cument.getElementById(“start-menu-icon”).addEventListener(“click”, function(){
document.getElementById(“endpoint-security-icon”).classList.toggle(“disabled”);
});
function toggleDisabled() {
document.getElementById(“endpoint-security-icon”).classList.toggle(“disabled”);
}
Note: The above code snippet is just a representation and may not be functional in the actual HTML environment. It is provided for illustrative purposes only.
Why is endpoint security important Endpoint security is important because it helps protect endpoints like computers, laptops, and mobile devices from cyber threats. It plays a crucial role in preventing unauthorized access, data breaches, malware infections, and other malicious activities that can harm an organization’s network and sensitive information.
What are the risks of not having endpoint security Not having endpoint security can expose your devices and network to various risks, including:
1. Malware Infections: Without endpoint security, your devices are more vulnerable to malware such as viruses, trojans, ransomware, and spyware.
2. Data Breaches: Endpoint security helps protect sensitive data from being accessed or stolen by unauthorized individuals or cybercriminals.
3. Unauthorized Access: Without proper security measures, attackers can gain unauthorized access to your devices and network, potentially compromising critical information.
4. Network Vulnerabilities: Endpoints without security can serve as entry points for cyberattacks, allowing attackers to exploit network vulnerabilities and gain control.
5. Loss of Productivity: Dealing with security incidents and recovering from attacks can result in significant downtime and loss of productivity for individuals and organizations.
Does endpoint security impact system performance Endpoint security solutions are designed to minimize the impact on system performance. However, depending on the specific security measures implemented and the resources available on the endpoint devices, there might be a slight impact on system performance. This impact is usually negligible and outweighed by the benefits of having strong endpoint security in place.
Can endpoint security detect all types of threats Endpoint security solutions are designed to detect and protect against a wide range of threats. However, it’s important to note that no security solution is 100% foolproof, and new threats are constantly emerging. While endpoint security software employs various techniques such as signature-based scanning, behavior monitoring, vulnerability assessment, and threat intelligence to detect and mitigate threats, it’s crucial to stay updated with the latest security patches and keep the endpoint security solution itself up to date to ensure maximum protection against evolving threats.
How often should endpoint security be updated It is recommended to update endpoint security software regularly to ensure optimal protection against new threats. The frequency of updates may vary depending on the specific solution and the vendor’s recommendations. In general, it is advisable to enable automatic updates whenever possible to ensure continuous protection. Additionally, organizations should stay informed about the latest security updates and patches released by the vendor and promptly apply them to the endpoint security software.
Can endpoint security prevent data loss Endpoint security plays a crucial role in preventing data loss by implementing various measures such as data encryption, access controls, and data loss prevention (DLP) policies. These measures help protect sensitive data from unauthorized access, accidental sharing, or intentional exfiltration. By monitoring and controlling data transfers within the network and on endpoint devices, endpoint security solutions can prevent data loss incidents and mitigate the associated risks. However, it’s important to note that no security solution can guarantee absolute prevention of data loss, and a comprehensive approach to data protection is recommended, including regular data backups and employee awareness training.
How can endpoint security help in incident response Endpoint security solutions provide valuable support in incident response by enabling quick and effective detection, investigation, and containment of security incidents. Key features and capabilities that help in incident response include:
1. Real-time Threat Detection: Endpoint security solutions continuously monitor endpoint devices for malicious activities and promptly alert security teams about potential threats.
2. Forensics and Investigation: Endpoint security solutions log and track security incidents, providing valuable forensic data for investigating the nature and scope of the incident.
3. Quarantine and Remediation: Endpoint security solutions can isolate compromised devices from the network, preventing further spread of the incident and facilitating remediation efforts.
4. Incident Reporting and Analysis: Endpoint security solutions generate comprehensive reports on security incidents, helping security teams analyze the incident’s impact, identify trends, and implement necessary improvements in security measures.
By leveraging these capabilities, endpoint security solutions contribute to a proactive and effective incident response strategy, minimizing the potential damage caused by security breaches.
Can endpoint security protect against insider threats Endpoint security solutions can help mitigate risks associated with insider threats. By implementing access controls, monitoring user activities, and applying behavioral analysis, endpoint security solutions can detect suspicious or unauthorized actions by employees or privileged users. These solutions can also enforce security policies and restrict access privileges, preventing potential data breaches or unauthorized actions. However, it’s important to note that endpoint security is just one component of a comprehensive insider threat prevention strategy, which should also include employee training, awareness programs, and regular reviews of access controls.
Do I need endpoint security if I use a firewall While firewalls play a crucial role in network security by controlling traffic between endpoint devices and the network, they are not sufficient on their own to provide comprehensive endpoint protection. Endpoint security solutions complement the functionality of firewalls by focusing on protecting individual devices from malware, unauthorized access, and other security threats. Endpoint security takes a more granular approach, monitoring activities on the endpoint devices themselves and implementing measures like antivirus, intrusion prevention systems, and behavioral analysis. Therefore, it is recommended to use both a firewall and endpoint security solutions to ensure comprehensive protection for your network and devices.
Can endpoint security protect against zero-day attacks Endpoint security solutions are designed to detect and protect against zero-day attacks, which are previously unknown vulnerabilities exploited by cybercriminals. While traditional signature-based antivirus solutions may not be effective against zero-day attacks, modern endpoint security solutions employ advanced techniques like behavior monitoring, machine learning, and threat intelligence to detect and mitigate such threats. By analyzing patterns, behaviors, and anomalies, these solutions can identify and block zero-day attacks before they cause significant harm. However, it’s important to note that the effectiveness of protection against zero-day attacks may vary depending on the specific endpoint security solution and its capabilities. Regular updates and prompt application of security patches are also crucial in staying protected against zero-day attacks.
Can endpoint security protect against ransomware Endpoint security solutions can provide protection against ransomware by implementing various preventive measures. These measures include real-time threat detection, behavior monitoring, and application controls that help identify and block ransomware attacks. Additionally, endpoint security solutions often include features like file and data backup, encryption, and system restore capabilities to aid in recovery from ransomware attacks. However, it’s important to remember that cybercriminals are constantly evolving their tactics, and new variants of ransomware can emerge. Therefore, maintaining up-to-date endpoint security software, regularly backing up important data, and educating users about safe browsing and email practices are essential in staying protected against ransomware threats.
How does endpoint security protect against phishing attacks Endpoint security solutions utilize multiple layers of protection to guard against phishing attacks. These measures may include:
1. Email Filtering: Endpoint security solutions often employ email filtering mechanisms to identify and block phishing emails containing malicious links or attachments.
2. Web Content Filtering: By analyzing website content and reputation, endpoint security solutions can block access to known phishing websites or suspicious domains.
3. URL Reputation Analysis: Endpoint security solutions can assess the reputation of URLs in real-time, identifying potential phishing sites and warning users before they access them.
4. User Awareness Training: Endpoint security solutions can integrate with user awareness training programs, educating individuals about phishing techniques, and warning them about potential risks.
By implementing these measures, endpoint security solutions provide an extra layer of defense against phishing attacks, reducing the chances of users falling victim to fraudulent schemes. However, user awareness and caution are still crucial in preventing successful phishing attacks.
Can endpoint security protect against fileless malware Yes, endpoint security solutions can protect against fileless malware. Fileless malware is a type of malicious software that resides in the memory or executes directly from the operating system without being stored as a file on disk. While traditional antivirus solutions may have difficulty detecting fileless malware due to its non-traditional execution methods, modern endpoint security solutions employ advanced techniques like behavior monitoring, memory scanning, and anomaly detection to identify and block fileless malware attacks. By analyzing system behaviors and monitoring memory activities, these solutions can detect and mitigate the presence of fileless malware, reducing the risk of compromise and data breaches. However, it’s important to regularly update and patch endpoint security software to stay protected against evolving fileless malware threats.
How does endpoint security impact privacy Endpoint security solutions aim to protect devices and networks from security threats, and in doing so, they may collect and process certain information about the endpoints. This information may include device identifiers, network activities, and security event logs. However, reputable endpoint security solutions are designed with privacy in mind, and they should adhere to data protection regulations and industry best practices. The collected data is typically used for security purposes, such as threat detection, incident response, and performance optimization. Organizations should ensure that they choose endpoint security solutions from trusted vendors that prioritize privacy and provide transparency regarding data handling practices. It’s also important to review and understand the vendor’s privacy policy and configure the endpoint security solution according to the organization’s privacy requirements.
What are the three main steps of endpoint security
3 Steps to Better Endpoint SecurityStep 1: Establish a Security Posture. I think the first step in establishing a strong security posture is understanding what's in scope.Step 2: Investigate and Remediate. Next, you've got to investigate and remediate security incidents precisely and fast.Step 3: Know your Score.
Cached
Why is endpoint security on my computer
Endpoint protection helps protect endpoints—devices like laptops and smartphones that connect to a network—from malicious actors and exploits. Cybercriminals target endpoints because they can help attackers gain access to corporate networks.
How do you secure an endpoint
Identify your endpoint
The first step you should take to secure endpoints is cataloging and assessing vulnerabilities. Once you have this data, you can enable network access only to the approved devices and prioritize the most risky and sensitive endpoints.
How do I know if endpoint protection is installed
Verify the Endpoint Protection client installationOn the reference computer, open System Center Endpoint Protection from the Windows notification area.On the Home tab of the System Center Endpoint Protection dialog box, verify that Real-time protection is set to On.
What is an example of endpoint security
What Is an Endpoint Security Example Some examples of endpoint security solutions include: Firewalls: Firewalls can control traffic between endpoint devices and the network. They can help to block malicious traffic and protect endpoint devices from attackers.
What are key components of endpoint security
5 Key Components of Endpoint SecurityNetwork control. The network control component tracks, monitors, and filters all inbound network traffic.Application control.Data control.Browser protection.
How do I remove endpoint security from my computer
How to remove Endpoint SecurityOpen the Control Panel, Programs and Features or Apps & features (depending on your version of Windows).If any of the following ENS products are present, right-click the product and select Uninstall:Wait up to 30 minutes for background architecture files to be removed.
How do I disable endpoint security
There's an icon in your start menu or there's an icon down by the clock. The icon looks like a red shield. Click Disable Endpoint Security Firewall. If you already have the firewall disabled, you will not see this option.
Can you explain how endpoint security works
The endpoint security solution provides system admins with a centralized management console that is installed on a network or server and enables them to control the security of all devices connecting to them. Client software is then deployed to each endpoint, either remotely or directly.
How do I check my endpoint connection
Testing an endpoint connectionIn the Manage Endpoint Connections window, select the endpoint you want to work with.At the bottom of the endpoint's General tab, click Test Connection.If the connection is successful, click Close.
Is endpoint security Platform installed automatically
McAfee® Endpoint Security Platform (the McAfee® Endpoint Security Common module) is automatically installed with any Endpoint Security module.
What is endpoint security for dummies
Endpoint security is the practice of securing endpoints or entry points of end-user devices such as desktops, laptops, and mobile devices from being exploited by malicious actors and campaigns.
What is the basics of endpoint security
Endpoint security is the process of protecting devices like desktops, laptops, mobile phones, and tablets from malicious threats and cyberattacks.
How do I remove Endpoint Security from Windows 10
Go to 'Control Panel > Programs and Features'. Select 'Check Point Endpoint Security' and press 'Uninstall'.
Can I delete Endpoint Security
For Windows computers, you can delete the computer from the management UI and uninstall the Endpoint Security software remotely. Remote uninstallation is only supported on Windows platforms.
How do I remove Endpoint Security from Windows
PowerShellOpen a PowerShell Window as Administrator.Run the following command: (Get-WmiObject -Class Win32_Product -Filter "Name='Symantec Endpoint Protection'" -ComputerName . ). Uninstall()A successful uninstall will return a message that ends with "ReturnValue: 0"
How do I enable endpoints
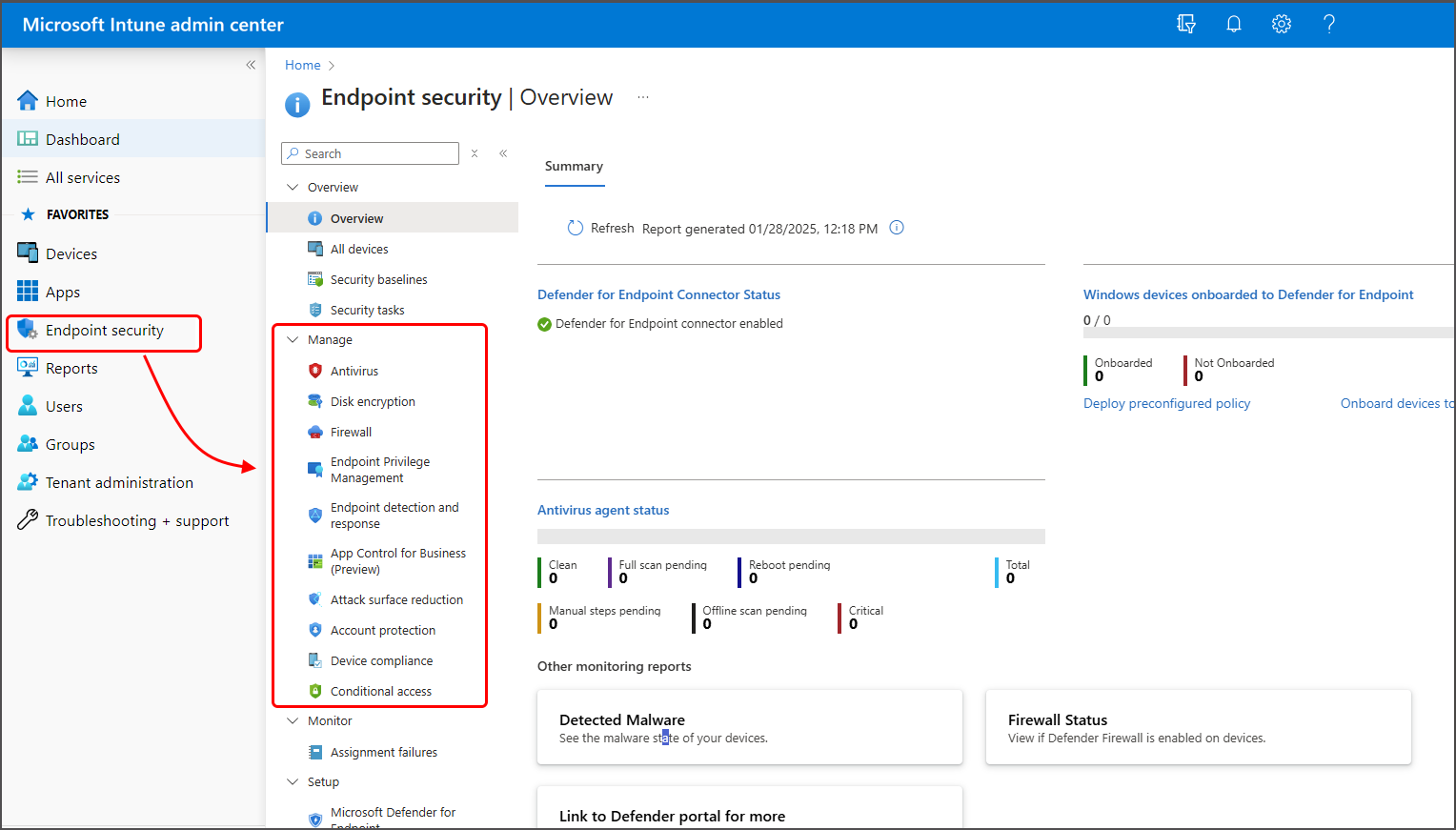
The first item you want to do is login into Microsoft Endpoint Manager admin center and select the Endpoint Security tab on the main column and then under Setup, select Microsoft Defender ATP. Under Common Share Settings select Open the Microsoft Defender ATP admin console.
How do I know if my API endpoint is working
API testing flow is quite simple with three main steps:Send the request with necessary input data.Get the response having output data.Verify that the response returned as expected in the requirement.
How to install endpoint security Platform
Installation InstructionsDownload a copy of McAfee Endpoint Security from the Software Download site and save it to your desktop.If you have an existing anti-virus software installed, you must uninstall any existing anti-virus first.Double click ENS zip file.In the folder of extracted files, double click setupEP.exe.
Where in a network is endpoint protection installed
It is installed on laptops, desktops, servers, virtual machines, as well as remote endpoints themselves. Antivirus is often part of an endpoint security solution and is generally regarded as one of the more basic forms of endpoint protection.
Who is responsible for endpoint security
An Endpoint Security Engineer protects an organization's network and computer systems from cyber threats. They are responsible for implementing and maintaining endpoint security solutions that detect, prevent, and respond to security incidents.
How do I remove Endpoint Security from my computer
How to remove Endpoint SecurityOpen the Control Panel, Programs and Features or Apps & features (depending on your version of Windows).If any of the following ENS products are present, right-click the product and select Uninstall:Wait up to 30 minutes for background architecture files to be removed.
How do I disable Endpoint Security
There's an icon in your start menu or there's an icon down by the clock. The icon looks like a red shield. Click Disable Endpoint Security Firewall. If you already have the firewall disabled, you will not see this option.
Why does it say this endpoint has been disabled
Disabled means that one or more components is not turned on. You can run the computer status report and export to CSV into Excel. It will show which component(s) are disabled.
How do I set permissions on endpoints
Set global endpoint permissionsGo to Core Services > Roles, then click Add Role.On the Description tab, complete the available fields and options. Field. Description. Name.Click Members, then add members to the role. The steps to add members to a role are different depending on the type of role. Static. Dynamic.