Summary
There are 4 stages of mitigating a DDoS attack: Detection, Response, Routing, and Adaptation. The key points for each stage are as follows:
- Detection: To stop a distributed attack, a website should be able to differentiate between an attack and a high volume of legitimate traffic.
- Response: Immediate response is crucial to minimize the impact of the attack.
- Routing: Traffic can be rerouted to absorb the attack and protect the target server.
- Adaptation: The mitigation strategy should adapt to evolving attack patterns to ensure continued protection.
Questions
1. What are the 4 stages of mitigating a DDoS attack?
The 4 stages of mitigating a DDoS attack are Detection, Response, Routing, and Adaptation.
2. Which service is used to mitigate DDoS attacks?
AWS Shield is used to mitigate DDoS attacks. It is integrated with AWS edge services, reducing time-to-mitigate from minutes to sub-second.
3. What is the largest mitigated DDoS attack?
The largest reported HTTP DDoS attack exceeded 71 million requests per second, according to Cloudflare’s research.
4. What are four network threat mitigation strategies?
The top four network threat mitigation strategies are:
- Application whitelisting
- Patching applications
- Patching operating systems and using the latest version
- Minimizing administrative privileges
5. How do servers protect against DDoS?
Servers can protect against DDoS attacks by relying on network security measures such as firewalls and intrusion detection systems. Additionally, anti-virus and anti-malware software can detect and remove viruses and malware.
6. What is DDoS and how do you prevent it?
A distributed denial-of-service (DDoS) attack is a type of attack where the traffic used to overwhelm the target comes from many distributed sources. To prevent it, blocking the source of traffic is not sufficient as botnets are often employed. Implementing appropriate security measures is essential.
7. How did Amazon mitigate a DDoS attack?
Amazon mitigated a DDoS attack using AWS Shield, a service designed to protect customers from DDoS attacks, bad bots, and application vulnerabilities. The attack was successfully mitigated back in February according to Amazon’s Q1 2020 threat report.
8. How long does it take to mitigate a DDoS attack?
The optimal DDoS protection solutions can detect and mitigate attacks in less than 30 seconds, making them suitable for enterprise use.
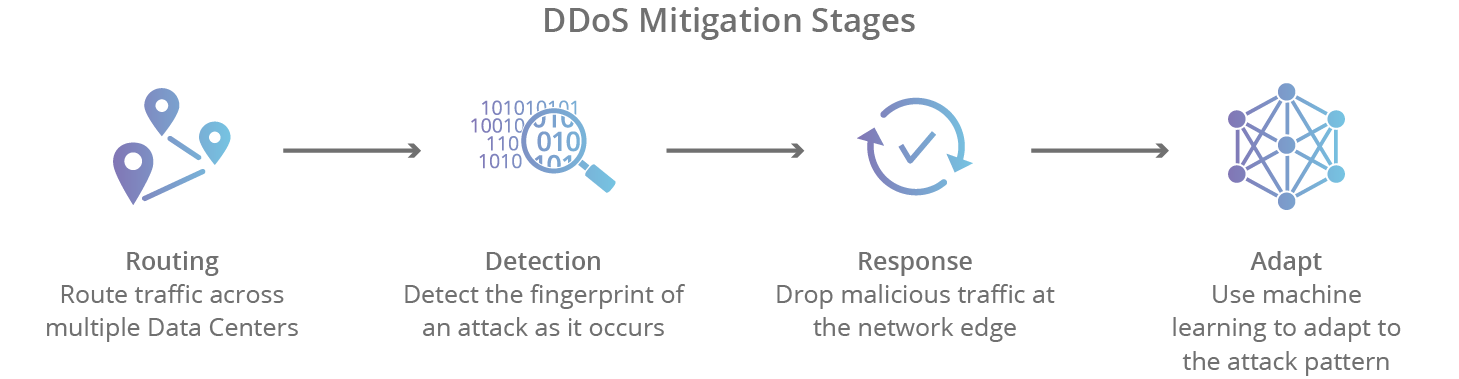
What are the 4 stages of mitigating a DDoS attack
There are 4 DDoS mitigation steps for attacks that use a cloud-based provider:Detection. To stop a distributed attack, a website should be able to differentiate between an attack and a high volume of legitimate traffic.Response.Routing.Adaptation.Scalability.Flexibility.Reliability.Network Capacity.
Which service is used to mitigate DDoS attacks
AWS Shield DDoS mitigation systems are integrated with AWS edge services, reducing time-to-mitigate from minutes to sub second.
What is the largest mitigated DDoS attack
The largest attack exceeded 71 million rps, which is the largest reported HTTP DDoS attack, according to Cloudlare's research.
What are four 4 network threat mitigation strategies
The top four mitigations are: Application whitelisting; Patching applications; Patching operating systems and using the latest version; Minimising administrative privileges. This document is designed to help senior managers in organisations understand the effectiveness of implementing these strategies.
How do servers protect against DDoS
You can rely on the following types of network security to protect your business from DDoS attempts: Firewalls and intrusion detection systems that act as traffic-scanning barriers between networks. Anti-virus and anti-malware software that detects and removes viruses and malware.
What is DDoS and how do you prevent it
A distributed denial-of-service (DDoS) is a type of DoS attack where the traffic used to overwhelm the target is coming from many distributed sources. This method means the attack can't be stopped just by blocking the source of traffic. Botnets are often employed for DDoS attacks.
How did Amazon mitigate DDoS attack
Detailing the attack in its Q1 2020 threat report, Amazon said that the attack occurred back in February, and was mitigated by AWS Shield, a service designed to protect customers of Amazon's on-demand cloud computing platform from DDoS attacks, as well as from bad bots and application vulnerabilities.
How long does it take to mitigate a DDoS attack
Protection solutions that detect and mitigate DDoS attacks in less than 30 seconds are therefore optimal for enterprise use.
What are the 3 types of mitigation cybersecurity
A cybersecurity threat mitigation strategy reduces the overall risk or impact of a cybersecurity incident by employing security policies and procedures. There are three components to risk mitigation: prevention, detection, and remediation.
What are the top four mitigation strategies
4. The top four mitigations are: application whitelisting; patching applications and operating systems and using the latest version; and minimising administrative privileges. This document is designed to help senior managers in organisations understand the effectiveness of implementing these strategies.
What is the best defense against DDoS
A Web Application Firewall (WAF) is the best defense against all DDoS attacks. It thwarts malicious traffic trying to block vulnerabilities in the application.
Do firewalls protect against DDoS attacks
A web application firewall (WAF) is a type of firewall that monitors, filters or blocks incoming traffic to a web application. It is designed to protect web applications from attacks such as DDoS attacks. A WAF can prevent a DDoS attack by blocking or rate-limiting incoming traffic that is deemed to be malicious.
Can you protect against DDoS attacks
Enroll in a DDoS protection service. Many internet service providers (ISPs) have DDoS protections, but a dedicated DDoS protection service may have more robust protections against larger or more advanced DDoS attacks.
Is it possible to stop DDoS
Broadly speaking, there are several approaches to stopping DDoS attacks. The most common solutions rely on do-it-yourself (DIY) methods, on-premise mitigation appliances and off-premise cloud-based solutions.
What are the three DDoS mitigation service providers
9 Best DDoS Protection Service Providers for 2023Akamai.Imperva.Radware.Cloudflare.Vercara.NetScout.Ribbon.Amazon Web Services.
Why is it so hard to defend DDoS
These attacks are also extremely difficult to defend against because of their distributed nature. It is difficult to differentiate legitimate Web traffic from requests that are part of the DDoS attack. There are some countermeasures you can take to help prevent a successful DDoS attack.
What makes DDoS attacks difficult to stop
During a DDoS attack, that can be thousands of constantly changing IPs and millions of packets of data to keep track of in state tables. The memory and processing resources required to do that quickly for every packet is enormous and most firewalls simply can't handle the load.
What are the six 6 threat mitigation strategies required for network security
6 strategies for cybersecurity risk mitigationRisk assessment.Establish network access controls.Continuously monitor network traffic.Create an incident response plan.Minimise your attack surface.Stay on top of patch updates.
What are the 3 types of mitigation
The types of mitigation enumerated by CEQ are compatible with the requirements of the Guidelines; however, as a practical matter, they can be combined to form three general types of mitigation: avoidance, minimization, and compensatory mitigation.
What are the five main mitigation strategies
Five risk mitigation strategies with examplesAssume and accept risk.Avoidance of risk.Controlling risk.Transference of risk.Watch and monitor risk.
Can DDoS attacks be prevented using encryption
To prevent the Denial-of-service and distributed DoS attack a client puzzle method is implemented. In order to prevent further attack in network and to enhance the security the request that is provided by the client and the file sent by the server to client is in encrypted form.
What is the best protection against DDoS
How to Stop a DDoS Attack: 5 Best Practices for DDoS Attack PreventionMake a Denial of Service Response Plan.Ensure a Resilient Infrastructure.Take Refuge in the Cloud.Deploy DDoS Protection Solutions and Threat Intelligence.
What is the best DDoS protection
Let's have a look at some of the best DDoS Protection tools as well as Anti-DDoS software available.Indusface AppTrana (FREE TRIAL)SolarWinds Security Event Manager (FREE TRIAL)Sucuri Website Firewall (LEARN MORE)StackPath Web Application Firewall (FREE TRIAL)Link11.Cloudflare.AWS Shield.Akamai Prolexic Routed.
Is it possible to stop DDoS attacks
In extreme cases, you can completely shut down the services being attacked to prevent immediate damage. While this will stop attacker traffic, it stops all user traffic in its entirety. Stopping services can make businesses lose potential customers and revenue, making it a last resort effort to stop DDoS attacks.
How do servers prevent DDoS
DDoS Protection TechniquesReduce Attack Surface Area.Plan for Scale.Know what is normal and abnormal traffic.Deploy Firewalls for Sophisticated Application attacks.