Does encryption stop ransomware?
Yes. Strong encryption is enough to protect against ransomware. However, encryption does not inherently protect data availability. If an encryption key or data set is lost, corrupted, or deleted, the data is lost.
Are encrypted files safe from ransomware?
No. Ransomware can infect encrypted files by adding a layer of encryption on top of the existing protection. Common types of ransomware include Crypto-ransomware, which encrypts valuable files to prevent access.
What prevents ransomware attacks?
- Identify assets that are searchable via online tools and take steps to reduce exposure.
- Protect against ransomware using various techniques.
- Understand patches and regularly update software.
- Exercise caution when opening email attachments.
- Follow SMB security best practices.
- Ensure website security.
- Address the rising threat of ransomware to operational technology assets.
Does encryption prevent viruses?
No. Encrypted viruses use encryption methods to evade antivirus scanners. However, all encrypted files require decryption, allowing anti-malware integrated with decryption to detect viruses.
Can a hacker break encryption?
Yes. Hackers can break encryption using various methods. The most common method is stealing the encryption key. Intercepting data before encryption or after decryption is another way hackers exploit encryption.
Can hackers see encrypted data?
No. Encrypted data is scrambled and unreadable until the encryption key is used for decryption. However, if hackers obtain the encryption key or crack the encryption algorithm, they can gain access to the data.
Can a hacker break into an encrypted file?
No, hackers cannot directly access encrypted files without the encryption key or passphrase to decrypt them. If they manage to obtain the key or crack the algorithm, they can access the data.
Additional Questions:
- How can I protect my files from ransomware? Regularly backup your important files, keep your software and operating system up to date, and practice safe browsing habits.
- What are some common signs of a ransomware infection? Encrypted file extensions, ransom notes on your computer, and the inability to access your files.
- Are there any preventive measures to avoid falling victim to ransomware? Yes, such as using up-to-date anti-malware software, being cautious with email attachments, and regularly patching and updating your software.
- What should I do if I become a victim of a ransomware attack? Disconnect from the network, notify your IT department or a cybersecurity professional, and report the incident to law enforcement.
- Do I have to pay the ransom if I get infected with ransomware? It is generally advised not to pay the ransom, as there is no guarantee that your files will be decrypted, and it encourages further attacks.
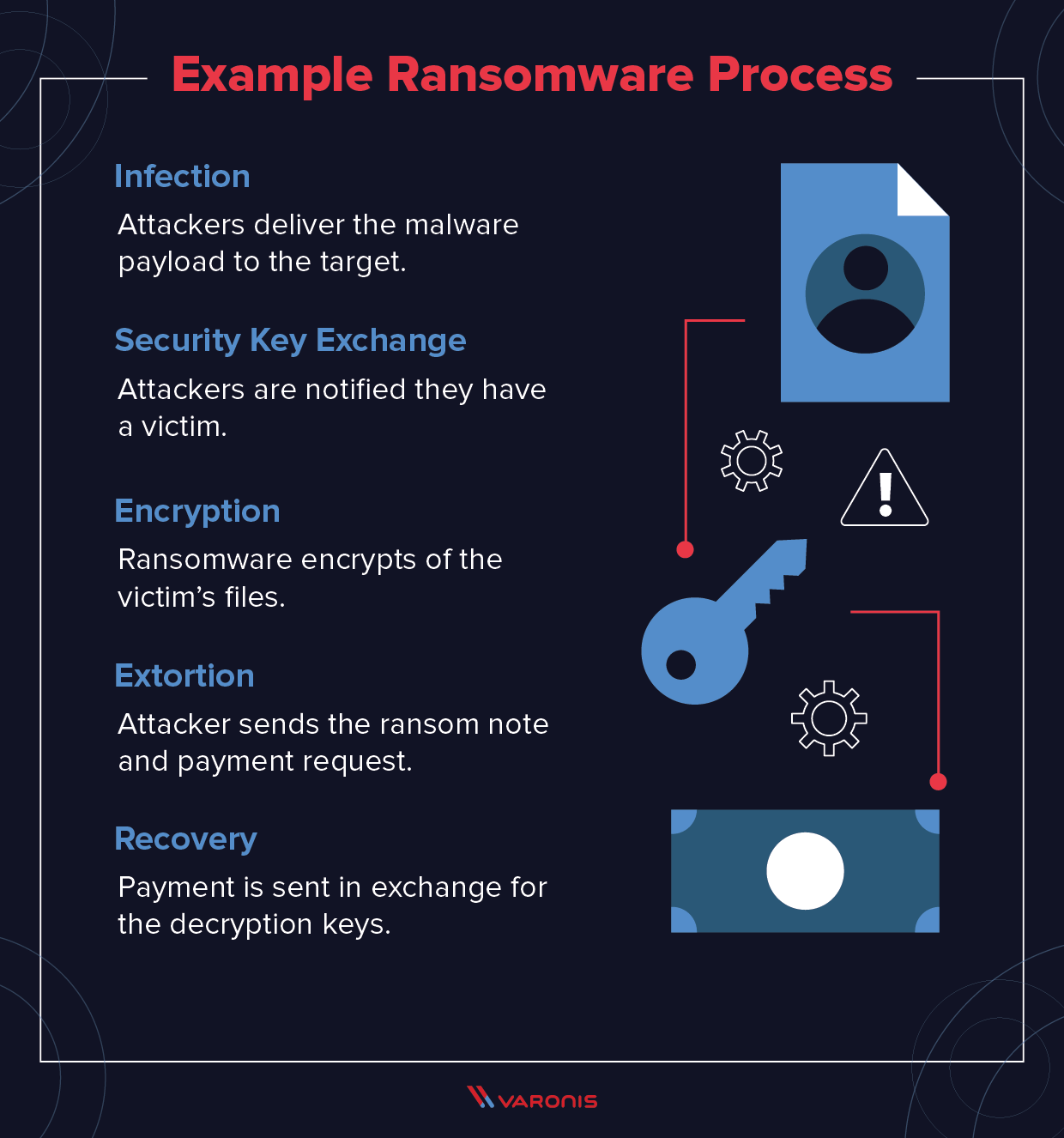
Does encryption stop ransomware
Strong encryption is enough to protect against ransomware.
It's likewise important to remember that encryption wasn't designed to reconstruct data and it does not inherently protect data availability. When an encryption key or data set is lost, corrupted or deleted, that data is lost.
Are encrypted files safe from ransomware
In a word, no. Ransomware can infect even encrypted files by adding a layer of encryption on top of the existing protection. There are a few common kinds of ransomware: Crypto-ransomware, which encrypts valuable files to prevent the owner from accessing them.
Cached
What prevents ransomware attacks
TipsIdentify assets that are searchable via online tools and take steps to reduce that exposure.Protecting Against Ransomware.Understanding Patches and Software Updates.Using Caution with Email Attachments.SMB Security Best Practices.Website Security.Rising Ransomware Threat to Operational Technology Assets.
Does encryption prevent viruses
Encrypted viruses use encryption methods to hide them from malware (antivirus) scanners. Shuffle the code to prevent detection. However, all encrypted files in your computer system require decryption, so you can use anti-malware integrated with decryption to detect viruses.
Can a hacker break encryption
Hackers can break encryption to access the data using a number of different methods. The most common method is stealing the encryption key itself. Another common way is intercepting the data either before it has been encrypted by the sender or after it has been decrypted by the recipient.
Can hackers get through encryption
Can hackers see encrypted data No, hackers cannot see encrypted data, as it is scrambled and unreadable until the encryption key (or passphrase) is used to decrypt it. However, if a hacker manages to obtain the encryption key or crack the encryption algorithm, then they can gain access to the data.
Can a hacker break into an encrypted file
Can hackers see encrypted data No, hackers cannot see encrypted data, as it is scrambled and unreadable until the encryption key (or passphrase) is used to decrypt it. However, if a hacker manages to obtain the encryption key or crack the encryption algorithm, then they can gain access to the data.
Does ransomware steal data or just lock it
Ransomware has been one of the most popular and successful malware types these days. With it, cybercriminals can successfully block access to your own data and devices, steal sensitive information, and earn a fortune by forcing you to pay a ransom.
What are the top 3 causes of successful ransomware attacks
Ransomware attack vectors and mitigations
The top three ways ransomware gets onto victims' systems are phishing, Remote Desktop Protocol (RDP) and credential abuse, and vulnerabilities.
How is ransomware prevented or removed
User education is essential for preventing ransomware infection. Training sessions should be conducted periodically to ensure users are aware of important security measures, including: Avoid clicking on links from unknown or untrusted sources—including websites and emails.
What is the downside of using encryption
One of the significant disadvantages of encryption is key management. Key management should be done efficiently as Encryption and decryption keys cannot be compromised, which might invalidate the data security measures taken.
Is encryption 100 percent safe
Encryption only protects whatever is encrypted, such as your internet connection, email, or files, but it does nothing to prevent you from other online threats.
What is the hardest encryption to crack
AES 256-bit encryption is the strongest and most robust encryption standard that is commercially available today. While it is theoretically true that AES 256-bit encryption is harder to crack than AES 128-bit encryption, AES 128-bit encryption has never been cracked.
When should you not use encryption
Top 4 Reasons Encryption Is Not UsedLack of executive support. This has been a problem since organizations started using encryption.Lack of resources/funding. Encryption costs money.Lack of understanding of what is required.Increasing technology complexity, BYOD and mobility.
Does wiping a computer remove ransomware
The surest way to confirm malware or ransomware has been removed from a system is by doing a complete wipe of all storage devices and reinstall everything from scratch. Formatting the hard disks in your system will ensure that no remnants of the malware remain.
Is it possible to decrypt ransomware files
There are currently many free ransomware decryption tools available for some of the most common types of ransomware. Below are the top 10 free decryptor tools to help you recover files encrypted following a ransomware attack.
What is the #1 cause of ransomware
Infection Vectors
The majority of ransomware is propagated through user-initiated actions such as clicking on a malicious link in a spam e-mail or visiting a malicious or compromised website.
What is the most common method to infect your computer with ransomware
Ransomware is often spread through phishing emails that contain malicious attachments or through drive-by downloading. Drive-by downloading occurs when a user unknowingly visits an infected website and then malware is downloaded and installed without the user's knowledge.
Why can’t ransomware be stopped
Today's ransomware and malware are sophisticated, using random extensions and file names, which makes detection by signature-based (blocked list) solutions ineffective. Cloud Secure uses advanced machine learning algorithms to uncover unusual data activity and detect a potential attack.
Why Let’s encrypt is a really really really bad idea
Let's Encrypt is an example where the “convenience” of automated issuance of “free” SSL certificates is a bug, not a feature. The more sites secured by Let's Encrypt certificates, the bigger the threat surface becomes because the compromise of Let's Encrypt's KMS could potentially affect a large number of sites.
What is more secure than encryption
Hashing and encryption both provide ways to keep sensitive data safe. However, in almost all circumstances, passwords should be hashed, NOT encrypted. Hashing is a one-way function (i.e., it is impossible to "decrypt" a hash and obtain the original plaintext value).
Which encryption is hardest to crack
AES 256-bit encryption is the strongest and most robust encryption standard that is commercially available today. While it is theoretically true that AES 256-bit encryption is harder to crack than AES 128-bit encryption, AES 128-bit encryption has never been cracked.
Can hackers crack encryption
Hackers can break encryption to access the data using a number of different methods. The most common method is stealing the encryption key itself. Another common way is intercepting the data either before it has been encrypted by the sender or after it has been decrypted by the recipient.
Who can crack 256-bit encryption
256-bit encryption is refers to the length of the encryption key used to encrypt a data stream or file. A hacker or cracker will require 2256 different combinations to break a 256-bit encrypted message, which is virtually impossible to be broken by even the fastest computers.
How long would it take to crack 256 encryption
AES-256 encryption is virtually uncrackable using any brute-force method. It would take millions of years to break it using the current computing technology and capabilities. However, no encryption standard or system is completely secure.