Can’t firewalls defend against DDoS attacks Firewalls are not designed to handle the volume and complexity of DDoS attacks. They are more focused on filtering traffic based on predefined rules and policies. DDoS attacks overwhelm the network by flooding it with traffic from multiple sources, making it difficult for firewalls to distinguish between legitimate and malicious traffic. Additionally, DDoS attacks often target specific applications or services, bypassing the firewall altogether.
How can a network be protected from DDoS attacks There are several measures that can be implemented to protect a network from DDoS attacks. These include:
1. Traffic analysis and profiling: Monitoring network traffic patterns and identifying anomalous behavior can help detect and mitigate DDoS attacks.
2. Intrusion Detection System/Intrusion Prevention System (IDS/IPS): IDS/IPS can help identify and block DDoS attacks by analyzing network traffic in real-time and applying appropriate countermeasures.
3. Load balancing: Distributing incoming traffic across multiple servers can help mitigate the impact of DDoS attacks by spreading the load.
4. Content Delivery Network (CDN): Using a CDN can help distribute traffic geographically, reducing the impact of DDoS attacks by distributing the load across multiple servers.
5. Rate limiting: Implementing rate limiting on network resources can help mitigate the impact of DDoS attacks by restricting the amount of traffic that can be processed.
6. DDoS mitigation services: Engaging the services of a specialized provider can help detect and mitigate DDoS attacks, as they have the infrastructure and expertise to handle large-scale attacks.
7. Network segmentation: Dividing the network into smaller, isolated segments can limit the scope of a DDoS attack and prevent it from affecting the entire network.
8. Redundancy and failover systems: Implementing redundant systems and failover mechanisms can ensure that the network remains operational even during a DDoS attack.
9. Constant monitoring and incident response: Monitoring network traffic continuously and having a well-defined incident response plan in place can help minimize the impact of DDoS attacks and facilitate a swift recovery.
10. Regular software updates and patches: Keeping software and systems up-to-date with the latest security patches can help reduce the vulnerability to DDoS attacks by fixing known vulnerabilities.
What are some common DDoS attack techniques DDoS attacks can employ various techniques to overwhelm a target’s resources. Some common techniques include:
1. UDP Flood: A large number of User Datagram Protocol (UDP) packets are sent to the target, consuming network bandwidth and overwhelming network devices.
2. SYN Flood: Attackers send a high volume of TCP connection requests (SYN packets) to the target, causing network resources to be tied up in processing these requests and preventing legitimate connections.
3. ICMP Flood: Attackers send a large number of Internet Control Message Protocol (ICMP) packets to the target, consuming network bandwidth and overwhelming network devices.
4. HTTP Flood: Attackers send a large number of HTTP requests to a target’s web server, leading to the consumption of server resources and eventual unavailability of the website.
5. DNS Amplification: Attackers send small DNS queries to open DNS servers, which respond with much larger DNS responses, overwhelming the target’s network.
6. NTP Amplification: Attackers abuse Network Time Protocol (NTP) servers to generate a large volume of traffic towards the target’s network.
7. SSDP/UPnP Reflection: Attackers send Simple Service Discovery Protocol (SSDP) or Universal Plug and Play (UPnP) requests to vulnerable devices, which then respond with larger amounts of data to the target.
8. Slowloris: Attackers establish a large number of low-bandwidth connections to a target web server, exhausting server resources and preventing it from serving legitimate requests.
9. Application-layer attacks: Attackers target vulnerabilities in specific applications or services, such as web servers or databases, causing them to become unresponsive or crash.
10. IoT Botnet attacks: Attackers compromise Internet of Things (IoT) devices and use them to launch coordinated DDoS attacks, leveraging the combined computing power of multiple devices.
Each attack technique requires different mitigation strategies, and a combination of preventative measures is typically employed to defend against various attack vectors.
Can firewalls be bypassed during DDoS attacks Firewalls can be bypassed during DDoS attacks. Attackers can use various techniques to circumvent firewalls, such as using IP spoofing to hide the source of the attack or targeting specific application vulnerabilities that the firewall may not be able to detect. Additionally, some DDoS attacks may overwhelm the firewall itself, rendering it ineffective in defending against the attack.
Can a DDoS attack be traced back to its source Tracing a DDoS attack back to its source can be challenging. Attackers often use techniques to obfuscate their identity and location, such as using botnets or anonymizing services. Furthermore, DDoS attacks may involve traffic coming from multiple sources, making it difficult to pinpoint the exact origin of the attack. However, with the assistance of network monitoring tools, forensic analysis, and cooperation with internet service providers, it is possible to trace the attack back to some extent.
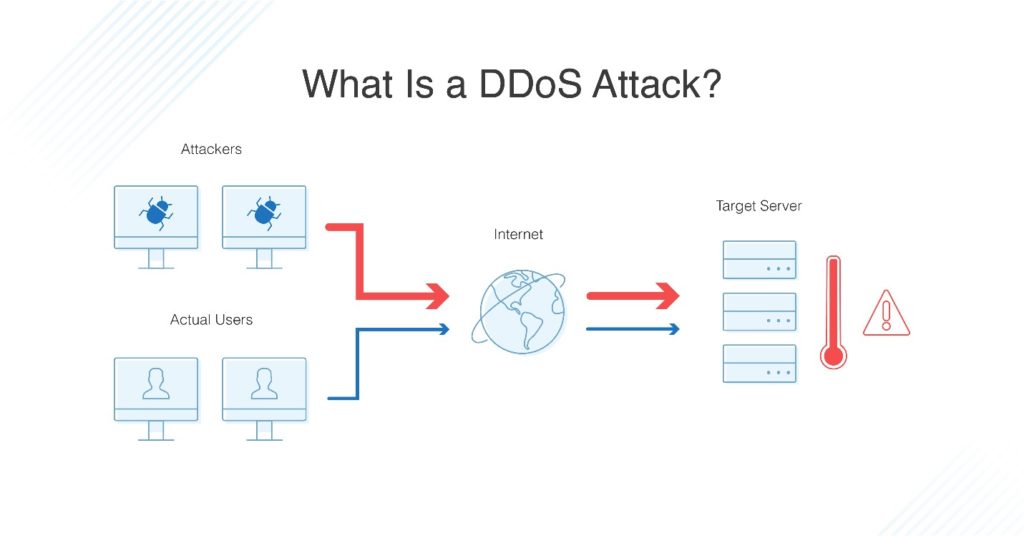
What is the difference between a DoS and a DDoS attack A DoS (Denial of Service) attack is a malicious attempt to disrupt the availability of a system or network by overwhelming it with a flood of traffic or resource requests. It typically involves a single source that can either be a single computer or a network of compromised computers (botnet).
On the other hand, a DDoS (Distributed Denial of Service) attack involves multiple sources flooding the target system or network with traffic or requests. These sources are usually compromised devices that form a botnet under the control of the attacker. DDoS attacks are often more powerful and harder to mitigate than DoS attacks due to the distributed nature of the attack.
What are the motivations behind DDoS attacks DDoS attacks can be motivated by various factors, including:
1. Extortion: Attackers may launch DDoS attacks as a means of extorting money from businesses or individuals, threatening to disrupt their services or websites unless a ransom is paid.
2. Revenge: DDoS attacks can be carried out to seek revenge against an individual or organization, often in response to a perceived wrongdoing or conflict.
3. Competition: In some cases, rival companies or individuals may launch DDoS attacks to gain a competitive advantage, by disrupting the services of their competitors.
4. Hacktivism: DDoS attacks can be a form of protest or activism, used to draw attention to a particular cause or to voice dissent against an organization or government.
5. Distraction: DDoS attacks may be used as a diversionary tactic, diverting the attention of security teams or resources while other malicious activities, such as data breaches, are carried out.
6. Ideology: Some DDoS attacks are motivated by ideological or political beliefs, aiming to disrupt the services of organizations or governments that the attackers perceive as adversaries.
7. Testing: DDoS attacks can also be carried out for testing purposes, to assess the resilience and effectiveness of an organization’s defenses against such attacks.
The motivations behind DDoS attacks can vary greatly depending on the attacker’s goals, and understanding the motivations can help organizations better prepare and defend against such attacks.
How can individuals protect themselves from DDoS attacks While individuals may not be the primary targets of DDoS attacks, they can still take steps to protect themselves, such as:
1. Using a reputable internet security suite: Installing and keeping internet security software up-to-date can help protect against various types of cyber threats, including DDoS attacks.
2. Regularly updating software and devices: Keeping software, firmware, and devices (such as routers) up-to-date with the latest security patches can help minimize vulnerabilities that may be exploited in DDoS attacks.
3. Enabling firewalls and network security features: Activating firewalls and other network security features provided by routers or internet security software can add an extra layer of defense against DDoS attacks.
4. Avoiding suspicious links and downloads: Being cautious about clicking on unknown links or downloading files from untrustworthy sources can help prevent malware infections that can contribute to DDoS attacks.
5. Using strong and unique passwords: Employing strong, unique passwords for online accounts can help prevent unauthorized access and reduce the risk of attackers using compromised credentials in DDoS attacks.
6. Being vigilant about phishing attacks: Staying alert to phishing attempts and avoiding sharing personal information or login credentials with suspicious or unsolicited requests can help prevent account compromises that may lead to DDoS attacks.
While individuals may not have the same resources as organizations to defend against DDoS attacks, these measures can provide a basic level of protection and reduce the risk of falling victim to such attacks.
How can organizations prepare for potential DDoS attacks Organizations can take several steps to prepare for potential DDoS attacks, including:
1. Conducting a risk assessment: Evaluating the organization’s infrastructure, networks, and systems to identify vulnerabilities and potential entry points for DDoS attacks.
2. Developing an incident response plan: Creating a comprehensive plan that outlines the steps to be taken in the event of a DDoS attack, including communication protocols, roles and responsibilities, and technical mitigation strategies.
3. Implementing DDoS mitigation solutions: Deploying dedicated DDoS mitigation solutions, such as hardware appliances or cloud-based services, can help detect and mitigate attacks in real-time.
4. Testing networks and systems: Regularly testing the organization’s networks and systems for vulnerabilities and ensuring that all security measures are functioning as intended.
5. Engaging with DDoS mitigation providers: Establishing relationships with DDoS mitigation providers can help organizations quickly activate specialized services in the event of an attack, ensuring timely response and mitigation.
6. Ensuring redundancy and scalability: Building redundancy and scalability into the organization’s infrastructure and networks can help absorb the impact of DDoS attacks and ensure the continuity of critical services.
7. Educating employees: Providing ongoing training and education to employees about DDoS attacks, their impact, and steps to take in the event of an attack can help create a culture of security and preparedness.
8. Monitoring network traffic and behavior: Implementing network monitoring tools and solutions can help detect early signs of a DDoS attack, allowing for a faster response and mitigation.
By taking these proactive measures, organizations can strengthen their defenses against DDoS attacks and minimize the impact on their networks, systems, and operations.
Can DDoS attacks cause permanent damage In most cases, DDoS attacks do not cause permanent damage to a target’s infrastructure or systems. Once the attack subsides and normal traffic is restored, the systems generally resume their normal functioning. However, there can be indirect damage caused by DDoS attacks, such as reputational damage, loss of business, or disruption to critical services. It is important for organizations to have proper mitigation measures in place to minimize the impact and recover quickly from such attacks.
Can Windows Firewall block DDoS attack
Block DDos attacks are impossible via Windows firewall and also Hardware firewalls. You can't really block DDoS attacks just with your firewall. It's a start, especially firewalls that block botnets. But if the DDoS attack is targeted at you, at some point your firewall will just fail.
How can DDoS attacks be stopped
Reroute traffic through firewalls or add device firewalls to block attacks. Apply stronger rate limits to firewalls, servers, and other resources protecting and servicing the router or server. Add or strengthen network security products, network intrusion detection systems (IDS), and intrusion prevention systems (IPS).
How does firewall detect DDoS attack
Web scanners, web application firewall (WAF), and traffic anomaly DDoS attack detection tools can help reduce damage and traffic profiling. Web scanners monitor web applications regularly, especially after an attack, while WAF filters traffic using machine learning algorithms.
Can stateful firewall prevent DDoS
Deployed on-premises, in front of the firewall and using stateless packet processing technology, AED can stop all types of DDoS attacks – especially state exhaustion attacks that threat the availability of the firewall and other stateful devices behind it.
Why can’t firewall stop DDoS attack
Firewalls and IPS Cannot Distinguish between Malicious and Legitimate Users. Certain DDoS attack vectors such as HTTP/HTTPS floods, are composed of millions of legitimate sessions. Each session on its own is legitimate and it cannot be marked as a threat by firewalls and IPS.
What attacks can’t be defended by the firewalls
Social engineering is a kind of cyber threat that firewalls cannot prevent. Social engineering attacks include a broad range of attacks involving human interaction which overpasses firewalls. Social engineering's goal is to trick end-users into making a security blunder, such as giving away login credentials.
Can a DDoS be permanent
Transient denial-of-service DOS attacks occur when a malicious perpetrator chooses to prevent regular users contacting a machine or network for its intended purpose. The effect may be temporary, or indefinite depending on what they want to get back for their effort.
Why is it so hard to stop DDoS
During a DDoS attack, that can be thousands of constantly changing IPs and millions of packets of data to keep track of in state tables. The memory and processing resources required to do that quickly for every packet is enormous and most firewalls simply can't handle the load.
What attacks does a firewall stop
Firewalls protect your network from unauthorized access by hackers who use a variety of tools to gain entry such as viruses, backdoors, denial-of-service (DoS) attacks, macros, remote logins, phishing emails, social engineering, and spam.
What attacks do firewalls prevent
A firewall safeguards your PC against harmful data by filtering them out of the system. It protects against backdoors, denial-of-service attacks, macros, remote logins, spam, and viruses.
What do firewalls not protect against
Firewalls do not guarantee that your computer will not be attacked. Firewalls primarily help protect against malicious traffic, not against malicious programs (i.e., malware), and may not protect you if you accidentally install or run malware on your computer.
Is a firewall better than anti DDoS
Does a Firewall Protect Against DDoS Attacks Users often associate the concept of a “firewall” with comprehensive protection. However, having a firewall does not really guarantee protection against DDoS, because in addition to traffic processing policy, specialized settings and multiple layers of filters are required.
Can hackers get past firewalls
A firewall may be secure, but if it's protecting an application or operating system with vulnerabilities, a hacker can easily bypass it. There are countless examples of software vulnerabilities that hackers can exploit to bypass the firewall.
Will a firewall stop hackers
A firewall is a crucial security feature that helps to protect your computer or network from external threats such as hackers and malware. However, despite its effectiveness, there are several ways in which a firewall can be breached and leave your system vulnerable to attacks.
Can you go to jail if you DDoS someone
The use of booter and stresser services to conduct a DDoS attack is punishable under the Computer Fraud and Abuse Act (18 U.S.C. § 1030), and may result in any one or a combination of the following consequences: Seizure of computers and other electronic devices. Arrest and criminal prosecution.
How long does a DDoS usually last
Depending on the severity of the attack, DDoS attacks can last up to a day or more. But with robust planning and good security partners, you can usually manage small to mid-sized attacks in a matter of hours or minutes.
Can a firewall stop a hacker
A firewall is a crucial security feature that helps to protect your computer or network from external threats such as hackers and malware. However, despite its effectiveness, there are several ways in which a firewall can be breached and leave your system vulnerable to attacks.
What are the 3 main advantages of using firewalls
Firewalls serve as a first line of defense to external threats, malware, and hackers trying to gain access to your data and systems.Monitors Network Traffic. All of the benefits of firewall security start with the ability to monitor network traffic.Stops Virus Attacks.Prevents Hacking.Stops Spyware.Promotes Privacy.
Do firewalls stop hackers
A firewall is a crucial security feature that helps to protect your computer or network from external threats such as hackers and malware. However, despite its effectiveness, there are several ways in which a firewall can be breached and leave your system vulnerable to attacks.
What firewalls Cannot do
Users not going through the firewall: A firewall can only restrict connections that go through it. It cannot protect you from people who can go around the firewall, for example, through a dial-up server behind the firewall. It also cannot prevent an internal intruder from hacking an internal system.
How long does a DDoS last
This type of sporadic attack can vary in length, from short-term actions that last for a few minutes to longer strikes that exceed an hour. According to the DDoS Threat Landscape Report 2021 from Swedish telecom Telia Carrier, documented attacks average a 10-minute duration.
What is the punishment for DDoS in USA
The use of booter and stresser services to conduct a DDoS attack is punishable under the Computer Fraud and Abuse Act (18 U.S.C. § 1030), and may result in any one or a combination of the following consequences: Seizure of computers and other electronic devices. Arrest and criminal prosecution.
Can you go to jail for DDoS
The use of booter and stresser services to conduct a DDoS attack is punishable under the Computer Fraud and Abuse Act (18 U.S.C. § 1030), and may result in any one or a combination of the following consequences: Seizure of computers and other electronic devices. Arrest and criminal prosecution.
What are the weakness of firewall
The weaknesses of a firewall: An inability to fend off attacks from within the system that it is meant to protect. This could take the form of people granting unauthorized access to other users within the network or social engineering assaults or even an authorized user intent on malafide use of the network.
Is DDoS a serious crime
The use of booter and stresser services to conduct a DDoS attack is punishable under the Computer Fraud and Abuse Act (18 U.S.C. § 1030), and may result in any one or a combination of the following consequences: Seizure of computers and other electronic devices. Arrest and criminal prosecution.