Summary:
1. How do you physically secure a network: There are several proven ways to secure a computer network, including installing and monitoring firewall performance, updating passwords regularly, utilizing advanced endpoint detection, creating a virtual private network (VPN), training employees, filtering and deleting spam emails, shutting down computers when not in use, and encrypting files.
2. How do I secure my network infrastructure: To improve the security of network infrastructure devices, you can segment and segregate networks and functions, limit unnecessary lateral communications, harden network devices, secure access to infrastructure devices, perform out-of-band (OoB) network management, and validate the integrity of hardware and software.
3. What are the physical security protection methods: Physical security methods include using items such as fences, gates, walls, and doors as deterrents to criminal entry. Additional measures like locks, barbed wire, visible security measures, and signs can further reduce casual attempts by cybercriminals. Technology-supported approaches can also be used for more sophisticated access controls.
4. How do I harden my home network: To secure your home Wi-Fi network, you can place your router in a central location, create a strong password and change it regularly, change the default login credentials for your router, turn on the firewall and Wi-Fi encryption, create a guest Wi-Fi network, use a Virtual Private Network (VPN), and keep your router and devices up to date.
5. What is an example of physical network security: An example of physical network security is the use of physical security controls such as CCTV cameras, motion sensors, intruder alarms, and smart alerting technology. These measures can help detect intruders quickly, allowing security staff to delay their progress and contact law enforcement if necessary.
6. What are examples of physical security: Some common examples of physical security measures include warning signs or window stickers, fences, vehicle barriers, vehicle height-restrictors, restricted access points, security lighting, and trenches.
7. What are the key aspects to secure the network: Five key elements of effective network security are identity management, perimeter security, data privacy, security monitoring, and policy management. Accurate identification of network users, hosts, applications, services, and resources is crucial. Additionally, having strong perimeter security, ensuring data privacy, implementing security monitoring measures, and proper policy management are essential.
Questions and Answers:
1. How do you physically secure a network?
In order to physically secure a network, it is important to install and monitor firewall performance, update passwords regularly, utilize advanced endpoint detection, create a virtual private network (VPN), train employees on cybersecurity best practices, filter and delete spam emails, shut down computers when not in use, and encrypt files to protect sensitive data.
2. How can you improve the security of network infrastructure devices?
To improve the security of network infrastructure devices, you can segment and segregate networks and functions to limit access, restrict unnecessary lateral communications, harden network devices by updating firmware and disabling unnecessary features, secure access to infrastructure devices using strong authentication methods, perform out-of-band (OoB) network management to separate network traffic, and regularly validate the integrity of hardware and software to detect any tampering or vulnerabilities.
3. What are some physical security protection methods?
Physical security protection methods include using physical deterrents such as fences, gates, walls, and doors to prevent unauthorized access. Additional measures like locks, barbed wire, visible security measures, and signs can further deter potential intruders. Technology-supported approaches can also be used, such as biometric systems or access control systems.
4. How can I harden my home network?
To harden your home network, it is recommended to place your router in a central location to maximize coverage, create a strong Wi-Fi password and change it regularly, change the default router login credentials to prevent unauthorized access, turn on the firewall and Wi-Fi encryption to protect against external threats, create a separate guest Wi-Fi network for visitors to isolate them from your main network, use a VPN for secure remote access, and ensure that both your router and devices connected to the network are kept up to date with the latest security patches.
5. Can you provide an example of physical network security?
An example of physical network security is the use of surveillance cameras, motion sensors, and intrusion alarms in a business setting. These devices can help monitor and detect any unauthorized physical access to the premises, allowing security personnel to respond promptly and prevent potential security breaches.
6. What are some common examples of physical security measures?
Common examples of physical security measures include the use of warning signs or window stickers to deter intruders, the installation of fences or barriers around a premises, the implementation of access control systems with key cards or biometrics, the use of security lighting to enhance visibility, and digging trenches or creating physical obstacles to restrict access to sensitive areas.
7. What are the key aspects of network security?
The key aspects of network security include identity management, which involves accurately identifying and authenticating users, hosts, applications, services, and resources within the network. Perimeter security, including firewalls and intrusion detection systems, protects the network from external threats. Data privacy measures safeguard sensitive information, while security monitoring helps detect and respond to potential security incidents. Policy management involves defining and enforcing effective security policies to ensure compliance and mitigate risks.
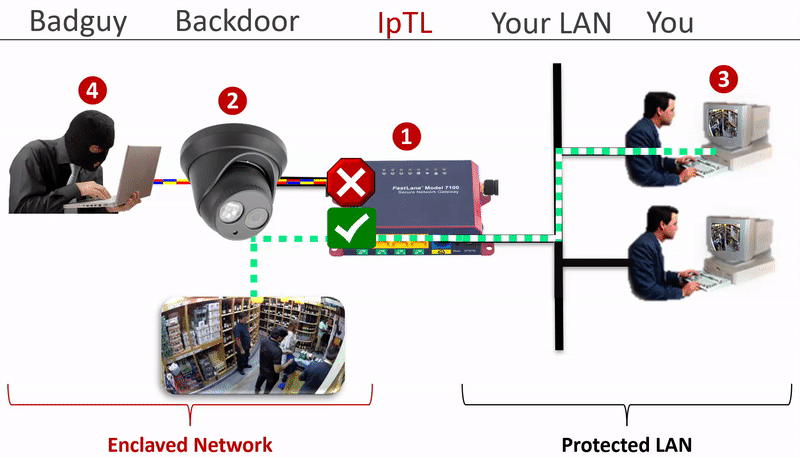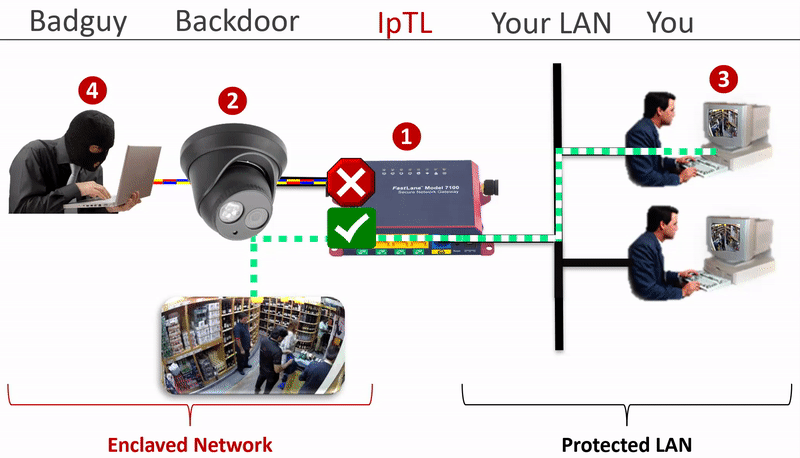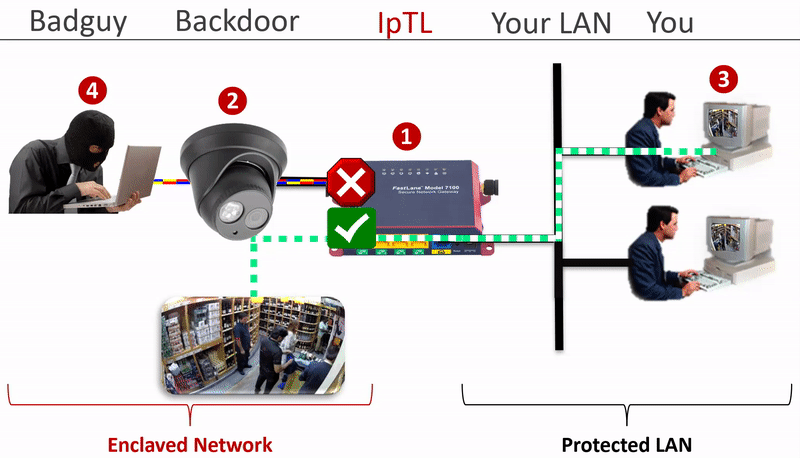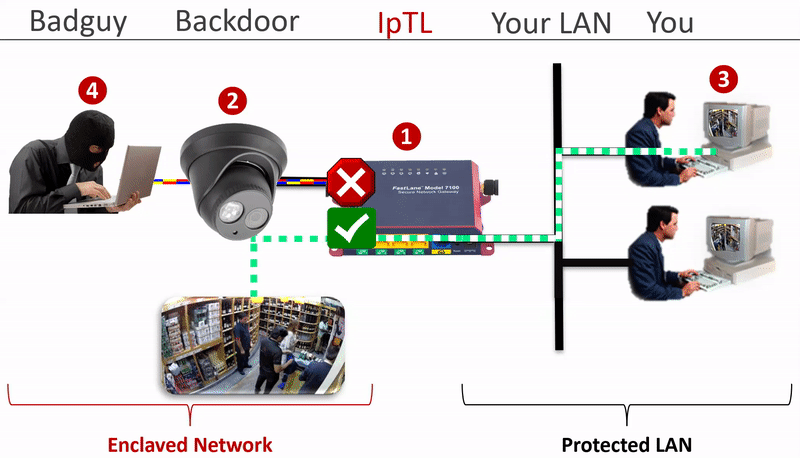
How do you physically secure a network
10 Proven Ways to Secure a Computer NetworkInstall and monitor firewall performance.Update Passwords When Needed and/or Yearly.Lean on Advanced Endpoint Detection.Create a virtual private network (VPN)Train your employee.Filter and delete spam emails.Shut down computers when not in use.Encrypt your files.
Cached
How do I secure my network infrastructure
How can you improve the security of network infrastructure devicesSegment and segregate networks and functions.Limit unnecessary lateral communications.Harden network devices.Secure access to infrastructure devices.Perform out-of-band (OoB) network management.Validate integrity of hardware and software.
Cached
What are the physical security protection methods
Items such as fences, gates, walls and doors all act as physical deterrents to criminal entry. Additional locks, barbed wire, visible security measures and signs all reduce the number of casual attempts carried out by cybercriminals. More sophisticated access controls involve a technology-supported approach.
How do I harden my home network
How to secure your home Wi-Fi network.Place your router in a central location.Create a strong Wi-Fi password and change it often.Change the default router login credentials.Turn on the firewall and Wi-Fi encryption.Create a guest Wi-Fi network.Use a VPN.Keep your router and devices up to date.
What is an example of physical network security
Physical security controls examples include CCTV cameras, motion sensors, intruder alarms and smart alerting technology like AI analytics. If an intruder is spotted quickly, it makes it much easier for security staff to delay them getting any further, and to contact law enforcement if needed.
What are examples of physical security
Some of the most common examples are also the most basic: warning signs or window stickers, fences, vehicle barriers, vehicle height-restrictors, restricted access points, security lighting and trenches.
What are the key aspects to secure the network
Five key elements of effective network security.Identity. Accurate and positive identification of network users, hosts, applications, services, and resources is a must.Perimeter security.Data privacy.Security monitoring.Policy management.
What are four ways of physically protecting a network
4 Ways to Ensure Network Physical SecurityProtect the Perimeter.Control Access to the Facility.Monitor the Entire Site.Provide Security at the Cabinet Level.
What are 4 examples of physical security
Some of the most common examples are also the most basic: warning signs or window stickers, fences, vehicle barriers, vehicle height-restrictors, restricted access points, security lighting and trenches.
What is best security for a home network
Implement WPA3 or WPA2 on the wireless network
To keep your wireless communications confidential, ensure your personal or ISP- provided WAP is capable of Wi-Fi Protected Access 3 (WPA3). If you have devices on your network that do not support WPA3, you can select WPA2/3 instead.
How do I harden my router and switches
Change the default password!Disable IP directed broadcasts.Disable HTTP configuration for the router, if possible.Block ICMP ping requests.Disable IP source routing.Determine your packet filtering needs.Establish Ingress and Egress address filtering policies.Maintain physical security of the router.
What is physical network security
Physical Network Security
Physical security controls are designed to prevent unauthorized personnel from gaining physical access to network components such as routers, cabling cupboards and so on. Controlled access, such as locks, biometric authentication and other devices, is essential in any organization.
What are the 5 principles of physical security
These principles are preparation, detection, deterrence, delay, and defense. The world of physical security planning and design conceptualizes layering key elements of security when developing protection measures for facilities or infrastructure.
What are the three 3 basic network security measures
Privacy and integrity of sensitive information is ensured through multi-factor authentication, endpoint compliance scanning, and encryption of all transmitted data.
What are the 3 elements of network security
The CIA triad refers to an information security model made up of the three main components: confidentiality, integrity and availability. Each component represents a fundamental objective of information security.
What is an example of a physical network security
Physical security controls examples include CCTV cameras, motion sensors, intruder alarms and smart alerting technology like AI analytics. If an intruder is spotted quickly, it makes it much easier for security staff to delay them getting any further, and to contact law enforcement if needed.
What are the 3 most important components of physical security
The four components are:Deterrence. The initial layer of security; the goal of deterrence is to convince unwanted persons that a successful effort to enter an unauthorized area is unlikely.Detection.Delay.Response.
What is the strongest home network encryption
When choosing from among WEP, WPA, WPA2 and WPA3 wireless security protocols, experts agree WPA3 is best for Wi-Fi security. As the most up-to-date wireless encryption protocol, WPA3 is the most secure choice.
What is the strongest form of home network encryption
WPA2 uses the Advanced Encryption Standard (AES) which is also used by the U.S. government to protect classified documents. This is the strongest level of security you can provide for your home wifi network.
What does it mean to harden a network
In computer security, network hardening is the process of reviewing a connected system, identifying its vulnerabilities and implementing mechanisms that reduce its known (surface) vulnerabilities.
What does hardening a router mean
Hardening a router means that the router is secured against attacks as best as possible. This article discusses various means of making sure your routers are set up with maximum security, including manually hardening the router and router hardening with Cisco SDM.
What are the 3 D’s of physical security
These are the three Ds of security: deter, detect, and delay. The three Ds are a way for an organization to reduce the probability of an incident.
What is the best protection for network security
Firewall. Firewalls control incoming and outgoing traffic on networks, with predetermined security rules. Firewalls keep out unfriendly traffic and is a necessary part of daily computing.
What are the six 6 basic network security measures
Here are six essential measures needed to keep your network safe.Keep Informed.Educate Your Team.Know Avenues of Attack and Preempt Them.Install Antivirus and Other Security Programs.Make Sure Your System is Physically Secure.Test Your Security.About the Author.
What are the 5 types of network security
Types of Network Security ProtectionsFirewall. Firewalls control incoming and outgoing traffic on networks, with predetermined security rules.Network Segmentation.Remote Access VPN.Email Security.Data Loss Prevention (DLP)Intrusion Prevention Systems (IPS)Sandboxing.Hyperscale Network Security.