- What are the 5 types of security
Cybersecurity can be categorized into five distinct types:
– Critical infrastructure security
– Application security
– Network security
– Cloud security
– Internet of Things (IoT) security - How many types of IT security are there
However, for the most part, there are three broad types of IT security:
– Network security
– End-Point security
– Internet security (the cybersecurity subcategory)
The other various types of IT security can usually fall under the umbrella of these three types. - What are 4 types of information security
There are four types of information technology security you should consider or improve upon:
– Network Security
– Cloud Security
– Application Security
– Internet of Things Security - What type of software is security software
Security software is any type of software that secures and protects a computer, network or any computing-enabled device. It manages access control, provides data protection, secures the system against viruses and network/Internet based intrusions, and defends against other system-level security risks.
- What are the 7 types of cyber security
It can be divided into seven main pillars:
– Network Security: Most attacks occur over the network, and network security solutions are designed to identify and block these attacks.
– Cloud Security
– Endpoint Security
– Mobile Security
– IoT Security: Internet of Things (IoT) devices are vulnerable to cyber attacks, and IoT security focuses on protecting these devices and networks.
– Application Security
– Zero Trust: It is an approach to cybersecurity that treats all activities and behavior as potentially malicious, regardless of location or network context. - What are the 7 elements of security
The 7 Elements of Human Security are defined by the United Nations as:
– Economic Security
– Environmental Security
– Food Security
– Health Security
– Political Security
– Personal Security
– Community Security - What are the 7 types of security
There are essentially seven issues associated with human security. These are:
– Economic security
– Food security
– Health security
– Environmental security
– Personal security
– Community security
– Political security - What are the 3 types of software security
There are three software security types:
– Security of the software itself
– Security of data processed by the software
– Security of communications with other systems over networks - What are the three types of software security
There are three software security types:
– Security of the software itself
– Security of data processed by the software
– Security of communications with other systems over networks - What are the three types of security
In this article, we have examined the three basic security controls – technical, administrative, and physical.
- What are the 10 forms of cyber security
10 steps to cyber security:
– Risk management regime: Assess the risks to your organization’s information and systems by embedding an appropriate risk management regime.
– Secure configuration
– Network security
– Managing user privileges
– User education and awareness
– Incident management
– Malware prevention
– Monitoring - What are the 10 domains of cyber security
The 10 Domains of Security:
– Security Management Practices
– Access Control Systems and Methodology
– Telecommunications and Networking Security
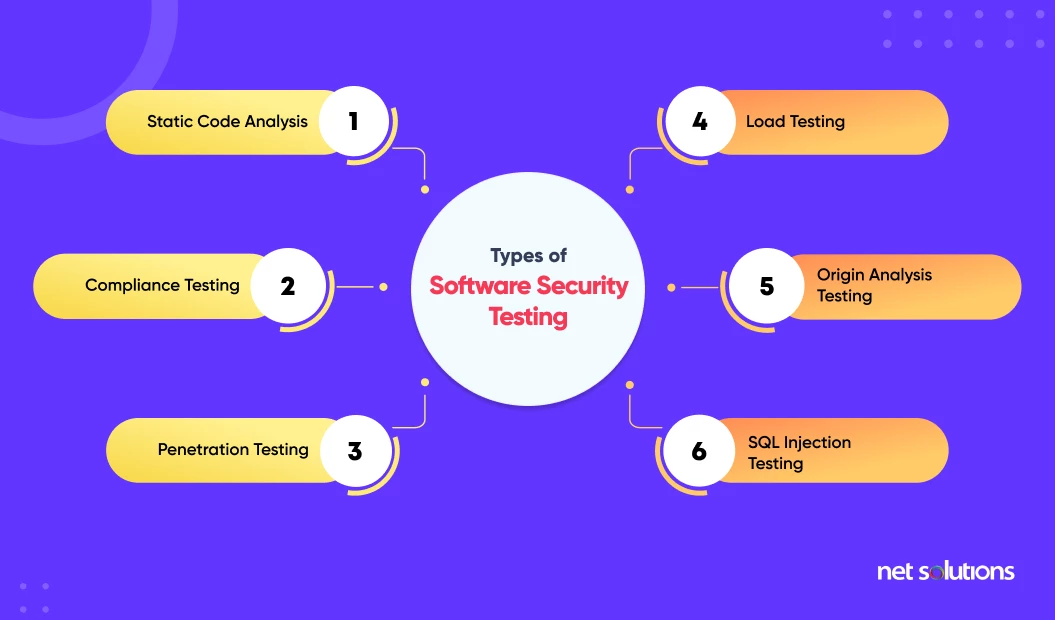
What are the 5 types of security
Cybersecurity can be categorized into five distinct types:Critical infrastructure security.Application security.Network security.Cloud security.Internet of Things (IoT) security.
Cached
How many types of IT security are there
However, for the most part, there are three broad types of IT security: Network, End-Point, and Internet security (the cybersecurity subcategory). The other various types of IT security can usually fall under the umbrella of these three types.
What are 4 types of information security
There are four types of information technology security you should consider or improve upon:Network Security.Cloud Security.Application Security.Internet of Things Security.
What type of software is security software
Security software is any type of software that secures and protects a computer, network or any computing-enabled device. It manages access control, provides data protection, secures the system against viruses and network/Internet based intrusions, and defends against other system-level security risks.
Cached
What are the 7 types of cyber security
It can be divided into seven main pillars:Network Security. Most attacks occur over the network, and network security solutions are designed to identify and block these attacks.Cloud Security.Endpoint Security.Mobile Security.IoT Security.Application Security.Zero Trust.
What are the 7 elements of security
The 7 Elements of Human Security are defined by the United Nations as: Economic, Environmental, Food, Health, Political, Personal and Community.
What are the 7 types of security
There are essentially seven issues associated human security. These are economic security, food security, health security environmental security, personal security, community security, and political security.
What are the 3 types of software security
There are three software security types: security of the software itself, security of data processed by the software, and the security of communications with other systems over networks.
What are the three types of software security
There are three software security types: security of the software itself, security of data processed by the software, and the security of communications with other systems over networks.
What are the three types of security
In this article, we have examined the three basic security controls – technical, administrative, and physical.
What are the 10 forms of cyber security
10 steps to cyber securityRisk management regime. Assess the risks to your organisation's information and systems by embedding an appropriate risk management regime.Secure configuration.Network security.Managing user privileges.User education and awareness.Incident management.Malware prevention.Monitoring.
What are the 10 domains of cyber security
The 10 Domains of SecuritySecurity Management Practices;Access Control Systems and Methodology;Telecommunications and Networking Security;Cryptography;Security Architecture and Models;Operations Security;Application and Systems Development Security;Physical Security;
What are the 4 C’s in security
These four layers are Code security, Container security, Cluster security, and Cloud security. Let's take a deep dive into each of the C's to understand them better and also answer some of the most asked questions about the 4C's.
What are the six basic security concepts
Describe accountability, authentication, authorizations, privacy, confidentiality, integrity, and non-repudiation.
What are the 11 general order of security
11 GENERAL ORDERSTo take charge of this post and all government properties in view.To walk my post in military manner.To repost all violation of orders I am instructed to enforce.To repeat all calls, from my post more distant from the guard house than my own.To quit my post only when properly relieved.
What is the 3 major aspect of security
Confidentiality, integrity and availability together are considered the three most important concepts within information security. Considering these three principles together within the framework of the "triad" can help guide the development of security policies for organizations.
What is the 3 components of security
When we discuss data and information, we must consider the CIA triad. The CIA triad refers to an information security model made up of the three main components: confidentiality, integrity and availability. Each component represents a fundamental objective of information security.
What are the 3 basic security requirements
Regardless of security policy goals, one cannot completely ignore any of the three major requirements—confidentiality, integrity, and availability—which support one another.
What are the 5 C’s of cyber security
The five C's of cyber security are five areas that are of significant importance to all organizations. They are change, compliance, cost, continuity, and coverage.
What are the 7 layers of cyber security
The Seven Layers Of CybersecurityMission-Critical Assets. This is data that is absolutely critical to protect.Data Security.Endpoint Security.Application Security.Network Security.Perimeter Security.The Human Layer.
What are the 7 aspects of security
The model consists of seven dimensions: attitudes, behaviors, cognition, communication, compliance, norms, and responsibilities.
What are the 3 key components of security
The CIA triad refers to an information security model made up of the three main components: confidentiality, integrity and availability. Each component represents a fundamental objective of information security.
What are the 7 elements of security model
The 7 Elements of Human Security are defined by the United Nations as: Economic, Environmental, Food, Health, Political, Personal and Community. We design projects and initiatives with our partners that holistically address these areas of Human Security.
What are the 3 types of force in security
There are three main types of security officers working for private and public businesses and individuals: government, in-house, and those working contractually for private security firms. Within those three main types, there are even more options – armed and unarmed, plainclothes or uniformed, on-site or remote.
What are 7th general orders
7. To talk to no one except in the line of duty. 8. To give the alarm in case of fire or disorder.