does not directly protect against malware or phishing attacks, as it focuses on securing data.
10. How important is key management in encryption? Effective key management is crucial for maintaining the security of encrypted data.
11. What is the role of encryption in secure internet browsing? Encryption helps protect data transmitted over the internet, making it more secure against interception.
12. Can encryption prevent data breaches? Encryption can help mitigate the impact of data breaches by making stolen data unreadable without the encryption key.
13. Are there any alternatives to encryption for data security? While encryption is a widely used method, other security measures such as access controls and firewalls also contribute to data security.
14. How can individuals ensure they are using encryption correctly? Individuals should keep software and devices updated, use strong encryption algorithms, and regularly change encryption keys.
15. Is there ongoing research to improve encryption methods? Yes, ongoing research aims to improve encryption methods and address potential vulnerabilities.
Is encryption actually safe
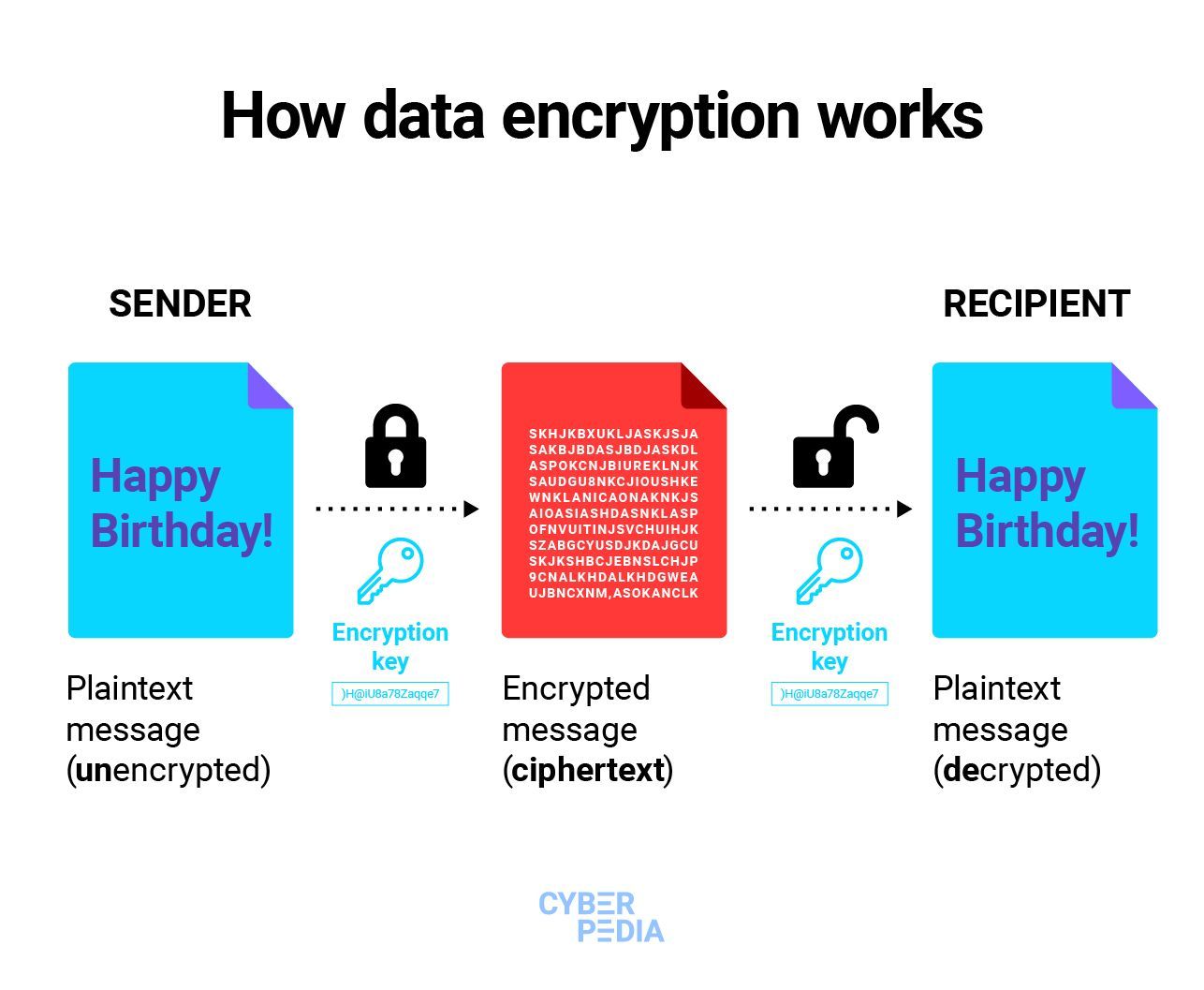
Is encryption really secure Yes, when used correctly and implemented properly, encryption can provide a good level of data security and privacy. However, it is important to remember that no encryption is foolproof and weaknesses can be discovered or exploited by hackers.
Is encryption 100 percent safe
Encryption only protects whatever is encrypted, such as your internet connection, email, or files, but it does nothing to prevent you from other online threats.
Cached
Can a hacker break encryption
Hackers can break encryption to access the data using a number of different methods. The most common method is stealing the encryption key itself. Another common way is intercepting the data either before it has been encrypted by the sender or after it has been decrypted by the recipient.
What is the downside of using encryption
One of the significant disadvantages of encryption is key management. Key management should be done efficiently as Encryption and decryption keys cannot be compromised, which might invalidate the data security measures taken.
Is it easy to crack encryption
Unfortunately, the reality is that almost anyone with very basic knowledge, and a bit of time (it took me about 4 hours), can crack your encryption. Imagine what an expert can do. Pay the due caution when choosing how to encrypt the data in your application.
Is encryption illegal in the US
Because encryption products can be used for illegal purposes, including terrorist activity, the United States and many of the countries that you may visit may ban or severely regulate the import, export and use of encryption products.
Which encryption is hardest to crack
AES 256-bit encryption is the strongest and most robust encryption standard that is commercially available today. While it is theoretically true that AES 256-bit encryption is harder to crack than AES 128-bit encryption, AES 128-bit encryption has never been cracked.
What is the hardest encryption to crack
AES 256-bit encryption is the strongest and most robust encryption standard that is commercially available today. While it is theoretically true that AES 256-bit encryption is harder to crack than AES 128-bit encryption, AES 128-bit encryption has never been cracked.
Which encryption Cannot be cracked
In cryptography, the one-time pad (OTP) is an encryption technique that cannot be cracked, but requires the use of a single-use pre-shared key that is larger in size than or equal to the size of the message being sent.
Why Let’s encrypt is a really really really bad idea
Let's Encrypt is an example where the “convenience” of automated issuance of “free” SSL certificates is a bug, not a feature. The more sites secured by Let's Encrypt certificates, the bigger the threat surface becomes because the compromise of Let's Encrypt's KMS could potentially affect a large number of sites.
Which is the safest encryption method
AES 256-bit encryption is the strongest and most robust encryption standard that is commercially available today.
How long would it take to crack 256 encryption
AES-256 encryption is virtually uncrackable using any brute-force method. It would take millions of years to break it using the current computing technology and capabilities. However, no encryption standard or system is completely secure.
What is the hardest encryption to hack
AES 256-bit encryption is the strongest and most robust encryption standard that is commercially available today. While it is theoretically true that AES 256-bit encryption is harder to crack than AES 128-bit encryption, AES 128-bit encryption has never been cracked.
Can the FBI see encrypted messages
It can see limited message content, basic user information, contacts, date and time info, encryption keys, sender and receiver information, and even your iCloud backups. Since iCloud stores non-encrypted message backups by default, that gives the FBI access to a lot of content.
Can FBI open encrypted files
While the document confirms that the FBI can't gain access to encrypted messages sent through some services, the other type of information they can glean from providers might still help authorities in other aspects of their investigations.
Who can crack 256-bit encryption
256-bit encryption is refers to the length of the encryption key used to encrypt a data stream or file. A hacker or cracker will require 2256 different combinations to break a 256-bit encrypted message, which is virtually impossible to be broken by even the fastest computers.
How easy is it to crack 256-bit encryption
With the right quantum computer, AES-128 would take about 2.61*10^12 years to crack, while AES-256 would take 2.29*10^32 years.
How hard is it to break encryption
Many modern encryption algorithms have been battle tested (sometimes for decades) with no known vulnerabilities. This, however, does not mean that such encryption cannot be broken. Breaking encryption with no known flaws is a bit like guessing a password. If you guess enough times, you will eventually get it right.
How long would it take to crack 256-bit encryption
AES-256 encryption is virtually uncrackable using any brute-force method. It would take millions of years to break it using the current computing technology and capabilities. However, no encryption standard or system is completely secure.
Can you trust Let’s Encrypt
It's simple – There's no payment, no validation emails, and certificates renew automatically. It's secure – Let's Encrypt serves as a platform for implementing modern security techniques and best practices.
Should we even bother with encryption
Without encryption, your sensitive data could be vulnerable to attack. For instance, if you store credit card numbers on a server, anyone with physical access to the server could potentially steal those numbers.
What is more secure than encryption
Hashing and encryption both provide ways to keep sensitive data safe. However, in almost all circumstances, passwords should be hashed, NOT encrypted. Hashing is a one-way function (i.e., it is impossible to "decrypt" a hash and obtain the original plaintext value).
Which encryption is least secure
AES is a widely used standard and recommended for use. WEP is the least secure wireless encryption type, and WPA2 is the most secure wireless encryption type.
Can I trust 256-bit encryption
256-bit encryption is a data/file encryption technique that uses a 256-bit key to encrypt and decrypt data or files. It is one of the most secure encryption methods after 128- and 192-bit encryption, and is used in most modern encryption algorithms, protocols and technologies including AES and SSL.
Can police see end-to-end encrypted messages
End-to-end encryption (E2EE) is a system that, amongst others, allows mobile phone users to communicate with each other without anyone else eavesdropping. So, the police cannot listen in either, even if they are authorized to tap the communication.