the data for various illegal activities such as identity theft, fraud, or blackmail.
2. Hackers can use the leaked data for phishing attacks
By having access to personal information such as names, email addresses, or phone numbers, hackers can create convincing phishing emails or messages to trick individuals into giving away more sensitive information or clicking on malicious links.
3. Hackers can use the leaked data for targeted attacks
If the leaked data includes specific information about individuals or organizations, hackers can use this to launch targeted attacks. They can craft personalized and convincing messages or scams, making it more likely for the recipients to fall for their tactics.
4. Hackers can use the leaked data for blackmail
If the leaked data includes compromising or sensitive information, hackers can use it to blackmail individuals or organizations. They may threaten to publish the information publicly unless a ransom is paid.
5. Hackers can use the leaked data for credential stuffing
Credential stuffing is a technique where hackers use stolen usernames and passwords from one website or service to gain unauthorized access to other accounts. By using the leaked data, hackers can try to gain access to various online platforms or services, increasing the chances of success due to individuals reusing passwords.
6. Hackers can use the leaked data for creating fake accounts
With the leaked data, hackers can create fake online accounts impersonating individuals or organizations. These fake accounts can be used for various malicious purposes, such as spreading misinformation, conducting scams, or launching further attacks.
7. Hackers can use the leaked data for social engineering attacks
By having access to personal or organizational data, hackers can manipulate individuals or employees through social engineering tactics. They may use the obtained information to appear trustworthy or credible, making it easier to deceive people into revealing sensitive information or granting unauthorized access.
8. Hackers can use the leaked data for reputation damage
In some cases, hackers may leak the data they have obtained to damage the reputation of individuals or organizations. This can have severe consequences, including financial loss, loss of trust, or even legal implications.
9. Hackers can use the leaked data for insider trading
If the leaked data includes confidential or non-public information about companies, hackers can use it for insider trading purposes. By having access to such information before it becomes public, hackers can make illicit financial gains by manipulating the stock market.
10. Hackers can use the leaked data for research and development
In rare cases, hackers may be interested in intellectual property or sensitive research and development data. They can steal this data for their own purposes, which can include gaining a competitive advantage or selling it to rival companies or nations.
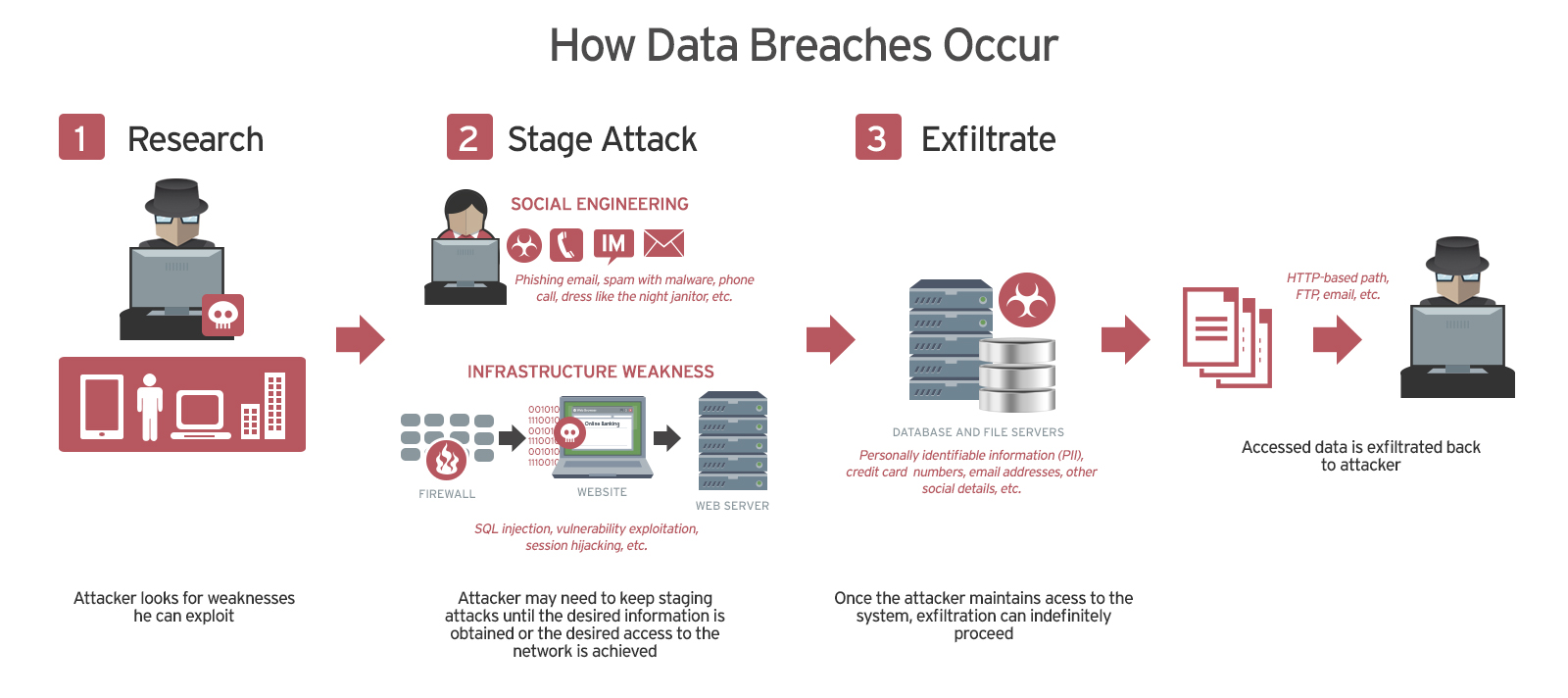
What are the 4 common causes of data breaches
Six Common Causes of Data BreachesCause 1. Insider Threats Due to Misuse of Privileged Access.Cause 2. Weak and Stolen Passwords.Cause 3. Unpatched Applications.Cause 4. Malware.Cause 5. Social Engineering.Cause 6. Physical Attacks.
How data breach can occur
Common vulnerabilities targeted by malicious criminals include the following: Weak credentials. The vast majority of data breaches are caused by stolen or weak credentials. If malicious criminals have your username and password combination, they have an open door into your network.
What are the three main causes of data breaches
A weak password, improper data extraction, and lack of email security best practices can cause a data breach worth thousands of dollars. On the other hand, we have insider threats. Disgruntled employees can cause more damage to a company than black hat hackers.
What is the leading cause of data breaches
Physical Theft of Sensitive Devices
Company devices contain sensitive information, and when these devices fall into the wrong hands, they can be leveraged to facilitate security breaches, or identity theft, leading to data breaches.
What are the three 3 kinds of data breach
Stolen login credentials, pilfered funds, or a leak of intellectual property are all types of data breaches.
How do I know if I was part of a data breach
When in doubt, contact the company directly. Obtain a copy of your credit report. Go to annualcreditreport.com or call 1-877-322-8228 to get a free copy of your credit report. You can get one free copy of your report from each of the three credit bureaus once a year.
How do hackers do data breaches
A user installs malicious software on a computer that harms the operating system. Spyware — a type of malware — then pilfers personal information from vulnerable user accounts. Ransomware. This is a type of malware that encrypts the data on a computer or system, making the data unusable unless the victim pays a fee.
What do hackers do with leaked data
1. Hackers can sell your data to other criminals
One way hackers profit from stolen data is selling it in masses to other criminals on the dark web. These collections can include millions of records of stolen data. The buyers can then use this data for their own criminal purposes.
What are examples of data breaches
Let's take a glance at the most common types of data breaches and how they affect the business.Hacking Intrusions.Insider Threat.Data on the Move.Physical Theft.Human Error.Accidental Internet Exposure.Unauthorized Access.
What prevents data breaches
A straightforward strategy for minimizing network compromise risk is keeping your company's security rating as high as possible. An internal security strategy focused on mitigating network access should also include the following common security breach controls. Firewalls. Endpoint detection and response solutions.
How can you protect yourself from data breaches
Staying secure in light of data breachesKeep an eye on your bank and credit card accounts.Monitor your identity with the help of a service.Place a fraud alert.Look into freezing your credit if needed.Update your passwords.Consider taking out identity theft coverage.Clean up your personal data online.
What is the most commonly encountered example of a data breach
Stolen passwords are one of the simplest and most common causes of data breaches.
How serious is a data breach
A data breach can easily result in identity theft when sensitive information is exposed to unauthorised individuals. Hackers can use this information to steal a person's identity and commit fraudulent activities, such as opening new accounts or making unauthorised purchases.
Why am I in a data breach for a site I never signed up for
Why do I see my username as breached on a service I never signed up to When you search for a username that is not an email address, you may see that name appear against breaches of sites you never signed up to. Usually this is simply due to someone else electing to use the same username as you usually do.
Does data breach mean hacked
The terms 'data breach' and 'breach' are often used interchangeably with 'cyberattack. ' But not all cyberattacks are data breaches—and not all data breaches are cyberattacks. Data breaches include only those security breaches in which the confidentiality of data is compromised.
Can you protect yourself from data breaches
Update software. Consider doing regular updates to software (including antivirus) on your phone, tablet, router and other devices. The latest software versions offer security patches and protection that may help you prevent cyberattacks and possible data breaches.
Does data leak mean I was hacked personally
While being a part of a data breach doesn't automatically mean your identity will be stolen, it does put you more at risk of becoming a victim of identity theft. The smartest way to protect yourself from these unsavory intruders is to make sure you're covered with identity theft protection.
How do hackers gain access to your data
One way is to try to obtain information directly from an Internet-connected device by installing spyware, which sends information from your device to others without your knowledge or consent. Hackers may install spyware by tricking you into opening spam email, or into “clicking” on attachments, images, and links in …
Can you stop a data breach
You can purchase security software and automate it to run on a continuous basis. Firewalls, anti-virus software, and anti-spyware software are important tools to defend your business against data breaches. Work closely with an internet security team or provider to set these up correctly.
How do hackers get personal information
Hackers create malicious apps that can siphon personal information from your device when you download or use the apps. Cybercriminals set up fake public Wi-Fi networks to lure and redirect people to malicious websites where they can steal personal information.
What do hackers do with data breaches
1. Hackers can sell your data to other criminals
One way hackers profit from stolen data is selling it in masses to other criminals on the dark web. These collections can include millions of records of stolen data. The buyers can then use this data for their own criminal purposes.
What are three of the top five causes of breaches
The use of weak passwords; Sending sensitive information to the wrong recipients; Sharing password/account information; and. Falling for phishing scams.
How do you know if your personal data has been leaked
Visit Have I Been Pwned
The search engine allows you to search either by your email address or phone number and will flag any breaches containing your data when they happen by cross-checking billions of leaked records added to the Have I Been Pwned database.
What can I do if my personal data has been breached
72 hours – how to respond to a personal data breachStep one: Don't panic.Step two: Start the timer.Step three: Find out what's happened.Step four: Try to contain the breach.Step five: Assess the risk.Step six: If necessary, act to protect those affected.Step seven: Submit your report (if needed)
Should I be worried if my password is in a data leak
The notice informs you that your login credentials have been compromised during a cyberattack or your password is leaked in a data breach. The usual recommendation is that you should immediately change your account password.