Keyloggers: Installation, Detection, and Removal
Summary: This article provides insights into keyloggers, focusing on their installation, detection, and removal. Keyloggers are software programs that monitor and record keystrokes on a user’s computer. They can be deployed through infected applications or websites and can go undetected by security software.
Key Points:
- A keylogging software program can be installed without physical access to the user’s computer.
- Software keyloggers are typically installed when the user downloads an infected application.
- Suspicious hardware and unknown processes are common signs of keylogger infection.
- Keyboard and mouse malfunction can also indicate the presence of a keylogger.
- Keyloggers can be installed through webpage scripts, exploiting vulnerable browsers.
- Hackers may use keyloggers to exploit and infect systems, often downloading and installing additional malware.
- Removing keyloggers can be challenging; wiping the device is the most effective method.
- Keyloggers can be hidden in the temporary folder, disguising themselves as genuine files.
- Hardware keyloggers are difficult to detect, as they are physical devices disguised within computer cabling or USB adapters.
- Frequent and thorough device hardware checks are necessary to detect hardware keyloggers.
Questions:
- Do keyloggers have to be physically installed?
- How are keyloggers deployed?
- How do you know if someone is keylogging you?
- How do hackers install keyloggers?
- Are keyloggers hard to remove?
- Can keyloggers be hidden?
- Can keyloggers go undetected?
- Are keyloggers hard to detect?
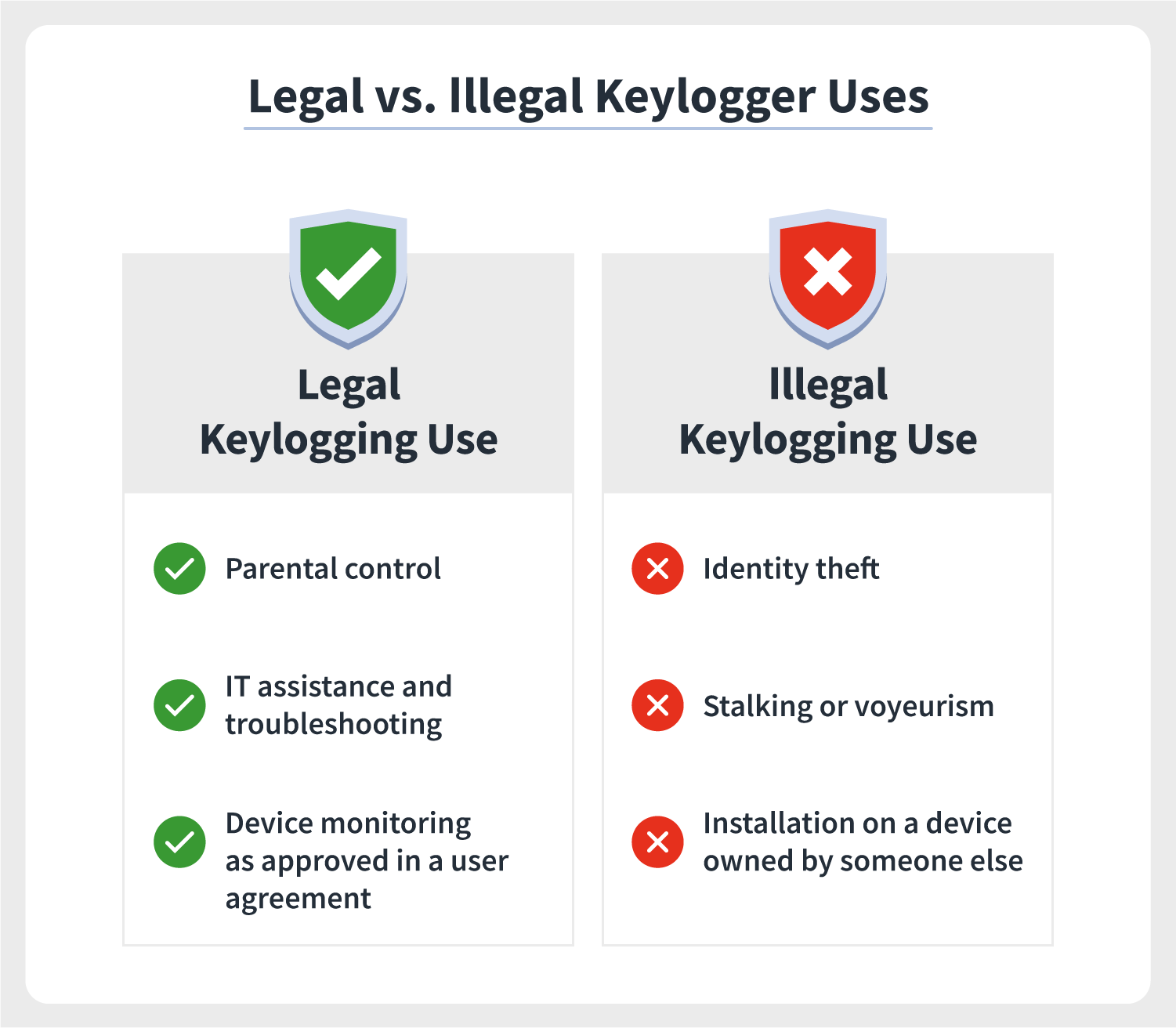
A keylogging software program does not require physical access to the user’s computer for installation.
A software keylogger is put on a computer when the user downloads an infected application. Once installed, the keylogger monitors the keystrokes on the operating system and records them.
Common signs of keylogger infection include suspicious hardware, unknown processes, and malfunctioning keyboard and mouse.
Keyloggers can be installed through webpage scripts by exploiting vulnerable browsers. They may also exploit infected systems to download and install other malware.
Keyloggers can be challenging to remove. If all else fails, wiping the device is the most effective way to remove malware, including keyloggers.
A keylogger can hide in the temporary folder, pretending to be a genuine file.
Hardware keyloggers can go undetected by security software and require thorough device hardware checks for detection.
Hardware keyloggers are difficult to detect as they can be disguised in computer cabling or USB adapters. Physical access to the device is required for installation.
Do keyloggers have to be physically installed
A keylogging software program does not require physical access to the user's computer for installation.
How are keyloggers deployed
A software keylogger is put on a computer when the user downloads an infected application. Once installed, the keylogger monitors the keystrokes on the operating system you are using, checking the paths each keystroke goes through. In this way, a software keylogger can keep track of your keystrokes and record each one.
Cached
How do you know if someone is keylogging you
What are the common signs of keylogger infectionSuspicious Hardware: There are two types of hardware modules are there.Unknown process: Software Keyloggers are also an application like others.Keyboard and mouse malfunction: You may experience your mouse and keyboards behave out of your control.
How do hackers install keyloggers
Keyloggers can be installed through webpage script. This is done by exploiting a vulnerable browser and the keystroke logging is launched when the user visits the malicious website. a keylogger can exploit an infected system and is sometimes capable to download and install other malware to the system.
Are keyloggers hard to remove
Keyloggers can be challenging to deal with and hard to remove from your device. If all else fails, you can always resort to wiping everything off on your phone. It's the most effective way to remove malware and surveillance apps, including keyloggers. Just make sure you back up any important files beforehand.
Can keyloggers be hidden
The temp folder is the storage of temporary files. A keylogger may hide in there and pretend as a genuine file.
Can keyloggers go undetected
While uncommon, hardware keyloggers are particularly dangerous because they can't be detected by security software. And unless the victim thoroughly and frequently checks their device hardware, they're likely to go unnoticed.
Are keyloggers hard to detect
Hardware keyloggers are physical devices that record every keystroke. Cybercriminals can disguise them in the computer cabling or in a USB adapter, making it hard for the victim to detect. However, because you need physical access to the device to install a hardware keylogger, it isn't as commonly used in cyberattacks.
Can a keylogger be detected
You can periodically manually review active processes and installed programs, but hackers often make keyloggers appear like legitimate programs. Because of that, antivirus software is the most reliable way to monitor for keyloggers and other forms of malware.
Where are keyloggers located
Hardware Keyloggers
These can easily be embedded within a computer's internal hardware, fixed as a hardware bug inside the keyboard, or installed inside the wiring between the keyboard and CPU. While uncommon, hardware keyloggers are particularly dangerous because they can't be detected by security software.
