al coffee shop. It all depends on how it is used and the intentions of the user.
Cached[/wpremark]
How does Wireshark work Wireshark captures network packets and analyzes them in real time. It displays detailed information about each packet, including the source and destination IP addresses, the protocol used, and the contents of the packet. This information can be used to troubleshoot network issues, analyze network traffic, or detect malicious activity.
Cached
What are some practical uses of Wireshark Wireshark can be used to troubleshoot network problems, such as slow network performance or intermittent connectivity issues. It can also be used to analyze network traffic for security purposes, such as detecting and preventing malware infections or identifying network attacks. Additionally, Wireshark can be used to study network protocols and gain a deeper understanding of how data is transmitted over a network.
Cached
Can Wireshark capture encrypted traffic Wireshark can capture encrypted traffic, but it cannot decrypt the contents of the packets without the encryption keys. However, it can still provide valuable information about the encrypted traffic, such as the source and destination IP addresses, the protocol used, and the size of the packets. This can be useful for analyzing patterns and detecting potential security threats.
Cached
How to filter network traffic in Wireshark Wireshark provides various filtering options to help you focus on specific network traffic. You can filter by IP address, port number, protocol, or even specific keywords in the packet contents. This allows you to narrow down the captured packets and focus on the ones that are relevant to your analysis or troubleshooting.
Cached
What are some alternatives to Wireshark There are several alternatives to Wireshark, such as tcpdump, Microsoft Network Monitor, and Capsa. These tools provide similar packet capturing and analysis capabilities, but each has its own unique features and user interface. It’s worth exploring different options to find the one that best suits your needs and preferences.
Cached
How to analyze HTTP traffic in Wireshark Wireshark can capture and analyze HTTP traffic by filtering for packets with the HTTP protocol. Once the HTTP packets are captured, Wireshark provides various tools and options to analyze the HTTP traffic, such as dissecting the headers and contents of the HTTP requests and responses, identifying any errors or abnormalities, and measuring the response times for different HTTP transactions.
Cached
Is Wireshark difficult to use Wireshark can be a complex tool, especially for beginners. However, with some practice and familiarity with networking concepts, it becomes easier to navigate and utilize the various features of Wireshark. The key is to start with basic captures and gradually explore more advanced features as you gain experience.
Cached
How to analyze DNS traffic in Wireshark Wireshark can capture and analyze DNS (Domain Name System) traffic by filtering for packets with the DNS protocol. Once the DNS packets are captured, Wireshark provides tools to dissect and analyze the DNS traffic, such as identifying DNS queries and responses, tracking DNS resolutions, and detecting any DNS-related issues or abnormalities.
Cached
Can Wireshark be used for performance testing Yes, Wireshark can be used for performance testing by capturing and analyzing network traffic. It allows you to identify any bottlenecks or latency issues, measure response times, and monitor network behavior under different conditions. This can be helpful in optimizing network performance and troubleshooting any performance-related problems.
Cached
How to analyze SSL/TLS traffic in Wireshark Wireshark can capture and analyze SSL/TLS (Secure Sockets Layer/Transport Layer Security) traffic by filtering for packets with the SSL/TLS protocol. Once the SSL/TLS packets are captured, Wireshark provides options to decrypt and analyze the encrypted traffic if you have the appropriate SSL/TLS keys. This allows you to inspect the encrypted contents of the SSL/TLS traffic and troubleshoot any security-related issues.
Cached
How does Wireshark help with network troubleshooting Wireshark helps with network troubleshooting by capturing and analyzing network packets. It allows you to identify any network errors or anomalies, track the flow of packets, determine the source and destination of network traffic, and diagnose network performance issues. By examining the details of the captured packets, you can pinpoint the root cause of network problems and implement appropriate solutions.
Cached
How to analyze VoIP traffic in Wireshark Wireshark can capture and analyze VoIP (Voice over Internet Protocol) traffic by filtering for packets with the appropriate VoIP protocols, such as SIP (Session Initiation Protocol) or RTP (Real-time Transport Protocol). Once the VoIP packets are captured, Wireshark provides tools to dissect and analyze the VoIP traffic, such as identifying the participants in a VoIP call, analyzing call quality metrics, and detecting any VoIP-related issues or abnormalities.
Cached
Can Wireshark be used for network forensics Yes, Wireshark can be used for network forensics. It allows you to capture and analyze network traffic, which can provide valuable evidence in investigating and reconstructing network security incidents or breaches. Wireshark’s detailed packet information and analysis capabilities can help in identifying malicious activity, unauthorized access, or any other suspicious behavior on a network.
Cached
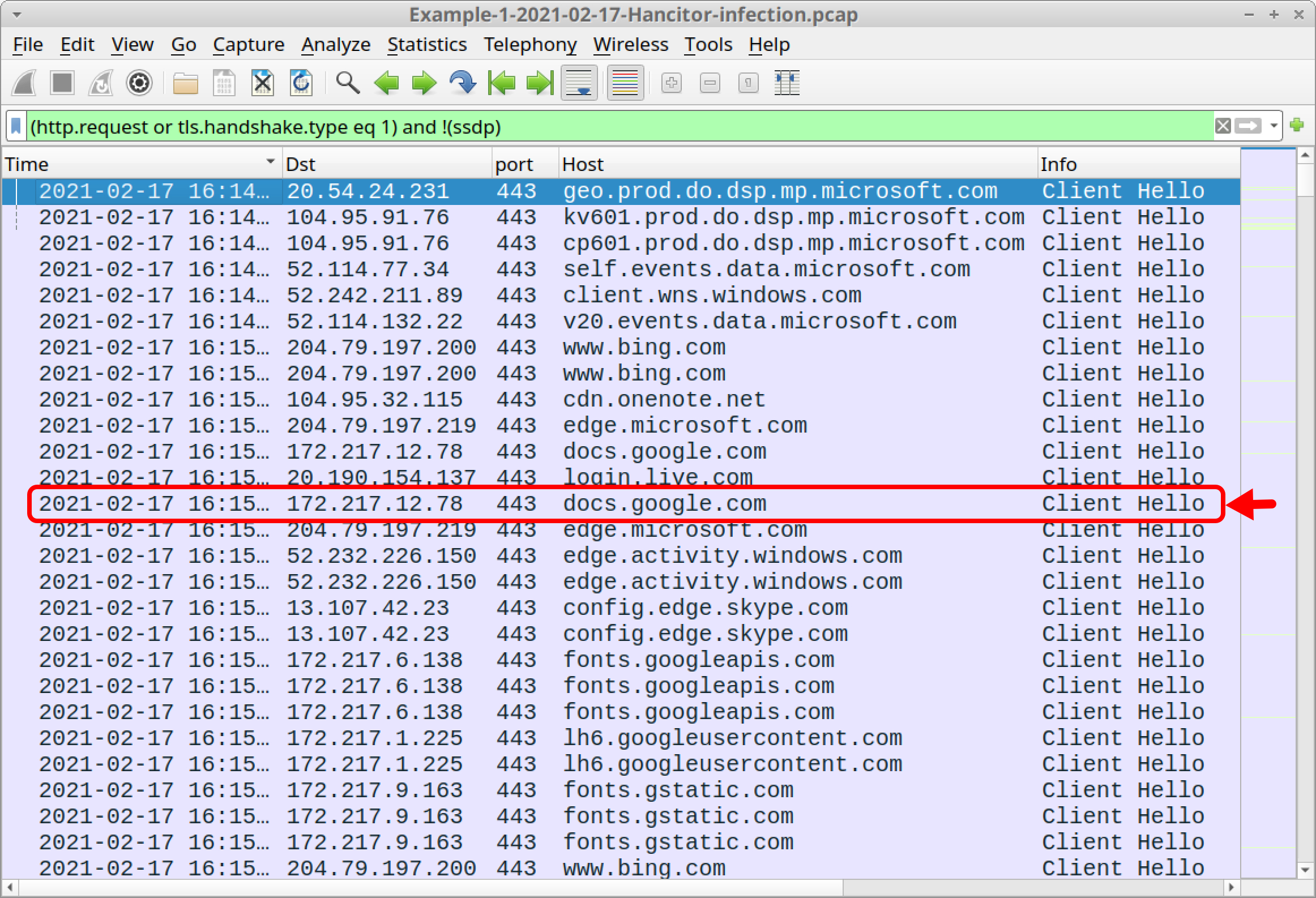
What can Wireshark detect
Wireshark has many uses, including troubleshooting networks that have performance issues. Cybersecurity professionals often use Wireshark to trace connections, view the contents of suspect network transactions and identify bursts of network traffic.
Cached
How does Wireshark detect malicious traffic
Wireshark proves to be an effective open source tool in the study of network packets and their behavior. In this regard, Wireshark can be used in identifying and categorizing various types of attack signatures. It lets administrator to see what"s happening on network at a microscopic level.
Does Wireshark capture everything
By default, Wireshark only captures packets going to and from the computer where it runs. By checking the box to run Wireshark in promiscuous mode in the capture settings, you can capture most of the traffic on the LAN.
Cached
What are the limitations of Wireshark
It cannot run from outside a network. Wireshark doesn't facilitate packet injection; it doesn't capture a passing packet stream and enables new packets to be substituted for those already passing by.
Is it illegal to use Wireshark
Just like anything, it is legal if you use it in accordance to the law. Shaving razors are legal, what becomes illegal is when you threaten or use it as a weapon. Wireshark is legal, it becomes illegal when you monitor a network that you don't have authorization to monitor.
Can Wireshark be used for spying
If you're on the same Wi-Fi network, it's as simple as opening Wireshark and configuring a few settings. We'll use the tool to decrypt WPA2 network traffic so we can spy on which applications a phone is running in real time.
How to detect malware with network traffic
One way to identify malware is by analyzing the communication that the malware performs on the network. Using machine learning, these traffic patterns can be utilized to identify malicious software.
Can Wireshark be used to steal
It can be used to analyze internal networks and network usage, debug application issues, and study protocols in action. But it can also be used to sniff passwords, reverse-engineer network protocols, steal sensitive information, and listen in on the online chatter at your local coffee shop.
What can hackers do with Wireshark
Wireshark can also be used as a tool for hackers. This usually involves reading and writing data transmitted over an unsecure or compromised network. Nefarious actors may seek out confidential data such as credit-card information, passwords, search queries, private messages, emails, financial transactions, and more.
Is IP sniffing illegal
Whether IP sniffing is legal or not depends on a few circumstances. There are about as many, very, different laws as there are legislators. In the US several Federal laws prohibit or restrict network monitoring and the sharing of records of network activity. These laws were drawn up to protect online privacy.
Can Wireshark detect keylogger
Wireshark can only act as a keylogger, in the sense of a program that monitors keystrokes, if the keyboard being used is a hardware keyboard that connects to a host over a network that Wireshark can sniff. If the keyboard you're trying to monitor is a software keyboard on a smartphone or tablet, that won't work.
How do you check if my computer is infected with malware
Open your Windows Security settings. Select Virus & threat protection > Scan options. Select Windows Defender Offline scan, and then select Scan now.
Which tool device can detect the presence of malware in a network device
Antivirus and antimalware software may be installed on a device to detect and remove malware. These tools can provide real-time protection or detect and remove malware by executing routine system scans.
Can Wireshark get your IP
Wireshark is a powerful tool that can analyze traffic between hosts on your network. But it can also be used to help you discover and monitor unknown hosts, pull their IP addresses, and even learn a little about the device itself.
Do hackers use Wireshark
Wireshark can also be used as a tool for hackers. This usually involves reading and writing data transmitted over an unsecure or compromised network. Nefarious actors may seek out confidential data such as credit-card information, passwords, search queries, private messages, emails, financial transactions, and more.
Is IP grabbing illegal in the US
Is tracing an IP address legal Yes, tracing your IP address is legal as long as it's not used for criminal activities. The websites you visit, the apps you use, and even your ISP collect your IP address along with other personal information. However, individual users can also easily trace your IP address.
Can Wireshark show incognito searches
Can Wireshark see incognito Yes. Incognito mode doesn't do anything to hide or encrypt network traffic, it only stops your browser from storing your browsing history for that session. This means that there will be network logs of your browsing and Wireshark will be able to see the connections.
What are 3 signs you might have malware on your computer
How To Know if You Have Malwaresuddenly slows down, crashes, or displays repeated error messages.won't shut down or restart.won't let you remove software.serves up lots of pop-ups, inappropriate ads, or ads that interfere with page content.shows ads in places you typically wouldn't see them, like government websites.
How do I completely check for malware
FAQsClick on Start.Click on Settings.Click on Update & Security.Choose Windows Security.Click on Virus & Threat Protection.Choose Current Threats.Click on Scan Options/Threat History.Run a new Advanced Scan.
How do you detect the presence of malware
To detect a certain malware instance, anti-virus software simply checks for the presence of its signature in a given program (scanning). Commercial anti-virus products maintain large databases of these signatures, and scan every file for all signatures of viruses and worms they know of.
How can I check my device for malware
Check for Android malware using Play ProtectOpen the Play Store on the Android device you want to scan.Tap on your profile in the upper-right corner.Tap on Play Protect.Tap Scan.Tap on the option to remove any detected malware.
How do hackers track your IP
Hackers can get your IP via email, digital ads, phony links, torrenting sites or your devices, such as routers and computers. You can use a VPN to protect your online activities and prevent hackers from getting your IP address.
Can Wireshark see through VPN
When paired with a VPN, Wireshark can confirm that a connection is encrypted and working as it should. It can also be used to collect traffic from your network and VPN tunnel. Check out our what is Wireshark page for more information about it.
What can I hack with Wireshark
Wireshark can also be used as a tool for hackers. This usually involves reading and writing data transmitted over an unsecure or compromised network. Nefarious actors may seek out confidential data such as credit-card information, passwords, search queries, private messages, emails, financial transactions, and more.
Can the FBI get your IP
So, If you're wondering if the police can track your phone numbers and IP addresses, the answer is – yes, they can. While the police cannot search your phone without a warrant, they have a legal right to watch what you do in public, on social media, and in your home and business.