tect and analyze suspicious activity on endpoints and provide remediation actions to mitigate the impact of security incidents. Unlike traditional antivirus solutions, EDR focuses on detecting and responding to advanced threats and targeted attacks.
How does EDR work EDR works by continuously monitoring endpoint devices, such as desktops, laptops, and servers, for any suspicious activity or signs of compromise. It collects and analyzes data from various sources, including system logs, network traffic, and user behavior, to detect potential threats. EDR solutions use advanced algorithms and machine learning techniques to identify patterns and anomalies that may indicate malicious activity. When a threat is detected, EDR tools can initiate automated response actions or provide alerts to IT security teams for further investigation and remediation.
What are the key features of EDR EDR solutions typically offer the following key features:1. Real-time monitoring and visibility: EDR provides real-time visibility into endpoint activities, enabling organizations to quickly identify and respond to potential threats.
2. Threat detection and response: EDR tools use advanced detection techniques to identify both known and unknown threats. They also offer response capabilities to contain and remediate security incidents.
3. Incident investigation and forensics: EDR captures detailed information about security incidents, allowing organizations to conduct thorough investigations, identify the root cause, and take appropriate actions to prevent future attacks.
4. Behavioral analysis: EDR solutions analyze user and endpoint behavior to detect and block suspicious activities that may indicate an ongoing attack or compromise.
5. File integrity monitoring: EDR monitors critical files and system configurations for unauthorized changes, ensuring the integrity and security of endpoint systems.
6. Endpoint isolation and quarantine: EDR can isolate compromised endpoints from the network and prevent further spread of malware or lateral movement by containing the affected system.
7. Threat intelligence integration: EDR solutions leverage threat intelligence feeds and integrate with external security tools to enhance their detection capabilities.
8. Automated response and remediation: EDR tools can automate response actions, such as quarantining or mitigating threats, to reduce the response time and minimize the impact of security incidents.
9. Compliance and reporting: EDR provides compliance monitoring and reporting features, helping organizations demonstrate adherence to security regulations and standards.
10. Integration with other security solutions: EDR solutions can integrate with other security products, such as SIEM (Security Information and Event Management) systems, to provide a holistic view of the security landscape and improve overall threat detection and response capabilities.
Is EDR only for large enterprises EDR solutions are not limited to large enterprises. They are suitable for organizations of all sizes, from small businesses to multinational corporations. The level of adoption may vary based on the organization’s security requirements, budget, and the complexity of their IT infrastructure. However, EDR can provide significant benefits for any organization looking to enhance their endpoint security and improve their ability to detect and respond to cyber threats. Can EDR detect zero-day attacks Yes, EDR solutions are designed to detect and respond to zero-day attacks. Unlike traditional signature-based antivirus solutions, EDR leverages behavior-based detection techniques, machine learning algorithms, and advanced analytics to identify previously unknown or zero-day threats. By monitoring endpoint activity and analyzing patterns, EDR can detect suspicious behaviors that may indicate the presence of a zero-day exploit or an unknown malware variant. Can EDR prevent ransomware attacks EDR solutions can help prevent and mitigate the impact of ransomware attacks. By continuously monitoring endpoint activities and detecting unusual file access or encryption behaviors, EDR can identify ransomware activity in real-time. EDR tools can also trigger automated response actions, such as isolating the affected endpoint, blocking network communication with the command and control servers, and rolling back malicious changes. Additionally, EDR can provide valuable insights during incident response and help organizations recover from ransomware attacks more effectively. How does EDR differ from SIEM EDR focuses on endpoint security and provides real-time visibility, detection, and response capabilities specifically for endpoints. SIEM, on the other hand, is a broader security solution that collects and analyzes security event data from various sources, including endpoints, network devices, and application logs. SIEM correlates and analyzes this data to identify security incidents and provide centralized monitoring and reporting. While SIEM can detect network-level threats and analyze broader security events, EDR is more specialized in monitoring and protecting endpoints. Can EDR be used alongside antivirus software Yes, EDR can be used in conjunction with traditional antivirus software. While antivirus software is primarily focused on signature-based detection of known threats, EDR provides additional capabilities for detecting and responding to advanced and unknown threats. By using both antivirus and EDR solutions together, organizations can improve their overall security posture and enhance their ability to detect and mitigate a wide range of threats. Is EDR a stand-alone solution EDR can be deployed as a stand-alone solution or as part of a broader cybersecurity platform. Many EDR solutions are also integrated into Endpoint Protection Platforms (EPP) or bundled with other security tools, such as firewall and intrusion prevention systems. The choice of deployment depends on the organization’s specific security requirements and existing infrastructure. However, it’s important to note that while EDR can provide advanced endpoint security capabilities, it is not a replacement for a comprehensive cybersecurity strategy that includes multiple layers of defense. What are some popular EDR solutions Some popular EDR solutions in the market include:1. CrowdStrike Falcon Endpoint Protection
2. Carbon Black Response
3. FireEye Endpoint Security
4. Symantec Endpoint Detection and Response
5. Microsoft Defender for Endpoint
6. Trend Micro Apex One
7. Palo Alto Networks Cortex XDR
8. SentinelOne Endpoint Protection
9. McAfee MVISION EDR
10. Cynet 360
These solutions offer a range of features and capabilities to help organizations detect, respond to, and prevent advanced threats and security incidents on their endpoints.
Are there any limitations of EDR Like any security solution, EDR has its limitations. Some potential limitations of EDR include:1. False positives: EDR solutions may generate false positive alerts, where legitimate activities are flagged as suspicious or malicious. This can result in unnecessary investigation and disruption of normal business operations.
2. Endpoint performance impact: EDR solutions may consume system resources and impact the performance of endpoint devices, particularly during intensive scanning and analysis processes.
3. Complexity and learning curve: EDR solutions typically require specialized knowledge and expertise to configure, operate, and tune effectively. Organizations may need to invest in training or rely on external expertise to maximize the value of their EDR deployment.
4. Privacy considerations: EDR solutions collect and analyze large amounts of data from endpoints, including user activities and behaviors. Organizations need to ensure they have proper policies and protocols in place to protect the privacy and confidentiality of this data.
5. Response time and effectiveness: EDR’s ability to detect and respond to threats relies on the speed and accuracy of its detection algorithms and the effectiveness of its response actions. There is always a risk of false negatives, where threats go undetected, or delays in response actions, which may allow an attacker to cause damage.
Overall, while EDR can greatly enhance an organization’s endpoint security capabilities, it is important to understand its limitations and consider them in the context of the organization’s specific security requirements and risk tolerance.
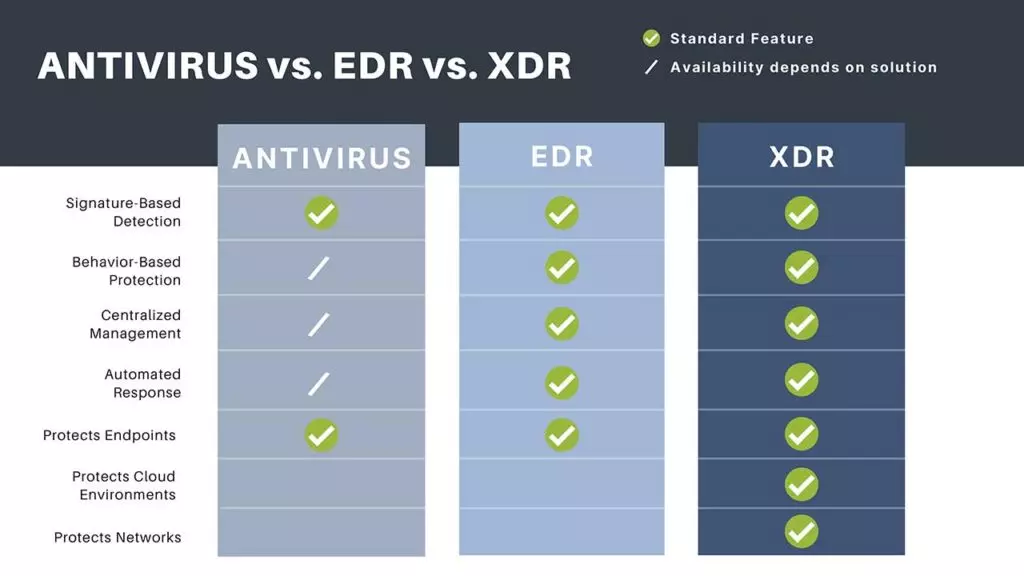
Is antivirus part of EDR
Does EDR Include Antivirus Yes, EDR solutions may include antivirus. In other cases, EDR is sold as a component of an Endpoint Protection Platform (EPP); the EPP solution typically provides antivirus protection and other security measures.
Cached
How is EDR better than antivirus
EDR solutions are better at detecting both known and unknown threats than antivirus solutions, as they don't rely on signatures . Additionally, EDR provides visibility into the activities of users, processes, applications, files, networks, and devices .
Cached
What is the disadvantage of EDR
The greatest drawback of EDR is that it is a reactive approach. Traditional EDR tools rely on behavioral analysis which means the threat has executed on the endpoint and it's a race against time to stop it before any damage is done.
Does EDR detect malware
Endpoint Detection and Response (EDR), also referred to as endpoint detection and threat response (EDTR), is an endpoint security solution that continuously monitors end-user devices to detect and respond to cyber threats like ransomware and malware.
Cached
Is Microsoft Defender Antivirus or EDR
Not only is Microsoft Defender Antivirus an excellent next-generation antivirus solution, but combined with other Defender for Endpoint capabilities, such as endpoint detection and response and automated investigation and remediation, you get better protection that's coordinated across products and services.
Does EDR include firewall
No, EDR is not a Firewall. It's an advanced-level security tool with firewall capabilities, but it performs many other functions to secure your organization against known and unknown malware attacks.
Can EDR replace antivirus
Can EDR replace antivirus, or are both needed You can use EDR solutions to track, monitor, and analyze data on endpoints to enhance the fortification of your environment. Generally, EDR tools do not replace traditional tools like antivirus and firewalls; they work beside them to provide enhanced security capabilities.
What is EDR instead of antivirus
EDR stands for Endpoint Detection and Remediation in IT security. It is a type of security software that monitors and responds to threats on computer networks. EDR tools can detect malicious activity, such as malware infections or unusual user behavior, and take action to contain or remove the threat.
Is Microsoft Defender enough as antivirus
Is Windows Defender good enough Yes, Windows Defender is a good basic virus protection software. You may not find everything you want if you are extremely security focused. A third-party antivirus or anti-malware software will likely find threats that Windows Defender may miss.
Is EDR better than firewall
A Firewall blocks unwanted traffic and won't let unauthorized users access your network. EDR monitor traffic across all endpoints with the sole purpose of identifying and preventing potential threats. EDR is better than a firewall because it detects malicious activity before it causes any damage.
How long does EDR data last
15 to 120 seconds
Some new cars don't even include an EDR. But an EDR will typically record data for 15 to 120 seconds, consistently overwriting that data with fresh data as you generate it. Most EDRs only record when an accident is detected.
Can I remove EDR from my car
EDRs are integral parts of the airbag control system, so the EDR cannot safely be removed from cars that have them.
What are the disadvantages of Windows Defender
Cons of Windows DefenderLacks integrated dashboard for all devices using Windows Defender.No accountability if the computer is infected by malware.Limited features for large scale use.Slows down installation of frequently-used applications.
Should I turn off Windows Defender if I have antivirus
But don't disable Defender unless you have another antivirus program ready to be installed. That's because without active anti-virus protection, you're exposed to a massive security risk. It's also not advisable to run multiple antivirus programs at the same time.
Does EDR prevent ransomware
Leveraging a powerful endpoint detection and response (EDR) solution like IBM Security QRadar EDR can help detect and remediate advanced ransomware threats in seconds. Unlike antiviruses, EDR solutions don't rely on known signatures and can detect unknown or fileless threats.
Does insurance look at EDR
Most insurance companies will act fast to get their hands on the EDR data of your car and that of the other vehicle/vehicles involved in the crash.
What are the problems with EDR data
Potential Problems with EDR Data
The EDR data contradicts physical evidence. The data is out of the common driving range (low or high) There is a discontinuity in the data (flat lines, spikes, etc.) Events such as multiple impacts, spins, airborne, rollover, or narrow object collisions.
Do I need antivirus or is Windows Defender enough
Is Windows Defender good enough Yes, Windows Defender is a good basic virus protection software. You may not find everything you want if you are extremely security focused. A third-party antivirus or anti-malware software will likely find threats that Windows Defender may miss.
Is Windows Defender good enough for virus protection
Is Microsoft Defender any good Microsoft Defender is a good enough option for basic antivirus protection. It has a very strong firewall and a good number of features for the program and device security. However, the scanning performance is very poor, and secure browsing is only possible with Microsoft Edge.
Can EDR data be erased
In terms of storage length, EDR event data will typically never be erased or lost unless the vehicle is involved in another collision (in which case the data will be overwritten). However, some older generation vehicles (i.e. Toyotas, GMs, and Fords) may overwrite data during routine driving operations.
How long does data last on EDR
Most EDRs store crash data for 200 ignition cycles, which typically means only six to eight weeks after an accident. If a vehicle is repaired after a crash, the EDR may be replaced or lost. Therefore, the sooner you contact an accident lawyer, the better the chances that EDR information can help your claim.
Is Microsoft Defender good enough for virus protection
Microsoft Defender is a good enough option for basic antivirus protection. It has a very strong firewall and a good number of features for the program and device security. However, the scanning performance is very poor, and secure browsing is only possible with Microsoft Edge.
