n in. Disabling two-factor authentication removes this added layer of security and makes it easier for malicious actors to gain unauthorized access to your account. It is strongly recommended to keep two-factor authentication enabled to protect your sensitive information.
Is two-factor authentication enough to protect my accounts from hackers While two-factor authentication significantly improves account security, it is not foolproof. Hackers are constantly finding new ways to bypass security measures. It is important to follow other best practices such as using strong, unique passwords, regularly updating software, and being cautious of phishing attempts. Two-factor authentication should be seen as an additional layer of security rather than the sole solution to account protection.
What are some alternatives to two-factor authentication There are several alternatives to two-factor authentication, such as multi-factor authentication (MFA), passwordless authentication, and biometric authentication. MFA adds additional layers of security beyond just a second factor, making it more secure. Passwordless authentication uses methods like biometrics or cryptographic keys instead of traditional passwords. Biometric authentication, as mentioned earlier, uses unique physical characteristics like fingerprints or facial recognition to verify identity. Each of these alternatives has its own advantages and considerations, so it’s important to choose the one that best fits your security needs.
How can I protect myself from phishing attacks when using two-factor authentication Phishing attacks are a common method used by hackers to trick users into revealing their credentials and bypassing two-factor authentication. To protect yourself, be cautious of suspicious emails or messages that ask for sensitive information. Always verify the legitimacy of the website or service before entering your credentials. Additionally, consider using a security solution that provides anti-phishing features and educates you on how to identify and avoid phishing attempts.
Can someone else use my two-factor authentication code Two-factor authentication codes are usually generated for a specific user’s account and cannot be reused. However, if someone gains unauthorized access to your account and knows your login credentials, they may be able to intercept the two-factor authentication code before you are able to use it. This can be done using phishing techniques, malware, or by exploiting vulnerabilities in the login process. It is important to keep your devices and accounts secure to minimize the chances of such attacks.
Is two-factor authentication only necessary for online accounts Two-factor authentication is commonly used to secure online accounts, such as email, social media, and banking accounts. However, it can also be implemented for other systems and devices that require security, such as computer logins or access to physical facilities. Implementing two-factor authentication in these scenarios can provide an additional layer of protection against unauthorized access.
Can I use the same two-factor authentication app for multiple accounts Yes, many two-factor authentication apps allow you to add multiple accounts. This means you can use the same app to generate verification codes for different online services or accounts. However, it is recommended to use different verification methods for different accounts to enhance security. Additionally, if the two-factor authentication app supports cloud backup or syncing, it is important to enable this feature to prevent data loss in case of device failure or loss.
How often should I update my two-factor authentication settings It is recommended to periodically review and update your two-factor authentication settings to ensure maximum security. This includes adding new devices or removing old ones, updating recovery phone numbers or email addresses, and reviewing the list of trusted devices or application-specific passwords. Regularly updating these settings can help protect against potential security breaches and ensure that your two-factor authentication remains effective.
What happens if I lose access to my two-factor authentication device Losing access to your two-factor authentication device can be problematic as it may prevent you from being able to sign in to your accounts. To prevent this situation, it is recommended to have backup codes or alternative recovery methods set up, such as using backup phone numbers or email addresses. These methods can help you regain access to your accounts if you lose your primary two-factor authentication device. Additionally, it is important to securely store and keep track of these backup codes or recovery methods to prevent unauthorized access.
What are the main benefits of using two-factor authentication Two-factor authentication provides several benefits for account security. It adds an extra layer of protection beyond just a password, making it harder for malicious actors to gain unauthorized access. Two-factor authentication also helps prevent unauthorized access even if the password is compromised, guessed, or phished. It can significantly reduce the risk of account breaches and protect sensitive information. Additionally, two-factor authentication can give users peace of mind knowing that their accounts are more secure.
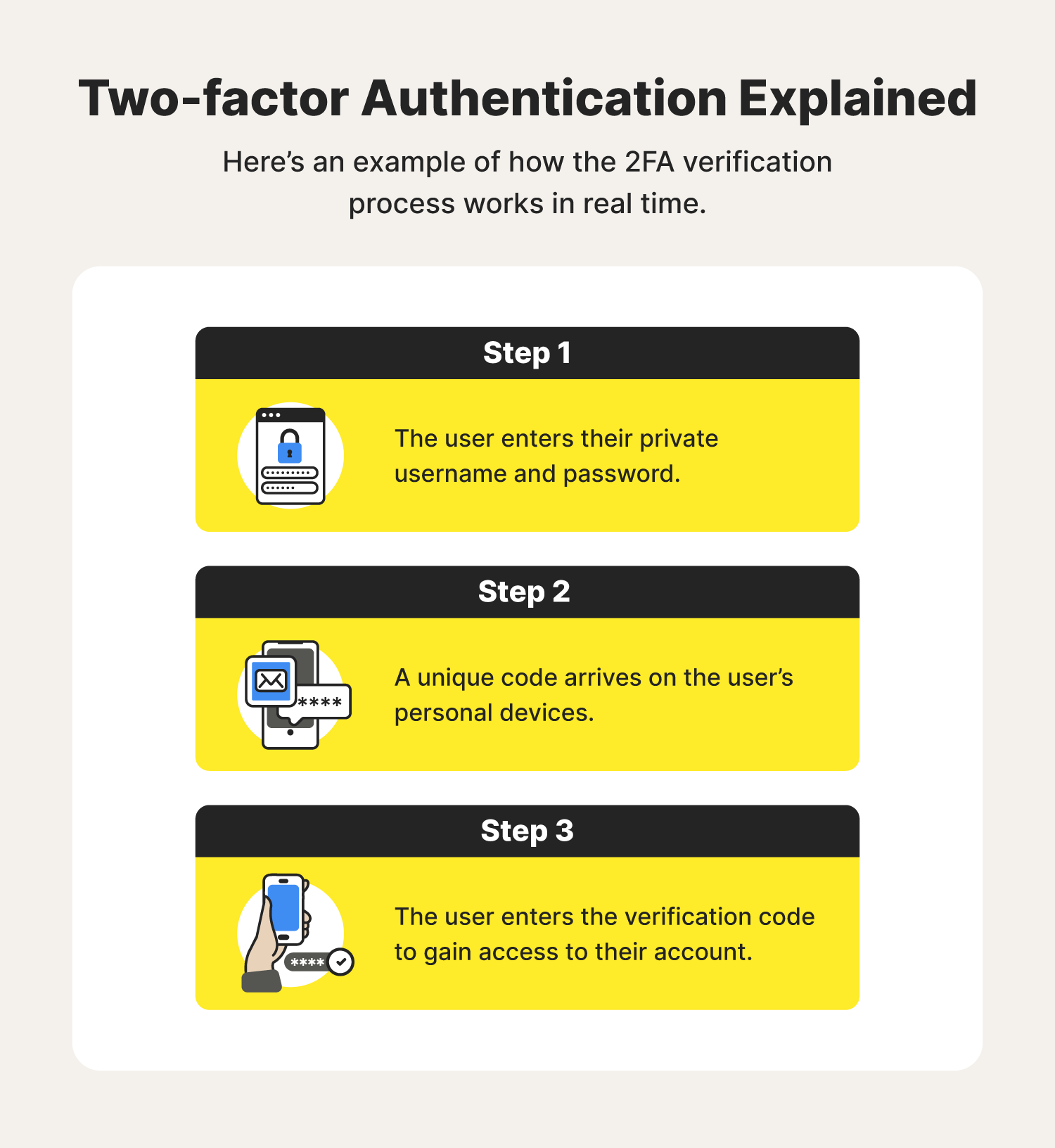
What is the safest 2 factor authentication
With the biometric lock enabled, the user has to scan their fingerprint or face before they can see the passcode. This extra 2FA security step can thwart malicious actors who stole or got remote access to the phone. This makes enabling a biometric lock an essential 2FA security best practice.
What is Norton two-factor authentication
An extra layer of protection. Your first layer of protection is your password. Two-Factor Authentication adds a second layer of protection—a unique verification code that changes every time you sign in. Even if someone steals or guesses your password, they can't access your account.
CachedSimilar
What is the difference between LifeLock and NortonLifeLock
What is the difference between LifeLock Standard and Norton 360 with LifeLock Select LifeLock Standard doesn't include features to help protect your devices or tools to help protect your online privacy like those included with Norton 360.
What is better security than two-factor authentication
MFA is more secure than 2FA. But many companies still use 2FA for two reasons. One, it's cheaper and easier to setup. Most software suites support 2FA, but not all of them support MFA.
Can hackers beat two-factor authentication
Consent Phishing
This is where hackers present what looks like a legitimate OAuth login page to the user. The hacker will request the level of access they need, and if access is granted, they can bypass MFA verification.
What are the flaws of two-factor authentication
The problem with 2FA isn't 2FA itself. It's how it's deployed. If an attacker can break any link in the 2FA chain, he can break into your systems. Some of the methods recently used to crack 2FA are good old phishing and social engineering.
Should I always use 2 factor authentication
2FA is essential to web security because it immediately neutralizes the risks associated with compromised passwords. If a password is hacked, guessed, or even phished, that's no longer enough to give an intruder access: without approval at the second factor, a password alone is useless.
Should I turn off two-factor authentication
Your account is more secure when you need a password and a verification code to sign in. If you remove this extra layer of security, you will only be asked for a password when you sign in. It might be easier for someone to break into your account.
What is the downside of LifeLock
Downsides. Only one credit bureau is monitored with the first three plans. You have to pony up and pay for the most expensive plan to monitor all three credit bureaus. Since not all companies report to all three bureaus, there could be fraud that you're not made aware of.
Is there a better option than LifeLock
myFICO. myFICO is a credit and identity monitoring solution that allows you to monitor credit reports from all three bureaus and view your FICO scores. With three-bureau reports, you can view side-by-side comparisons of your credit reports from each credit provider, helping you identify any suspicious activity.
Which is the safest authentication method
A security best practice is to combine multiple forms of user authentication into a multifactor authentication (MFA) protocol. And there's a reason it's not called multi-method authentication. The goal of MFA is to pull from two or more factors so a threat actor can't gain access using a single attack vector.
Which is the safest authentication mode
Wi-Fi Protected Access II (WPA2) — introduced in 2004 — remains the most popular wireless security protocol. It uses the Counter Mode Cipher Block Chaining Message Authentication Code Protocol (CCMP) based on the Advanced Encryption Standard (AES) encryption algorithm for stronger security measures.
Why is two-factor authentication bad
The problem with 2FA isn't 2FA itself. It's how it's deployed. If an attacker can break any link in the 2FA chain, he can break into your systems. Some of the methods recently used to crack 2FA are good old phishing and social engineering.
Why is two-factor authentication not safe
2FA can be vulnerable to several attacks from hackers because a user can accidentally approve access to a request issued by a hacker without acknowledging it. This is because the user may not receive push notifications by the app notifying them of what is being approved.
Is two-factor authentication 100% safe
Using two-factor authentication is like using two locks on your door — and is much more secure. Even if a hacker knows your username and password, they can't log in to your account without the second credential or authentication factor.
Why is 2 step verification bad
Sometimes passwords are too easy to reset. Identity thieves can gather enough information about an account to call up customer service or find other ways to request a new password. This often circumvents any two-factor authentication involved and, when it works, it allows thieves direct access to the account.
Can hackers disable two-factor authentication
Another social engineering technique that is becoming popular is known as “consent phishing”. This is where hackers present what looks like a legitimate OAuth login page to the user. The hacker will request the level of access they need, and if access is granted, they can bypass MFA verification.
Can hackers turn off two-factor authentication
Some platforms enable users to generate tokens in advance, sometimes providing a document with a certain number of codes that can be used in the future to bypass 2FA should the service fail. If an attacker obtains the user password and gains access to that document, they can bypass 2FA.
Has LifeLock ever been hacked
NortonLifeLock confirmed that its systems remain secure and have not been hacked, but customer accounts had been subjected to unauthorized access. NortonLifeLock said the compromised accounts contained information such as first names, last names, phone numbers, and mailing addresses.
Will LifeLock stop identity theft
Yes, LifeLock protects your Social Security number and other sensitive data. To do so, it monitors your social media accounts, the websites you visit, your financial accounts, and other places that have your personal information for indications that your identity may have been stolen.
Which type of authentication mode is not recommended
If non-authentication is used, any user can be successfully authenticated without the need of entering the user name and password. Therefore, you are not advised to use non-authentication for device or network security purposes.
Which authentication factor is strongest
The Inherence Factor is often said to be the strongest of all authentication factors. The Inherence Factor asks the user to confirm their identity by presenting evidence inherent to their unique features.
Which two-factor authentication is best
Our pick. Duo Mobile. The best two-factor authentication app.Runner-up. Authy. Easy to use, but requires more personal information.Also great. Google Authenticator. For those who want to avoid cloud backups.
Can hackers get past 2 factor authentication
Tech-savvy attackers can even bypass two-factor authentication without knowing the victim's login credentials. Man-in-the-middle (MiTM) attacks describe the phenomenon of a third party, also known as a man-in-the-middle, intercepting the communication between two systems.
Can your account be hacked after two-factor authentication
The best way to protect yourself from hackers is to develop a healthy amount of scepticism. If you carefully check websites and links before clicking through and also use 2FA, the chances of being hacked become vanishingly small. The bottom line is that 2FA is effective at keeping your accounts safe.